By Austin Hale and Frank G Hoffman
Would a future US-China conflict in Asia pit the US AirSea Battle concept – now referred to as the Joint Concept for Access and Maneuver in the Global Commons – against China’s anti-access/area-denial (A2/AD) capabilities? While this characterization may be too symmetrical for its own good, Frank Hoffman and Austin Hale believe Beijing’s capabilities represent a decisive, asymmetric, and long-term threat to US interests in the region.
China appears determined to assert itself throughout the Asia Pacific region and undercut United States’ alliances with potentially destabilizing effects on regional security.[1] Its increasingly aggressive actions in the Western Pacific, coupled with rising defense spending—an increase of 7.6 percent in 2016—have elevated the possibility of conflict between the United States and China.[2] Thus, U.S. analysts and defense scholars have been trying to identify the potential form a future conflict between the two powers may take. In the available literature, this potential conflict is characterized and operationalized as a competition between the U.S. AirSea Battle (ASB) operational concept—now referred to as the Joint Concept for Access and Maneuver in the Global Commons—and China’s Anti-access/Area-denial (A2/AD) capabilities.[3]
In their recent article, “Future Warfare in the Western Pacific,” in International Security, defense scholars Stephen Biddle and Ivan Oerlich argue that while advancements in reconnaissance, surveillance, and target acquisition (RSTA) have allowed China to field more advanced sensor, guidance, and communication technologies, the Chinese A2/AD approach is not a decisive, long-term threat to the United States or its allies in the region.[4] This conclusion would suggest that the U.S. Defense establishment need not concern itself with this challenge, undercutting its emphasis in recent Pentagon publications, such as the Quadrennial Defense Reviews and the Pentagon’s emerging Offset Strategies narrative.[5]
We contend that Chinese A2/AD capabilities are more asymmetric than Biddle and Oerlich presented and can be a decisive long-term threat to the interests of the U.S. and its allies in the region. Furthermore, a mature A2/AD system would allow China to project power throughout the region largely unchecked. Underestimating developments to extend and diversify Chinese intelligence and targeting assets could lead to erroneous conclusions and strategic failure.
Biddle and Oerlich base much of their argument on the belief that “it will be especially difficult for China . . . to extend A2/AD’s reach beyond about 400-600km from a friendly coast.”[6] The authors identify this restriction because they conclude that airborne radars, such as advanced Airborne Early Warning and Control (AEWC) systems, cannot safely deploy beyond the reach of land-based air defense systems. Thus, A2/AD must rely on active radar for targeting, which in turn is restricted by the Earth’s curvature and the physical horizon of 400-600km from the coast of the Mainland.[7] Furthermore, they conclude that “only radar can provide the broad-area, day-night, long-range detection essential for A2/AD.”[8] In support of this claim, the authors systematically assess the viability of alternatives to radar for A2/AD systems. Concerning ground-based over-the-horizon (OTH) radar, while admitting that it can detect targets beyond the physical horizon, the authors’ maintain that it cannot extend the range of A2/AD because it operates at frequencies unsuitable for target acquisition.
