Justin Sherman
Introduction
Much of the security commentariat has lately focused the global Internet security conversation on communications technologies deemed “emerging,” such as cloud computing infrastructure, new satellite technology, and 5G telecommunications. However, the vast majority of international traffic traversing the Internet each day, from video calls to banking transactions to military secrets, travels over a much older and far less flashy technology: undersea cables.1 These cables, which lay along the ocean floor and haul data intercontinentally, have been developed for 180 years by private sector firms and international consortia of companies. In recent years, large Internet companies (e.g., Facebook, Google) have gained significant ownership in these cables. Chinese state-owned firms have also greatly increased both their construction (e.g., Huawei Marine) and ownership (e.g., China Telecom, China Unicom) of undersea cables in recent years.
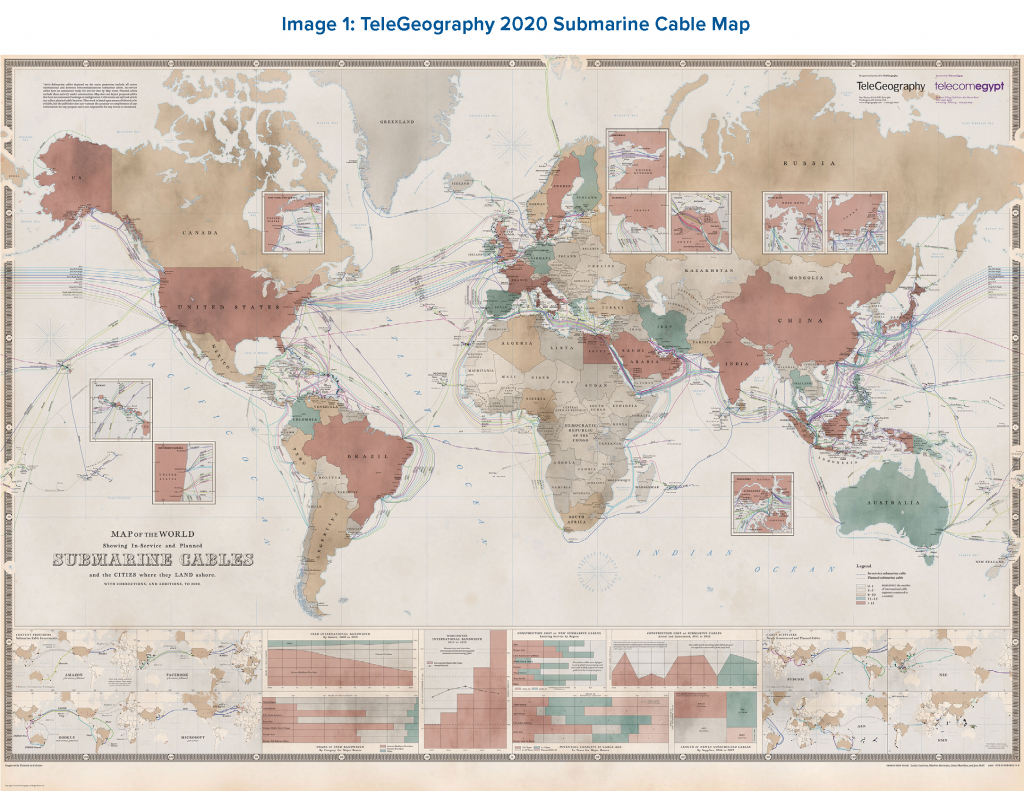 Source: Jayne Miller, “The 2020 Cable Map Has Landed,” TeleGeography Blog,
Source: Jayne Miller, “The 2020 Cable Map Has Landed,” TeleGeography Blog,
The undersea cables that carry Internet traffic around the world are an understudied and often underappreciated element of modern Internet geopolitics, security, and resilience. It is estimated that upwards of 95 percent of intercontinental Internet traffic is carried over these cables.2 Without them, the Internet would not exist as it does today. These cables are largely owned by private companies, often in partnership with one another, though some firms involved in cable management are state-controlled or intergovernmental. Submarine cables are, therefore, a major vector of influence that companies have on the global Internet’s shape, behavior, and security.3
 The Deterrence Theory was developed in the 1950s, mainly to address new strategic challenges posed by nuclear weapons from the Cold War nuclear scenario. During the Cold War, the U.S. and the Soviet Union adopted a survivable nuclear force to present a ‘credible’ deterrent that maintained the ‘uncertainty’ inherent in a strategic balance as understood through the accepted theories of major theorists like Bernard Brodie, Herman Kahn, and Thomas Schelling.1 Nuclear deterrence was the art of convincing the enemy not to take a specific action by threatening it with an extreme punishment or an unacceptable failure.
The Deterrence Theory was developed in the 1950s, mainly to address new strategic challenges posed by nuclear weapons from the Cold War nuclear scenario. During the Cold War, the U.S. and the Soviet Union adopted a survivable nuclear force to present a ‘credible’ deterrent that maintained the ‘uncertainty’ inherent in a strategic balance as understood through the accepted theories of major theorists like Bernard Brodie, Herman Kahn, and Thomas Schelling.1 Nuclear deterrence was the art of convincing the enemy not to take a specific action by threatening it with an extreme punishment or an unacceptable failure.



















