Tips from defense companies to a Pentagon office that monitors contractor security and protects classified data led to the arrest this month of three people accused of shipping sensitive microelectronics to Russia, according to the program’s director.
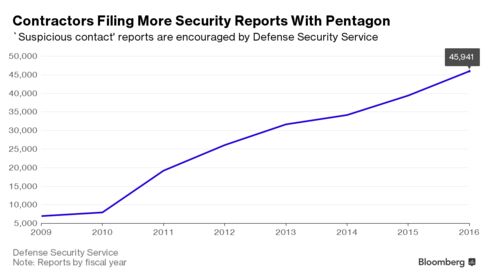
The five “suspicious contact” reports to the Defense Security Service in that case were among 45,941 submitted by industry in the fiscal year that ended Sept. 30, director Dan Payne said in an interview. Of the reported contacts, 19 percent resulted in solid counter-intelligence reports, Payne said.
The Russian case underscored what Payne described as the most attempts to steal, purchase or otherwise obtain sensitive U.S. technology uncovered during his 34 years of counter-intelligence work, which included years at the Central Intelligence Agency.
The 45,941 reports from industry last year was up from 7,002 reports in fiscal 2009 and 39,442 in fiscal 2015, according to agency figures. The reports led to 1,117 active intelligence community investigations or leads of counterintelligence cases and export control violations, Payne said.
“We are in a knife fight” with adversaries, Payne told a panel sponsored by Bloomberg Government last week on supply-chain security. He said in the interview that his message was “we can’t do it all” in government so “we almost have to have a unified front” with industry. “Thus far, industry has been very good with the reporting.”
The Justice Department said in a statement Oct. 6 that three people representing two Russian-affiliated front companies based in Brooklyn, New York, were arrested for buying and then shipping sensitive equipment to Russia. The department alleged that a naturalized U.S. citizen from Russia living in Brooklyn conspired with two Russian nationals based in Denver to ship microelectronics “used in a wide variety of military systems, including radar, and surveillance systems, missile guidance systems and satellites.”
The perpetrators were going to U.S. companies “for radiation-hardened microchips,” Payne said. “The companies came to us and said, ‘Hey look, we are getting inquiries from this company. Something’s not right.”’
He said methods used to obtain sensitive U.S. technology have included purchasing businesses to obtain technology, and requesting academic research.
“Information by the gigabyte” is “heading out the door,” Payne said. “Technologically, Russia is probably the best there is” at technology theft and transfer. “Their trade-craft is very good.”
No comments:
Post a Comment