In regards to space-based assets, the authors posit that the vulnerability of satellites precludes them from providing the necessary RSTA capability to extend the reach of A2/AD. Satellites travel in predictable orbits making them easy targets for ground-based antisatellite (ASAT) weapons. Furthermore, defending a satellite is impractical due to the large cost associated with equipping satellites with defensive capabilities or with the fuel needed to complete evasive maneuvers. Given these inherent vulnerabilities, the authors conclude that either side’s satellites could easily be destroyed at the outbreak of conflict and therefore cannot be relied upon to direct A2/AD systems.[9]
They also note that passive alternatives to radar, such as signals intervention and passive visible or infrared light detection, are also unreliable due to their ineffectiveness in poor weather conditions.[10]While drones, aircraft, and satellites can listen passively for ship radio transmissions in order to triangulate their position, tactics such as low-probability-of-intercept techniques and strict electronic emissions control (EMCON) can be used to substantially decrease detection rates and ranges. Passive infrared sensors require perfect weather conditions to be effective and advancements in infrared shielding make identifying targets particularly difficult.[11]
Biddle and Oerlich also suggest that sea-based assets, such as submarines and mines, would not be able to extend A2/AD’s range. For submarines, this limit is due to the fact that in order to “operate in distant waters under hostile control, submarines must . . . use onboard sonars and operate near the targets they would engage.”[12] Consequently, submarines are forced into a defined area in which anti-submarine warfare (ASW) can be more effective. Mines, on the other hand, are fixed in place and have relatively short ranges. Therefore, to successfully extend A2/AD’s reach, they must be employed in extremely large numbers throughout large swaths of open ocean—a task unaffordable and impractical for any navy.[13]
Based on this assessment of the strengths and limitations of A2/AD, the authors conclude that “[Chinese] A2/AD is not a decisive long-term threat to most U.S. allies in the region,” so the United States need not incur the investment costs or risks associated with pursuing the strike-centric AirSea Battle concept.[14]
Counterarguments
However, should the U.S. heed Biddle and Oerlich’s advice, the net result will be a system of “competing spheres of influence in the Western Pacific; a Chinese sphere over its mainland; a U.S. sphere over most of its allies’ landmasses and including most of the regions disputed island chains; and zone of mutual exclusion in between in which neither side enjoys freedom of movement”—an outcome the authors claim is acceptable.[15] However, this outcome is neither acceptable nor likely! In fact, the authors seriously underestimate the potential of A2/AD and the danger it poses to the U.S and its allies.
First, China is not nearly as dependent upon space-based assets that might be easily taken out at the initiation of a conflict as the United States is. As of January 2015, the Chinese government and the People’s Liberation Army (PLA) had a combined total of 115 operational satellites—37 for intelligence, surveillance, and reconnaissance (ISR) and remote sensing, 15 for navigation, 12 for communication, 28 for earth observation, and 23 for space sciences and technology development. At the same time, the U.S. government and military operated 287 satellites—45 for ISR, 36 for navigation, 122 for communication, 32 for earth observation, and 52 for space sciences and technology development.[16]These numbers clearly indicate the United States is more reliant on space-based assets than China. Thus, we conclude that even if the United States was willing and able to destroy China’s space-based assets, there is no reason to suspect that such an attack would severely limit China’s A2/AD capabilities.
Second, the authors’ do not credit the possibility that A2/AD systems—including advanced radar systems, such as High-Frequency (HF) radar and Airborne Early Warning and Control (AEWC) platforms (manned or unmanned)—could be deployed from disputed islands in the South and East China Seas and protected by land-based air defenses significantly extending the range of A2/AD’s warning and strike capabilities (see Table 1).[17] For example, HF radar, with ranges between 80-200 miles, could either target enemy assets directly if the selected weapons system is capable of localizing and pursuing a target, or it could provide cueing to AEWC assets to gather targeting information.[18]
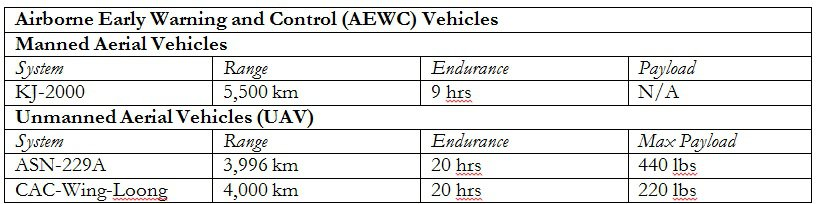
