Marcus J. Ranum
 Summary: The breakout year for cybersecurity continues, with a massive global attack — more than 45,000 attacks in 99 countries by software linked to (built by?) the NSA (source). In this from the archives cybersecurity expert Marcus Ranum explains defense in this new world. Offense gets all the attention, but smart organisations win by defense. See today’s second post: Skip the hysteria. What you need to know about the big ransomware attack.
Summary: The breakout year for cybersecurity continues, with a massive global attack — more than 45,000 attacks in 99 countries by software linked to (built by?) the NSA (source). In this from the archives cybersecurity expert Marcus Ranum explains defense in this new world. Offense gets all the attention, but smart organisations win by defense. See today’s second post: Skip the hysteria. What you need to know about the big ransomware attack.
In the previous chapters of this series, I showed how cybercrime increases our awareness of computer security weaknesses and force us to constantly improve our defenses — accidentally improving our posture against cyberwar and increasing the likelihood that cyberspies will be uncovered. The logistical problems of keeping a cyberweapon fresh and secret are severe, when you consider that you’re fielding it at the targets’ systems — where it is susceptible to dissection and analysis when it’s discovered. This dynamic has already been seen to be at play with the Stuxnet family of attack tools: security responses rapidly co-evolve with attack tools.
(2) Defense Strategies
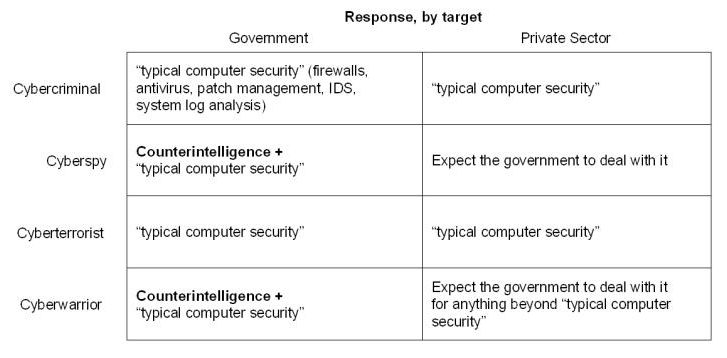
When we consider a breakdown of our defensive options, they aren’t very interesting!
Here’s the problem: the tools we have for defense against pretty much everything in cybersecurity boils down to: firewalls, intrusion detection/prevention, antivirus, patch management, system log analysis, etc. Those are what I refer to as “typical internet security” — the tools that have evolved to serve as effective techniques against cybercriminals.
These are the small ones.
Why not? Mostly because there isn’t anything more that the defenders can use. We’re already snooping into application data using FPGAs and regular expression accelerators in “next generation firewalls” and we’re already profiling users’ activities, checking their authentication status, doing statistics on edge-networks for weird connectivity, trapping and analyzing kernel calls, and looking for edge-cases in system logs. The profit-motive is so strong in the internet security industry that, if someone came up with a great new defensive idea, it would migrate rapidly between the military/defense market and the civilian market. In fact, to an observer of the security industry such as myself, it looks like the flow of innovation is doing from the civilian market toward the defense market, not the other way around.
Unlike traditional military technology, it’s impossible for a nation-state to monopolize computer security, so the free market reigns. I can assure you, as a “cyberweapons designer” for the last 20+ years, if I had an idea for a great new security tool, I’d make a huge amount of money selling it commercially, rather than reserving it for the exclusive defensive use of any one country’s military. Besides, once the ideas are had, the software is fairly simple to replicate. Thus we see a great “levelling effect” in defensive cyberweapons. What we have is what we’ll work with, because it’s all we have.
Where defensive cyberweapons get interesting is where they are knowledge-based: a next-generation firewall doesn’t just block packets based on source/destination address, it can be programmed to analyze data passing through it and specifically block portions of desired transactions. This makes them extremely nimble when it comes to reacting to an attack. For example, I know one site that was having a problem with a specific botnet variant. They put several next-generation firewalls in and programmed them with a custom signature to specifically match (and black hole) the botnet’s command-and-control traffic. Poof!
With knowledge-based products you’ve got the ability to reconfigure them quickly with new knowledge on short notice. This is where the dynamics of attack/defense might change: I suppose we could imagine an intelligence community having its own knowledge/expertise resource center. They could use off-the-shelf commercial tools and apply not-so-off-the-shelf expertise on top of them.
On the chart, “counterintelligence” implies that the target is going to amplify its defenses by analyzing the actions of potential attackers, and preparing to specifically thwart them. This could be done the expensive way, by embedding intelligence assets in an enemy’s cyberattack process, or the inexpensive way, by analyzing their objectives and hardening the points of attack. If you have an idea of your opponent’s cyberweapons stack, you can develop counter-attacks designed specifically to moot entire stacks of those weapons.
