By Daniel Miller
Key points:
The three broad categories of hackers behind attacks are: state actors, criminal groups or hacktivists
You can generally tell the different between them based on what they're targeting and the sophistication of the attack, an expert says
Australia may not be prepared for a large-scale cyber attack on civilian infrastructure, the military's cyber boss says
In the case of last year's breach at Perth-based Navy shipbuilder Austal, the Australian Cyber Security Centre suspected criminals based in Iran.
But for the attack earlier this month on Parliament House's computers, Prime Minister Scott Morrison came out a little over a week later to claim it was the work of a "sophisticated state actor".
How can you tell what's a 'state actor' and what's not?
While specific details of the Parliament attack are not known, there are a range of factors that help determine whether an attack is being carried out by a foreign government or a lone wolf sitting in an internet cafe.
Cybersecurity expert Andrew Woodward from Edith Cowan University, who has been in the industry for 20 years, said you could tell a lot from basic monitoring and logging of internet traffic.
"You can look at the all the traffic coming in and you can use a lot of visualisation tools — your big graphical displays, those kind of things — and if you look at that traffic, it's easy to tell the difference between a room or a building full of people coming after you as opposed to a single entity," Professor Woodward said.
"A single entity can control a botnet or group of PCs, but the level of sophistication in terms of the type of traffic, volume of traffic, types of attacks and systems they're going after… you generally get a feel for what is a lone actor as opposed to what is a dedicated large group from a well-resourced organisation or nation coming after you."
Debi Ashenden, Professor of Cyber Security at Deakin University, agreed the sophistication of the attack and the resources behind it were good "starting indicators" as to whether it was a state actor or not.
"Are they using methods that would be costly to implement and how clear are they at what they're doing?" she questioned.
In the case of the Parliament House hack, the Federal Government has not revealed which nation they believed launched the attack.
Professor Ashenden said such attribution was "something that no country is going to do lightly".
"You have to have robust evidence to be able to do that," she said.
The main types of hackers
Cyber attackers broadly fall into three main categories, Professor Woodward said.
These are:
State actors — hackers backed or employed by a foreign government, often with a political motive and backed up by a lot of resources
Criminal groups or individuals — these attackers are motivated by financial gain
Hacktivists — Groups like Anonymous that undertake cybercrime for personal motivations rather than financial reasons
Professor Ashenden said while hackers could be categorised this way, the motivation behind their attack was more important than the label.
One group may be working with another, she said.
"So hacktivists might be malicious or they might not be," she said.
Are cyber attacks on the rise?
"Absolutely. No question," Professor Woodward said.
Professor Ashenden agreed: "Coupled with the fact that we're getting better at seeing when they actually happen."
As companies move more of their business online, including storing user data in the cloud, that presents more targets to attackers.
"And amongst all of this increasing online presence we have a massive, massive skills shortage for cyber security professionals," Professor Woodward said.
In a 2017 Ponemon Institute study for IBM, figures showed it took on average 190 days for a company to detect a data breach.
That's from a sample of 419 companies in 13 countries, including Australia, the United States, Germany and the UK.
"There's some really sad stats out there that in the vast majority of cases an organisation only knows it's been attacked because an external third party has reported it to them because they've noticed before the company in question," Professor Woodward said.
He said there was a need for more cybersecurity professionals and funding across governments, the research sector and the private sector.
"We don't even know what's going on in our own networks … we find out when someone else tells us," he said.
"That's pretty damning. It doesn't get much worse than that."
Professor Ashenden, who recently moved to Australia from the UK, said it didn't matter what country you were in, there weren't enough skilled cybersecurity specialists to keep up with attacks.
How well prepared is Australia?
Major General Marcus Thompson, who leads the military's Information Warfare Division, said he held concerns about a large-scale cyber attack on Australia's civilian infrastructure.
That means things like utilities, banks and telecommunications.
"I have a concern, and I know this concern is shared by many of my colleagues and mates throughout the national security community, that in the event of a significant incident on Australia in cyberspace, the resources that would be required to respond might not exist at the scale that might be required," Major General Thompson said.
Professor Woodward said based on everything he knew, he would concur.
"The military has come out saying in the day-to-day basis, we've got things covered. In the event of an actual cyberwar we'd probably be in trouble," he said.
"I think that's a pretty accurate reflection on the state of what things are."
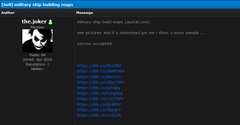
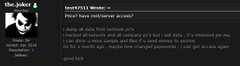
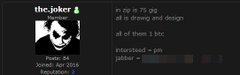
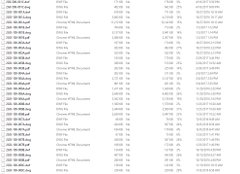
A security researcher noted that the files were put up for sale on the dark web in exchange for bitcoin, but the head of the Australian Cyber Security Centre clarified that "nothing of national security significance was taken".
Professor Woodward said attacks like the one on Austral showed that as a society we are "absolutely underprepared" for cyber threats.
"There's a significant challenge. It does come back to that skills issue," he said.
"If you are relying on other people to come in to defend your network and you can't get enough of those people or the people you get aren't quite up to the job then unfortunately that is going to be the end result."


No comments:
Post a Comment