Table 1: Chinese AEWC platforms[19]
Additionally, the deployment of HQ-9 surface-to-air missiles and YJ-62 anti-ship cruise missiles—both of which are already positioned on Woody Island—to the Fiery Cross, Subi, and Mischief Reefs would provide overlapping SAM coverage, as well as ASCM coverage over most of the South China Sea (see Figure 1).[20]
Such a configuration would allow AEWC platforms to be deployed within the defensive reach of air defense systems, such as the HQ-9, extending AEWCs radar range to 600-900km of the controlled landmass.[21] In turn, these systems could be used by the PLA to cue the launch and trajectory of a DF-21 D medium-range ballistic missile, known as the “carrier killer,” preventing foreign militaries from intervening in the Western Pacific. A CJ-10 land-attack cruise missile, in theory, would allow China to strike U.S. or allied military assets from Singapore to the Philippines (see Figure 1).[22]
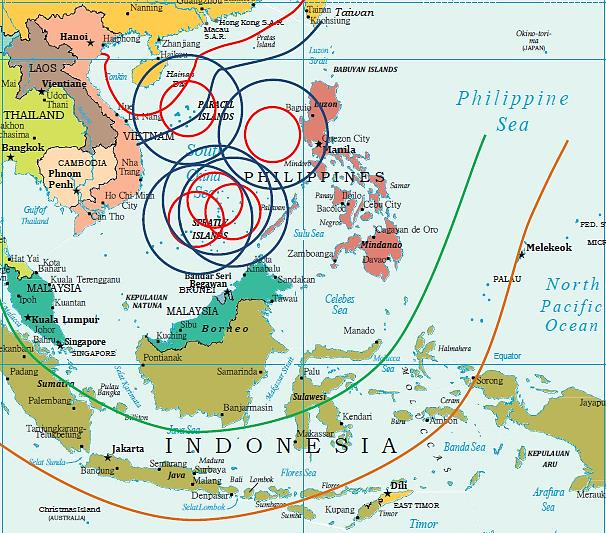
Figure 1: Potential range of HQ-9 SAM (200km), YJ-62 ASCM (400km), DF-21 MRBM (1,550km) and CJ-10 LACM (2,200km) when placed on disputed islands in the South China Sea (Fiery Cross Reef, Subi Reef, Mischief Reef and Scarborough Shoal), Woody Island, and along China’s coast.[23]
Biddle and Oerlich’s suggestion that the curvature of the earth limits the ability of China to identify, track, target, and strike U.S. forces in a crisis appears to ignore this constellation of ISR sources. As suggested in Figure 1, China is capable of creating a dense, redundant system of mutually reinforcing ISR and strike systems that gives it a significant anti-access capability. Furthermore, this more dispersed network of systems would be more resilient and harder to target in the initial stages of a crisis. These assets, especially the DF-21, threaten to push the United States Navy beyond the range of its carrier wings and surface warships and beyond the range of their LACMs, limiting the Navy’s ability to project power over or near Mainland China.[24] We are not saying that these operational capabilities cannot be overcome, but they should not be underestimated.
Third, Biddle and Oerlich do not recognize the role China’s maritime militia, dubbed China’s “little blue men,” could play in covering any gaps in China’s ISR coverage.[25] Maritime militia forces have allowed China to disrupt foreign survey operations and to extend and consolidate areas it views as Chinese territory with low escalatory risks.[26] While these actions can hardly be identified as military actions, during a conflict with the U.S., these forces could easily provide early warning, tactical intelligence, and targeting information to the PLA. China also maintains a massive, nationally owned fleet of commercial shipping vessels, fishing vessels, and non-military maritime resources that could easily be exploited as a highly distributed, maritime intelligence system.[27] The advent of multiple satellite-based precision navigation systems (GPS, BeiDou, GAGAN and GLONASS) could enable these forces to provide targeting information precise enough to support an attack by a weapon with its own localization seeker and maneuverability.[28]
Moreover, during peace-time, the maritime militia could extend the PLA’s eyes well out into the South China Sea and beyond, significantly increasing the range of China’s A2/AD systems in the region. While their survivability, and therefore their reliability, is certainly tenuous during a shooting war, the sheer size of the fishing fleet—nearly 200,000 marine fishing vessels and 2,460 distant-water (beyond China’s EEZ)—ensures that China could continually exploit this resource even while taking heavy casualties.[29]
Finally, Biddle and Oerlich do not acknowledge that the PLA could exploit networks that link their military resources better than we imagine today. According to China’s 2015 Defense White Paper, the PLA is committed to further force integration, stating that the armed forces will “establish an integrated joint operational system . . . construct a combat force structure for joint operations . . . enhance joint operational capabilities . . . establish an integrated joint operational system . . . and improve the CMC [Central Military Commission] command organ and theater-level command systems for joint operations.”[30] Further integration of PLA military resources could allow China to significantly expand its A2/AD capabilities. For instance, OTH radar could detect targets as far away as 3,000km and provide cueing to space-based assets or AEWC platforms to gather targeting information. In turn, these systems could cue the launch and guide the trajectory of CJ-10 or DF-21 D missiles to the selected target.
