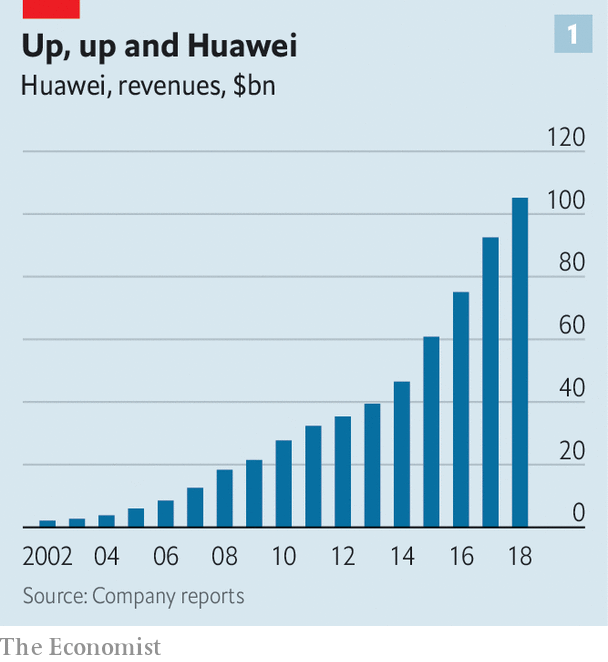
 It is hard to think of a better reflection of the rise of China than the rise of Huawei. Like China, the firm, which was founded in 1987, began at the bottom of the value chain, reselling telephone-switching gear imported from Hong Kong. Also like China, it was not content to stay there. These days its products—from smartphones to solar panels—are sleek, high-tech and competitive with anything its rivals can produce. As a result its revenues have soared, hitting $105bn in 2018 (see chart 1). Huawei, and its mother country, have become technological pacesetters in their own right. The firm employs 80,000 people in research and development alone. China filed 53,345 patents in 2018, a hair behind America’s 56,142. Of China’s, around one in ten came from Huawei alone.
It is hard to think of a better reflection of the rise of China than the rise of Huawei. Like China, the firm, which was founded in 1987, began at the bottom of the value chain, reselling telephone-switching gear imported from Hong Kong. Also like China, it was not content to stay there. These days its products—from smartphones to solar panels—are sleek, high-tech and competitive with anything its rivals can produce. As a result its revenues have soared, hitting $105bn in 2018 (see chart 1). Huawei, and its mother country, have become technological pacesetters in their own right. The firm employs 80,000 people in research and development alone. China filed 53,345 patents in 2018, a hair behind America’s 56,142. Of China’s, around one in ten came from Huawei alone.
Huawei’s ascent, like that of China, has caused a good deal of worry elsewhere in the world. Three decades on, the firm is still in the telecoms-equipment business. Along with Nokia, a Finnish firm, and Ericsson, a Swedish one, Huawei has become one of the world’s biggest suppliers of the high-tech kit used to build mobile-phone networks around the world. Of the three, Huawei has been the most active in setting the technical standards for “fifth-generation” (5g) networks. These promise big increases in speed and capacity that will improve some existing technologies, such as connected cars, and make possible new ones, including the sensor networks that will supposedly enable “smart cities”. Huawei and China therefore sit at the heart of technologies which governments worldwide have come to regard as a critical piece of future national infrastructure.
A half-open door
That is the context in which to see a decision by Britain, leaked to the press on April 24th, to grant Huawei a limited role in building its 5g networks. It was taken in the teeth of a determined American campaign to persuade its allies to freeze the company out. Mike Pence, America’s vice-president, and other officials have warned publicly that Huawei’s gear could contain “back doors”—malicious code designed to let Chinese spies snoop on communications, or even bring down networks altogether.
Mike Pompeo, America’s secretary of state, has threatened to withhold intelligence co-operation from anyone who uses the firm’s gear in “critical” networks. Australia, like Britain one of America’s allies in the “Five Eyes” electronic-spying pact, has banned the firm explicitly. New Zealand, another member, has rebuffed a request from a local firm to use Huawei’s kit. Japan—which is not in the club, but is closely allied to America—has tightened its rules.
America’s stance may seem sensible given China’s history of electronic espionage. The country is a prodigious hacker. It has purloined everything from the plans for the f-35, an advanced fighter jet, to a database of millions of American civil servants. It has been accused of hacking India’s Ministry of Defence. Britain and America say it has conducted a “vast” and “unrelenting” campaign targeting dozens of Western companies and government agencies. Last year CrowdStrike, a cyber-security firm, put China ahead of Russia as the most prolific sponsor of cyber-attacks against the West.
Yet Britain has long argued that such threats can be managed without banning Huawei outright. Its most recent decision reaffirms that stance. But it is not the only refusenik. Germany, another of America’s close allies, has resisted an outright ban. India is thought to be open to letting the firm in, albeit with limitations. In February Nick Read, the boss of Vodafone, one of the world’s biggest telecoms firms, challenged the Americans to provide concrete evidence of foul play. He warned that shutting out Huawei would be “very, very expensive” and could delay the deployment of 5g networks by years. Kester Mann of ccs Insight, a consulting firm, says that the company’s gear is up to a year ahead of the products manufactured by its rivals, as well as being cheaper.
