By Catalin Cimpanu
 Security researchers from Kaspersky Lab published yesterday a report detailing the operations of a new cyber-espionage group that's been active in the Middle East region for the past three years.Codenamed ZooPark, this advanced persistent threat (APT) has started operating in 2015 and has slowly evolved over the years, growing in sophistication. The Kaspersky report lays out the group's past operations —split into four periods, based on the malware they've used in attacks.Attackers deployed a very simplistic malware, only capable of two operations —stealing accounts details registered on the victim device, and stealing contacts from the address book. In this stage, attackers tried to disguise their app as the official Telegram application.
Security researchers from Kaspersky Lab published yesterday a report detailing the operations of a new cyber-espionage group that's been active in the Middle East region for the past three years.Codenamed ZooPark, this advanced persistent threat (APT) has started operating in 2015 and has slowly evolved over the years, growing in sophistication. The Kaspersky report lays out the group's past operations —split into four periods, based on the malware they've used in attacks.Attackers deployed a very simplistic malware, only capable of two operations —stealing accounts details registered on the victim device, and stealing contacts from the address book. In this stage, attackers tried to disguise their app as the official Telegram application.
Phase 2 (2016)
ZooPark operators improve their malware's capabilities. New feature additions show clear intentions that the malware was to be used as spyware.
Phase 3 (2016)
The group appears to realize that despite their best efforts, the malware is still under-developed, so they fork a version of the Spymaster Pro commercial spyware app and try to blend the two together.
Phase 4 (2017)
ZooPark's malware receives a major facelift. Changes added in Phase 3 are mostly dropped, and the group builds even more features on top of the old Phase 2 codebase.
"This last step is especially interesting, showing a big leap from straightforward code functionality to highly sophisticated malware," Kaspersky experts say. "This suggests the latest version may have been bought from vendors of specialist surveillance tools. That wouldn't be surprising, as the market for these espionage tools is growing, becoming popular among governments, with several known cases in the Middle East."
As for the distribution methods, ZooPark operators relied on simple techniques. They would either create Telegram channels where they'd share links to the malicious apps, or they'd compromise legitimate sites where they'd redirect incoming visitors to pages offering the tainted apps for download.
According to Kaspersky, these tactics worked, and the group was able to compromise victims in several countries, such as Morocco, Egypt, Lebanon, Jordan, and Iran.
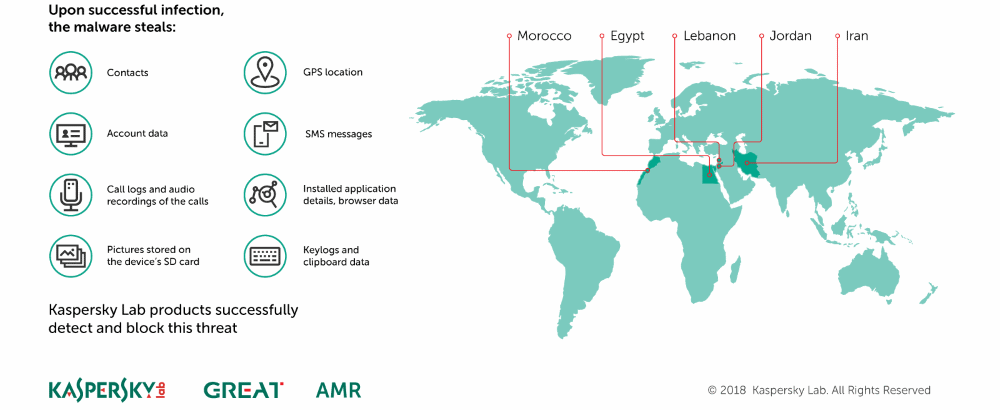
Image credits: Tatiana Belkina, EsaRiutta, Kaspersky Lab
Composition: Bleeping Computer

No comments:
Post a Comment