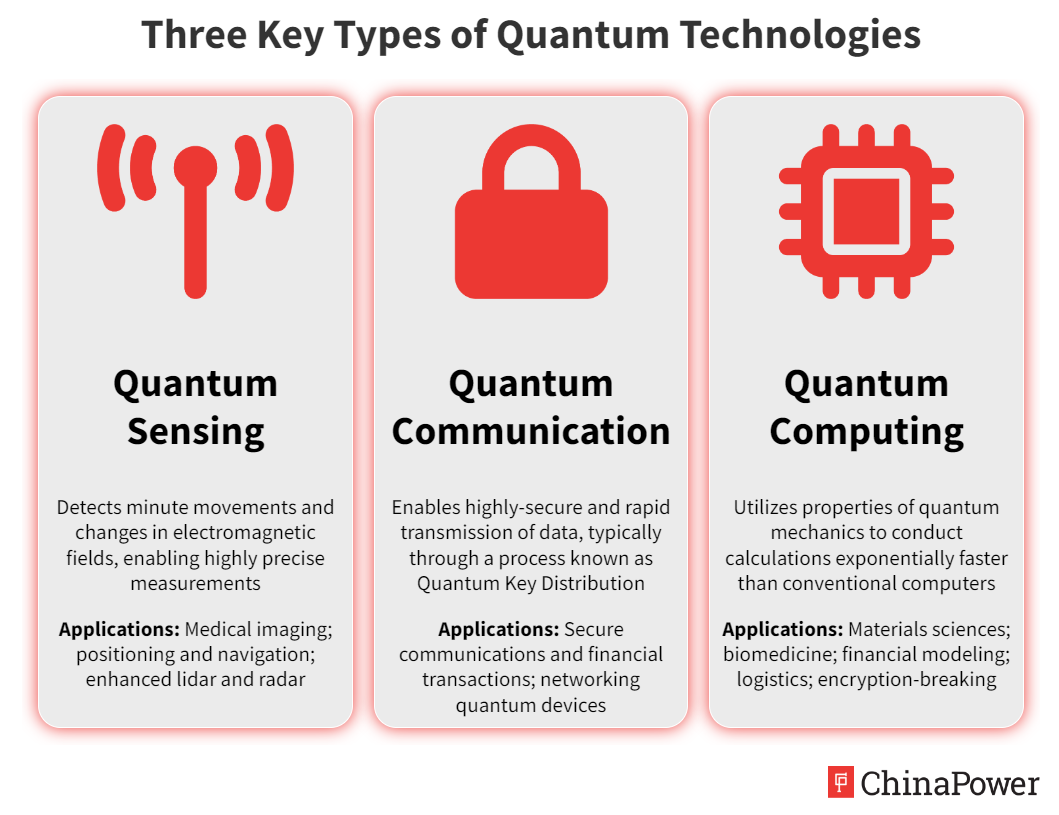
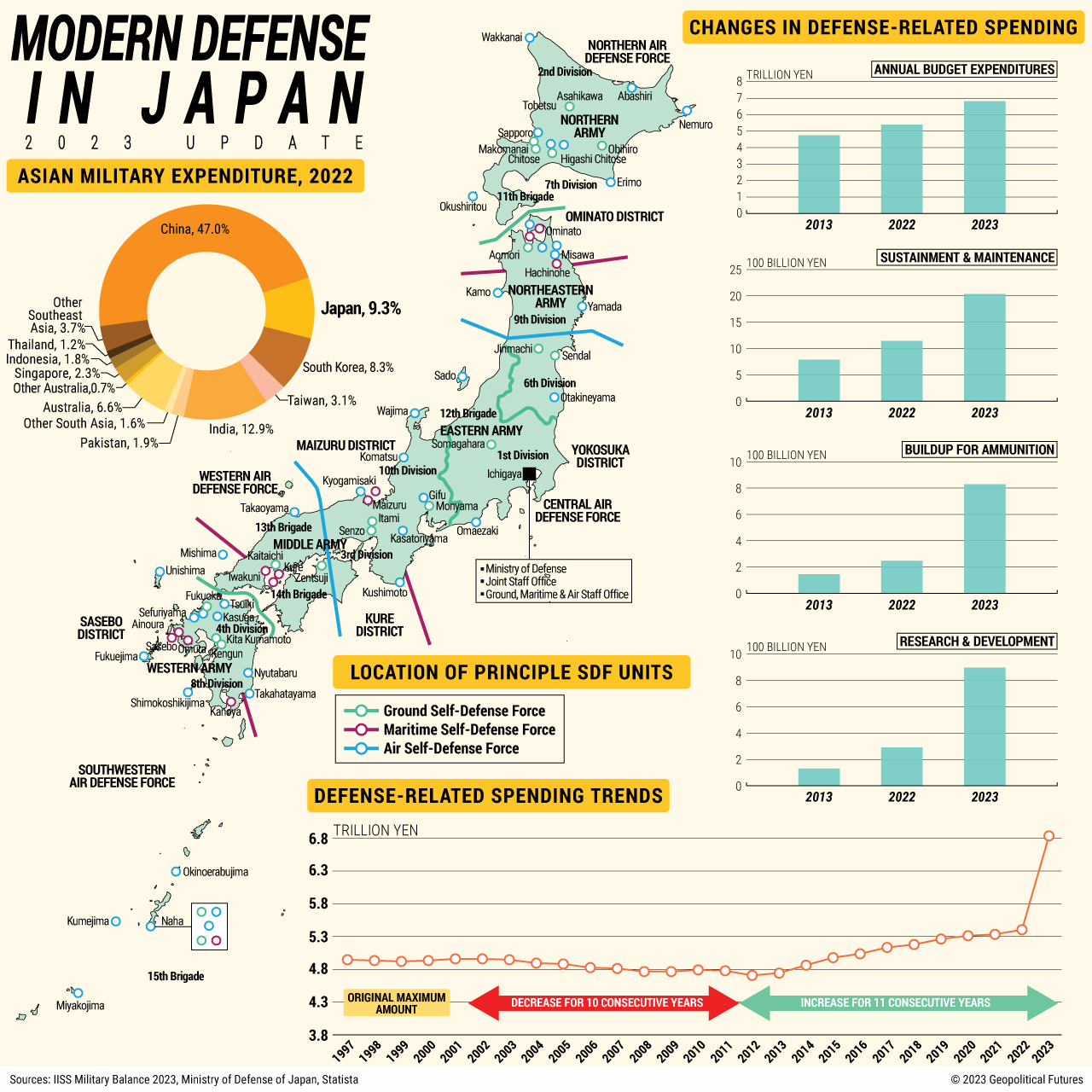
Nasir Andisha
This month marks the second anniversary of the withdrawal of US forces from Afghanistan and the Taliban’s military takeover of the country. The devastating images of Kabul in mid-August 2021 depicting despair, chaos, and abandonment are still vivid in our memories. These images also symbolized the collapse of democracy in Afghanistan. Despite evident shortcomings, this democratic state, for which I served as deputy foreign minister from 2015 to 2019, unleashed an unprecedented era of socioeconomic progress in Afghanistan’s history.
For the majority of Afghanistan’s new generation—those who worked, fought, and aspired for a free, democratic, and prosperous country—it has been a harrowing two years. It has been two long years of processing grief and overcoming the anguish of abandonment and collapse, but also two years of engaging in self-reflection, reorganization, and resistance.
The country is in a deep crisis; the status quo is not sustainable. The challenges ahead are enormous and multidimensional, but all is not lost. Afghanistan’s most precious asset, developed over the past two decades, is its professional and well-connected youth. More than 60 percent of Afghanistan’s population is under the age of twenty-five. The burden of resolving this crisis by spotting and exploiting opportunities amid this calamity falls on this generation. They are slowly but surely rising to the task.
The challenges ahead are indeed colossal. Afghanistan faces a deeply divided society, a demoralized elite, a broken economy, an exhausted civil society, and an extremist ethnoreligious group in control of the country. The Taliban reneged on the promises they made during the Doha negotiation process to form an inclusive government and provide women and girls with access to education. Instating exclusively male and essentially Pashtun mullahs, they failed to gain domestic and international legitimacy. They continue to impose draconian and regressive laws, which are pushing the country into a downward spiral in every socioeconomic, human-rights, and fundamental-freedoms index. After systematically erasing women and girls from public life, the Taliban administration is on the brink of being designated as a gender apartheid regime by United Nations–appointed rights experts. Its symbiotic relations with foreign terrorist groups, drug production and trafficking, and systematic promotion of violent extremist ideology pose imminent threats to the immediate region and beyond.