The point remains that, other than adding specific knowledge or intelligence, the elements on the cyberwar battlefield are using basically the same gear and the likelihood of a game-changing upgrade for one side or the other is effectively zero. That argues that cyberwar, at best, will be an intelligence war (a war of knowledge-bases) and that any advantage held by one side or the other is going to be very very fleeting indeed. This is why I say that “On the internet, the best defense is a strong defense.”
(3) Corporate Response
The White House, FBI, and intelligence community are fond of telling corporations that they must improve their cybersecurity. The cynic wonders if it’s simply a call to “buy more stuff!” because there isn’t any great new stuff that corporations can meaningfully do. Corporations already have available to them the entire panoply of internet security technologies — exactly the same as everyone else.
Sure, there are businesses that don’t take security seriously enough (and they tend to have “teaching moments” fairly frequently) but what corporations should really be pointing out to the government is that aside from defensive precautions that should be taken, there’s nothing more that’s practical to do.
It is not practical for Citibank to try to spy on The Mossad’s cyberwar tools developers, to gather advanced intelligence about what they are up to. It is not a good investment in shareholders’ money for Google to spy on Chinese Government spies to try to figure out where the next attack is coming from – they’re busy trying to keep the ordinary cybercriminals out. It’s the government’s job to do the counter-intelligence; that’s what corporations would pay their taxes for, assuming they actually paid taxes.
Because of this dynamic, the security world has proceeded to evolve in the only manner that is rational: doing basic internet security while sitting back and waiting for the government to do its job on the politico-military front. That the government keeps trying to throw its problem back into the laps of the corporations should be making people worry. Ultimately, other than spending more money on analysts, companies already have all the firewalls and internet security that they need in order to fight the cybercriminals. Corporate security managers’ response to the threat of state-sponsored cyberspies ought to be “isn’t that your job?”
(4) Counterintelligence
Because of the cost of developing cyberweapons, and how easily they can be mooted once the defender has a profile of how they operate, one obvious response to a hostile power gearing up for cyberwar is to defeat their weapons. Being a double-agent cyberweapons developer would be extremely lucrative; in a sense that’s what the guys who sell Zeus are doing right now.
If you’re a person who makes backdoors in software for a living, could you resist the temptation to backdoor your backdoor? Selling the keys could prove dangerous but profitable. The US’ cyberwar efforts appear to be relying (as usual) on outsider contractors. How can you tell if your backdoor is backdoored if you didn’t write it, or don’t have the skills to write it yourself?
One place where government counter-intelligence could get positively involved in cyberwar would be to start disclosing as much information as possible about the cyberspace activities of hostile powers. Because, unlike with military weaponry, disclosing hostiles’ methods would result in making them ineffective without any cost to the defender. Unfortunately, in the US, the FBI has relied on asserting claims of Chinese cyberattacks, rather than “outing” their methods and tools – which would have the effect of quickly rendering them obsolete as the commercial computer security industry took over and added them to its knowledge-base. The US DoD and intelligence community’s approach, so far, has been exactly backwards – by telling everything you know, you force your enemy to keep innovating.
(5) Conclusion
The big scenarios of cyberwar — “putting a country back to the pre-industrial era” — are overblown and ridiculous; generally they appeal to those who don’t really understand data networking or system administration. There are plenty of examples of successful attacks against individual point targets, but the big scenario does not follow logically as a consequence of a lot of small ones – what we’re more likely to see over the coming years are attacks against less important targets of opportunity.
Since it has been revealed to the community and dissected at length, Stuxnet has done more to justify improvements in security systems than anything else; in that sense it was self-defeating. It is a stone thrown by people who live in a glass house, that will serve to encourage more stone-throwing.
Because of the close relationship between cyberwar and cyberespionage governments that wish to have effective defenses will do well to merge those capabilities under the same roof; avoid inter-service toe-stepping. I’d go so far as to say that there really isn’t much of a difference between the capability sets required for cybewar and cyberespionage. They are technically the same problem and it seems to me that the intelligence-gathering aspect of cyberwar may be so much more valuable than the offensive aspect, that it might not even be worth engaging in offensive operations except for in very narrow situations.
The logistical problems of cyberwar need to be granted more weight than they have been, to date. One thing defenders must do is to turn the logistical problems to their advantage by exacerbating them – publishing and “outing” opponents capabilities; leveraging the existing commercial security products infrastructure to place would-be attackers on an endless treadmill of researching new techniques while simultaneously making them look bad.
Cyberwar is the “shiny new thing” for militarists, but it’s a gift that can’t keep on giving. The more it’s used, the more easily it can be defeated.
At this point, we can be sure that anyone who builds a gas centrifuge cascade is going to be a little bit more careful about their software than usual; perhaps they won’t rely on the lowest bidder to configure it. And that, in a nutshell, is the whole problem. Cyberwar forces organizations to re-examine their trust-boundaries: who do they get to do what, and how can they tell whether their service providers and supply chains are tamper-proof? For a government like the US’, that seems eager to outsource practically everything, that appears to be the opening of a gigantic and very nasty can of worms.

No comments:
Post a Comment