A Long-Term Threat
In the long-term, a fully mature Chinese A2/AD system could be a major threat to the United States and its allies in the region. Given the likelihood that China will place anti-access weapons systems and advance radar systems on disputed islands in the South China Sea, the potential exists for it to threaten U.S. assets from Singapore to the eastern shores of the Philippines. This more ambiguous, decentralized network is very distributed and resilient, but also more vulnerable. Underestimating the PLA’s A2/AD capabilities could lead the United States to suffer from strategic surprise should any conflict break out in the region. We do not need to obsess on the problem, but this operational challenge has strategic implications. Additionally, this is a larger challenge than just the Western Pacific, given that other regional powers also employ capabilities that could restrict operational freedom of maneuver in the North Atlantic, Baltic Sea, and Persian Gulf as well. Thus, it is important that the U.S. continues to develop the means necessary to counteract efforts to contest access in the global commons.
Notes
[1] Bernard Cole, The Great Wall at Sea: China Enters the Twenty-first Century (Annapolis, MD: Naval Institute Press, 2014), 2d ed.; Toshi Yoshihara and James R. Holmes, Red Star over the Pacific: China’s Rise and the Challenge to US Maritime Strategy, (Annapolis, MD: Naval Institute Press, 2010); Patrick Cronin, et al, Cooperation from Strength: The United States, China and the South China Sea (Washington, DC: Center for a New American Century, 2012); Xu Hui and Cao Xianyu, “A Perspective on China’s Maritime Security Strategy,” in Routledge Handbook of Naval Strategy and Security, Joachim Krause and Sebastian Bruns, eds. (Oxon, UK: Routledge, 2016); and Phillip Saunders, Director, Center for the Study of Chinese Military Affairs, NDU, personal e-mail correspondence, October 15, 2016.
[2] Chris Buckley and Jane Perlez, “China Military Budget to Rise Less Than 8%, Slower Than Usual,” New York Times, March 4, 2016, available at http://www.nytimes.com/2016/03/05/world/asia/china-military-spending.html?_r=0.
[3] For an overview of the debate generated by AirSea Battle, see Aaron Friedberg, Beyond Air-Sea Battle, The Debate Over US Military Strategy in Asia (London: International Institute of Strategic Studies, 2014). For a summary of postulated PLA A2/AD operations, see Jan Van Tol, Mark Gunzinger, Andrew Krepinevich, and Jim Thomas, “AirSea Battle: A Point-of-Departure Operational Concept,” Washington, DC: Center for Strategic and Budgetary Assessments, 2010, 17-47.
[4] Stephen Biddle and Ivan Oerlich, “Future Warfare in the Western Pacific,” International Security, Vol. 41, No. 1 (Summer 2016), 13.
[5] Robert M. Gates, The Quadrennial Defense Review Report 2010(Washington, DC: Department of Defense, February 2010); Chuck Hagel, The Quadrennial Defense Review (Washington, DC: Department of Defense, March 2014). On the Defense Department’s key innovation initiatives, see Robert Work, Prepared Remarks, “The Third Offset Strategy,” at the Ronald Reagan Defense Forum, Nov. 17, 2015, accessed at http://www.defense.gov/News/Speeches/Speech-View/Article/628246/reagan-defense-forum-the-third-offset-strategy.
[6] Biddle and Oerlich, “Future Warfare in the Western Pacific,” 13.
[7] Ibid., 13.
[8] Ibid., 23.
[9] Biddle and Oerlich, “Future Warfare in the Western Pacific,” 25–26.
