Yehoshua Kalisky

The laser is a unique light source for many and varied uses in a wide range of intensities. The prominent advantage of the laser is its ability to produce and concentrate an energetic light beam across a defined target, moving at the speed of light over a large range and heating of the target shell to the point of structural failure. Jeff Hecht (2019) reviewed the race to develop powerful laser-based weapon systems. As a result of Hecht’s review, the opinion was formed that a high-power laser system, combined with kinetic systems and a variety of suitable optical and electro-optical systems, could be used to strike and neutralize air threats in possession of Israel’s enemies – missiles, rockets, mortar shells (drones), unmanned small craft, unmanned aerial vehicles (such as UAVs) or skimmers. Today, the opponents operating these means of flight have advantages due to the simplicity of operation and the relatively low cost, which allows them to cause a lot of damage, disrupt normal life, and sow terror. A high-power laser-based weapon is one of the necessary layers to defend against these threats (Kalisky, 2007).
Types of Lasers
Laser-based weapons have a number of significant advantages: They enable accurate, continuous, high-power, light-speed interception with both minimal cost and logistics compared to kinetic missile interception. In addition, laser power can be controlled according to the type of target, without the need to “load an ammunition cartridge,” since the laser is a non-biodegradable system. The limitations of laser operation are mainly environmental – limited activity in clouds, haze, and rain as well as limited range of action due to atmospheric attenuation caused by the absorption of laser radiation by various water vapors or gases in the atmosphere. In addition, there must be a straight line between the laser and the target, since the movement of light is in a straight line, and the beam must stay on the target to cause the required damage.
When distinguishing between laser for tactical applications and laser for strategic applications, the required capacities are derived from this definition: Tactical laser, hereinafter referred to as kW-class lasers, is used to destroy short- and medium-range rockets, shells such as UAVs, skimmers, and light ships. The required power is around 100–150 kilowatts. It only takes 30 millionths of a second for a laser beam to reach a target that is 10 km away.
Lasers for strategic applications are used to destroy long-range missiles (hundreds and thousands of kilometers), the required power is 1–2 megawatts, and accordingly they are called MW-class lasers. It is important to know that depending on the amount of power required, the laser can be portable by land or air or can remain stationary.
Chemical Lasers
Historically, developments in the 1970s and 1980s focused on powerful strategic lasers – MW-class lasers – to neutralize and destroy ballistic missiles carrying nuclear warheads. The source for producing laser radiation of this magnitude are chemical lasers. These are lasers based on a mixture of gases, such as hydrogen or deuterium, together with fluorine or its derivatives as the active medium, with the heat generated from the chemical reaction between the fluorine atoms and the hydrogen or deuterium atoms causing processes leading to powerful laser radiation in the infrared domains. This development took place mainly in the United States, the Soviet Union, China, and the United Kingdom, and was significantly accelerated after the “Star Wars” speech of then US president, Ronald Reagan, on March 23, 1983. In this context, chemical laser systems “Nautilus” and “Skyguard” were developed in cooperation with Israel to intercept missiles, rockets, and shrapnel, which showed initial feasibility as early as 1996 in destroying short-range rockets and shells. Later, improved models of hydrogen or deuterium fluoride-based chemical lasers were developed for tactical purposes, i.e., power supplies up to 100 kilowatts and even chemical lasers based on a chemical reaction between oxygen and iodine in various configurations (stationary, portable or airborne), which have proven feasibility in destroying targets. In parallel with this activity, a chemical oxygen iodine laser was designed, assembled, and activated at 1–2 megawatts, carried on an airborne laser (ABL) Boeing 747. In field trials, the airborne laser performed two successful ballistic missile interceptions at the acceleration stage and at a distance of 400 km, but in 2011 the project was closed for economic reasons and poor performance evaluation.
Solid-State Lasers and Fiber Lasers
The US as well as Russia, Germany, and China have significantly developed solid-state lasers and fiber optic-based lasers since the late 1990s and accelerating in 2000–2010. During these years, solid-state laser and fiber laser systems were developed in various geometric configurations and in combination of a chain of optical amplifiers to increase the laser power. In addition, significant progress has been made in the development of high-power diode lasers, which are used to stimulate the crystal laser or optical fiber (Kalisky, 2013). At the same time, a significant breakthrough occurred in the development and production of unique optical fibers for producing laser beams, high-power-resistant optical components, cooling and heat removal systems, optical systems for the correction of atmospheric distortions, and methods for unifying rays. Unlike chemical lasers, solid-state lasers or fiber lasers produce intense power by combining several low-power beams into one high-power beam. The currently accepted combination is Coherent Beam Combining (CBC) and is done by coordinating the phases of the different beams so that they are all in the same phase – i.e., the peaks of the different light waves appear at the same time and increase the power produced by the system, as shown in Figure 1.
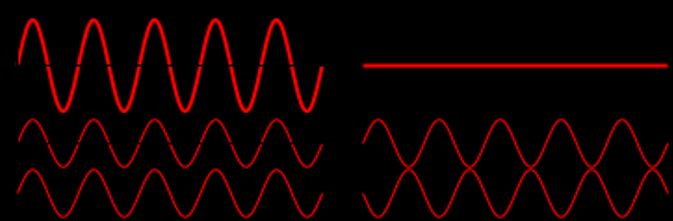
Figure 1. Non-phase beams (right) and unified phase beams (left)
Fiber lasers have additional advantages over solid-state lasers: efficient heat dissipation due to the large surface area, the considerable increase of laser radiation due to the length of the fiber, 50% lower power consumption than solid-state lasers, flexibility in assembly and operation, compactness and therefore the possibility of a terrestrial and aerial platform. Despite a number of shortcomings, especially in the optical field, high-fiber laser technology is considered “mature” and very promising.
The performance status for the various systems (solid-state lasers and fiber lasers) is currently 100 kilowatts, with an average efficiency of 30% with the expectation of receiving power of up to 400 kilowatts in 2024 with an efficiency of 30–50%. Powerful solid-state lasers – Laser Weapon System (LaWS) – in the range of 15–50 kilowatts (Fig. 2), that were developed by various bodies have demonstrated impressive operational feasibility in field interception experiments as UAVs and unmanned vessels and have been in operational service since 2014 in the Persian Gulf on the USS Ponce and on the USS Portland. This laser also intercepted a cruise missile in the White Sands Experimental Field, New Mexico. In terms of weight and volume estimation, today a solid-state laser system of 100 kilowatts weighs about 3 tons and has a total volume of 7,400 liters. The aim is to reach a system that weighs 500 kg, with a volume of 700 liters and an overall efficiency of 30% (Titterton, 2015: 255–256).

Conclusion
A high-power laser beam is a technologically complex electromagnetic weapon system, belonging to a generation of directed energy weapons. It has many advantages in terms of low cost, unlimited firing, minimal logistics, infinite reaction speed (relative to the target), and the ability to hit points within moving ranges depending on the type of laser and its location either on land or at high altitude. This weapon, however, also has environmental operating limitations and a limited range. The laser system is supposed to integrate and complete the Iron Dome system and provide an optimal protective shell for the State of Israel. The importance of Israel’s national security is reflected in the words of Prime Minister Naftali Bennett, in a speech at the International Conference of the Institute for National Security Studies held in February 2022, that within a year the IDF will operate a “blue and white” laser interception system.