 As our society evolves, so does our reliance on telecommunications technology. Cybercriminals prey on our daily use of electronic devices and continuously seek out new ways to exploit vulnerabilities and access information. Cooperation and information-sharing between law enforcement and the private sector has therefore become essential in the fight against these types of crime. One example of this collaboration is the joint Cyber-Telecom Crime Report 2019, published by Europol and Trend Micro today. The report gives an overview of how telecom fraud works and serves as a technical guide for stakeholders in the telecoms industry.
As our society evolves, so does our reliance on telecommunications technology. Cybercriminals prey on our daily use of electronic devices and continuously seek out new ways to exploit vulnerabilities and access information. Cooperation and information-sharing between law enforcement and the private sector has therefore become essential in the fight against these types of crime. One example of this collaboration is the joint Cyber-Telecom Crime Report 2019, published by Europol and Trend Micro today. The report gives an overview of how telecom fraud works and serves as a technical guide for stakeholders in the telecoms industry.
OVER €29 BILLION PER YEAR
This report highlights that telecom fraud is becoming a low-risk alternative to traditional financial crime. The reduced cost and increased availability of hacking equipment means this type of fraud is on the rise. The cost of telecommunications fraud is estimated to be €29 billion a year.
At its heart, this fraud is the abuse of telecommunications products (mainly telephones and mobile phones) or services with the intention of illegally acquiring money from a communication service provider or its customers.
The main goal of criminals is to gain access to customers’ or carriers’ accounts, where debt can be incurred in the criminal’s favour.
The most common methods can be broken into different categories ranging from crude to highly sophisticated scams:
Vishing calls. Vishing (a combination of the words Voice and Phishing) is a phone scam in which fraudsters trick victims into divulging their personal, financial or security information or into transferring money to them.
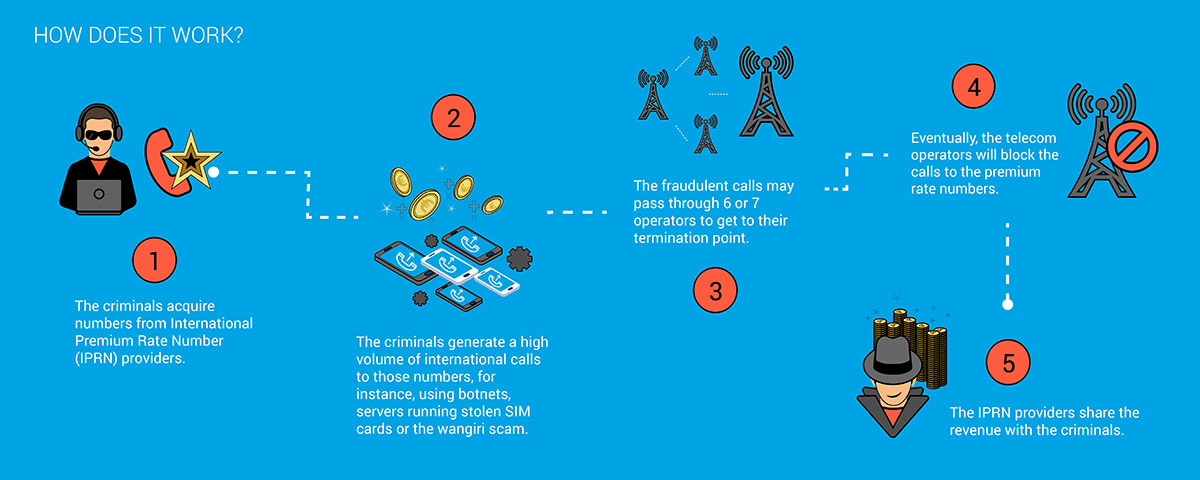
One (ring) and cut or Wangiri -Japanese for ‘one ring and drop the call’ – is a telephone scam where criminals trick victims into calling premium rate numbers. A fraudster will set up a system to dial a large number of random phone numbers. Each call rings just once then hangs up, leaving a missed call on the recipients’ phones. Users often see the missed call and, believing it to be legitimate, call the premium rate number back.
International Revenue Sharing Fraud (IRSF) has been the most damaging fraud scheme to date. It involves transferring monetary value from one carrier to another, based on the inter-carrier trust between telecom operators. Patient fraudsters wait for the logs to expire before executing any further money laundering steps.
THE CYBER-TELECOM INTELLIGENCE FUSION
The Europol EC3 CyTel working group, created in 2018, brings together more than 70 experts from law enforcement and global partners from the telecommunications industry, in order to share intelligence, knowledge and experience, and the techniques required to combat this type of fraud. The concept of a global telecom network, with unified telecommunications service providers and law enforcement, is essential for this fusion of cyber-telecom intelligence.
‘Telecommunications fraud is another example of criminals “hacking the system” in order to abuse legitimate enterprises for criminal gain,’ said Steven Wilson, Head of the Europol’s European Cybercrime Centre, ‘While this is not a new crime area, it does represent a new challenge for many law enforcement agencies throughout the European Union.’
Craig Gibson, Principal Threat Defence Architect at Trend Micro, added how vulnerable telecommunications can be and how it impacts our daily life: ‘We trust that our phones will work, that we can work from home, that we can be paid through our ATM accounts, and that we can shop online. We tend not to think about what is under the covers of the unseen global network we rely on so much.’
Craig Gibson, Principal Threat Defence Architect at Trend Micro, added how vulnerable telecommunications can be and how it impacts our daily life: ‘We trust that our phones will work, that we can work from home, that we can be paid through our ATM accounts, and that we can shop online. We tend not to think about what is under the covers of the unseen global network we rely on so much.’
No comments:
Post a Comment