[10] Ibid., 23.
[11] Ibid., 29-30.
[12] Ibid., 30-31.
[13] Ibid., 32.
[14] Ibid., 13, 41.
[15] Ibid., 43.
[16] Eric Heginbotham et al., The U.S.-China Military Scorecard: Forces, Geography, and the Evolving Balance of Power, 1996–2017 (Santa Monica, CA: RAND Corporation, 2015), 229–231, http://www.rand.org/pubs/research_reports/RR392.html; USNI News, “New Possible Chinese Radar Installation on SCS Artificial Island Could Put US Stealth Aircraft at Risk,” Feb. 2, 2016, https://news.usni.org/2016/02/22/new-possible-chinese-radar-installation-on-south-china-sea-artificial-island-could-put-u-s-allied-stealth-aircraft-at-risk.
[17] Ankit Panda, “South China Sea: China’s Surveillance Drones Make it to Woody Island,” The Diplomat, June 1, 2016, http://thediplomat.com/2016/06/south-china-sea-chinas-surveillance-drones-make-it-to-woody-island/; Victor Robert Lee, “South China Sea: Satellite Imagery Shows China’s Buildup on Fiery Cross Reef,” The Diplomat, September 16, 2015, http://thediplomat.com/2015/09/south-china-sea-satellite-imagery-shows-chinas-buildup-on-fiery-cross-reef/.
[18] Bryan Clark, CSBA, personal e-mail correspondence, October 15, 2016.
[19] IHS Jane’s, “KJ-2000,” Jane’s Strategic Weapons Systems, accessed October 17, 2016, https://janes.ihs.com/Janes/Display/1344988; IHS Jane’s, “Xian ASN-229A, Jane’s Strategic Weapons Systems, accessed October 17, 2016, https://janes.ihs.com/Janes/Display/1318933; and IHS Jane’s, “CAC Wing-Loong,” Jane’s Strategic Weapons Systems, accessed October 17, 2016, https://janes.ihs.com/Janes/Display/1318822.
[20] Timothy R. Heath, “Beijing Ups the Ante in South China Sea Dispute with HQ-9 Deployment,” Rand Corporation, March 28, 2016, accessed at http://www.rand.org/blog/2016/03/beijing-ups-the-ante-in-south-china-sea-dispute-with.html; Richard D. Fischer Jr., “Imagery suggests China has deployed YJ-62 anti-ship missiles to Woody Island,” IHS Jane’s Defence Weekly, March 23, 2016, http://www.janes.com/article/59003/imagery-suggests-china-has-deployed-yj-62-anti-ship-missiles-to-woody-island.
[21] Special thanks to Bryan Clark for bringing this possibility to our attention; IHS Jane’s, “HQ-9,” Jane’s Strategic Weapons Systems, accessed October 17, 2016, https://janes.ihs.com/Janes/Display/1501651.
[22] Victor Robert Lee, “South China Sea: Satellite Imagery Shows China’s Buildup on Fiery Cross Reef,” The Diplomat, September 16, 2015, http://thediplomat.com/2015/09/south-china-sea-satellite-imagery-shows-chinas-buildup-on-fiery-cross-reef/; Thomas Shugart, “China’s Artificial Islands are Bigger (and a Bigger Deal) Than You Think,” War on The Rocks, September 21, 2016, accessed at http://warontherocks.com/2016/09/chinas-artificial-islands-are-bigger-and-a-bigger-deal-than-you-think/; Jerry Hendrix, “Retreat from Range: The Rise and Fall of Carrier Aviation,” Washington, DC: Center for New American Security (June 2015), 51; Aaron Friedberg, A Contest for Supremacy: China, America, and the Struggle for Mastery in Asia (New York: W.W. Norton & Company, Inc., 2011), 219; and Mark Gunzinger and Bryan Clark, “Winning the Salvo Competition: Rebalancing America’s Air and Missile Defenses,” Washington, DC: Center for Strategic and Budgetary Assessment, 2016, 2-3.
[23] IHS Jane’s, “HQ-9/FT-2000,” Jane’s Strategic Weapons Systems, accessed October 17, 2016, https://janes.ihs.com/Janes/Display/1494658; Richard D. Fisher Jr., “Imagery suggest China has deployed YJ-62 anti-ship missiles to Woody Island,” Jane’s Defence Weekly, March 23, 2016, https://janes.ihs.com/Janes/Display/1765554; IHS Jane’s, “DF-21,” Jane’s Strategic Weapons Systems, accessed October 17, 2016, https://janes.ihs.com/Janes/Display/1316682; IHS Jane’s, “CJ-10 (DF-10/KD-20),” Jane’s Strategic Weapons Systems, accessed October 17, 2016 https://janes.ihs.com/Janes/Display/1748687; and CIA World Factbook, “Political Southeast Asia,” available at https://www.cia.gov/library/publications/the-world-factbook/graphics/ref_maps/political/pdf/southeast_asia.pdf.
[24] Hendrix, “Retreat from Range: The Rise and Fall of Carrier Aviation,” 3; Jan Van Tol, et al “AirSea Battle: A Point-of-Departure Operational Concept,” 19.
[25] Andrew S. Erickson, Connor M. Kennedy, “Beware of China’s “Little Blue Men” in the South China Sea,” The National Interest, September 15, 2015, http://nationalinterest.org/blog/the-buzz/beware-chinas-little-blue-men-the-south-china-sea-13846.
[26] The Chinese maritime militia has been involved in numerous international maritime skirmishes including the 1974 conflict in the Parcel Islands, the harassment and sabotage of U.S. survey ships in 2002 and 2009 and the seizing of Scarborough Shoal in 2012. See Andrew S. Erickson and Connor M. Kennedy, “Countering China’s Third Sea Force: Unmask Maritime Militia before They’re Used Again,” The National Interest, July 6, 2016, http://nationalinterest.org/feature/countering-chinas-third-sea-force-unmask-maritime-militia-16860?page=show.
[27] For further examination of China’s merchant marine and its potential to provide support to military operations, please see: Dennis J. Blasko, “China’s Merchant Marine,” prepared for the “China as ‘Maritime Power’ Conference” at the CNA Conference Facility, July 28-29, 2015, accessed at https://www.cna.org/cna_files/pdf/China-Merchant-Marine.pdf.
[28] Bryan Clark, personal correspondence through email, October 15, 2016.
[29] Lyle Goldstein, “The South China Sea Showdown: 5 Dangerous Myths,” The National Interest, Sept. 29, 2015, http://nationalinterest.org/feature/the-south-china-sea-showdown-5-dangerous-myths-13970; Zhang Hongzhou, “China’s Fishing Industry: Current Status, Government Policies, and Future Prospects,” prepared for the “China as ‘Maritime Power’ Conference” at the CNA Conference Facility, July 28-29, 2015, https://www.cna.org/cna_files/pdf/China-Fishing-Industry.pdf.
[30] Special thanks to Dr. Joel Wuthnow, at NDU’S Center for the Study of Chinese Military Affairs for shedding light on China’s plans to improve “jointness” between its branches of the military; see also “China’s Military Strategy,” The State Council Information Office of the People’s Republic of China, Beijing, May 2015, http://eng.mod.gov.cn/Database/WhitePapers/index.htm; for more information on the PLA’s planned reforms, see: Phillip C. Saunders and Joel Wuthnow, “China’s Goldwater-Nichols? Assessing PLA Organizational Reforms,” Strategic Forum (Washington, DC: National Defense University Press, April 2016), accessed at http://inss.ndu.edu/Portals/68/Documents/stratforum/SF-294.pdf.
About the Authors
Austin Hale is currently working as a research intern at the National Defense University’s Center for Strategic Research and is a student at George Washington University.
Frank G. Hoffman serves on FPRI's Board of Advisors, and effective June 20, 2011, Mr. Hoffman is serving at the National Defense University as a Distinguished Research Fellow with the Institute for National Strategic Studies.
No comments:
Post a Comment