Britain’s stance matters more than the middling size of its telecoms market suggests. The country’s signals-intelligence agency, gchq, is the biggest in the Five Eyes after America’s National Security Agency (nsa), with which it works hand-in-glove. And few countries know more about how Huawei operates. Britain was one of the firm’s first beachheads in the West. In 2005 Huawei was chosen by bt, a formerly state-owned telecoms company, to be part of a £10bn ($18bn) contract to modernise Britain’s phone network. Even then, security types regarded Huawei with suspicion. But civil servants did not tell ministers about the firm’s involvement until after the contract had been signed.
In an act later described by mps as trying to “shut the stable door after the horse has bolted”, Britain set up a lab, paid for by Huawei but run by the British, which would go over its kit and software with a fine-tooth comb, looking for anything untoward. The Huawei Cyber Security Evaluation Centre (hcsec) has been running since 2010. That lab, say British spooks, has provided unparalleled insight into both Huawei’s products and its corporate culture. It has proved useful for Huawei, too, enabling it to point out that its equipment has survived repeated and intrusive checks by a country with one of the most capable electronic-intelligence agencies in the West.
Huawei has flatly and repeatedly denied that it inserts back doors. Vincent Pang, a senior manager, said in December that the firm has strong incentives not to spy on its customers. If a back door were ever discovered, he said, “it would destroy our markets.” And in eight years of looking, Britain’s spies say they have never found one. That does not placate critics, who argue that, even if there are no back doors now, there might be in future, perhaps provided through the regular patches or updates that will be required for the huge amounts of code that a 5g network relies on. Huawei’s commercial self-interest is irrelevant, they say, pointing to a Chinese law that compels private firms to assist the intelligence services when asked.
Back doors may be bad for business, but they are not unknown. Leaks from Edward Snowden, a former worker at the nsa, seemed to confirm suspicions that it had tried to put a back door into a cryptographic standard proposed in 2006, which could have given America’s spies the ability to read communications that made use of it. Juniper, an American maker of network routers, announced in 2015 that it had found “unauthorised code” in its products that could have led to communications being monitored. Suspicion once again fell on the nsa.
Listening in
Huawei has used such stories to resist American pressure. In February Guo Ping, one of the firm’s three rotating chairmen, accused America of attacking it because the spread of its technology was hampering America’s spying. Mr Guo did not mention China’s efforts at electronic snooping. In 2018, for instance, newspaper reports alleged that China had been siphoning off sensitive data from computer networks at the African Union’s headquarters in Addis Ababa. The building had been paid for by China and built by a Chinese firm. (China’s foreign ministry denied the reports.)
But there is more to worry about than back doors and here Britain’s findings have been less reassuring. In the hcsec’s most recent report, published in March, it suggests that the code in Huawei’s products is a buggy, spaghettified mess. That may not sound sinister. But bugs can be as useful to hackers as any back door. “Why bother going to all the trouble of putting in a back door when you can just look for [accidental] vulnerabilities like everyone else?” asks Jon Crowcroft, a computer scientist at the University of Cambridge.
Russia’s prowess in cyber-attacks demonstrates the point. It has no big hardware firms to lean on to provide back doors. That has not stopped its hackers from attacking Ukraine’s power grids or stealing emails from American politicians. In February Ciaran Martin, head of the National Cyber Security Centre (ncsc), an arm of gchq, said that his agency had dealt with about 1,200 “significant cyber-security incidents” since it was set up in 2016. State-sponsored back doors had been a factor in none of them.
Bugs infest every piece of complex software but seem more common in Huawei’s gear than in competitors’ products. Evidence of Huawei’s lax attitude is everywhere, with thousands of snippets of unsafe code. One piece of kit, says the hcsec, used in mobile-phone base stations, contained 70 copies of four different versions of Openssl, a widely used set of cryptographic protocols designed to secure data travelling over networks. Researchers frequently find security flaws in Openssl, meaning that sticking to the newest versions is vital. Huawei’s kit, it seems, is at risk from hackers of all kinds, not just Chinese state-sponsored ones. Insiders blame this sloppiness at least partly on the same commercial agility that has made Huawei so popular among its customers for its speedy introduction of new products.
Huawei has promised to do better. In November, in response to criticism from the hcsec, it announced a $2bn overhaul of its software-development practices. David Wang, an executive at Huawei, reiterated that pledge after the latest round of brickbats, but said it would take three to five years. The hcsec takes a less rosy view, saying that “no material progress” had been made in fixing such issues since they were last raised a year ago. Worse, it says it has not seen anything to give it confidence that Huawei could meet the necessary standards, especially since similar promises made in 2012 appear to have led nowhere.
That alone might be enough to persuade countries that Huawei’s products are best left on the shelf. But there is one final complicating factor, says Rahim Tafazolli, who runs the 5g Innovation Centre at the University of Surrey. Gear from Huawei’s rivals has bugs, too, even if they are less common. Last year, for instance, faulty software in equipment made by Ericsson caused a day-long interruption in phone networks belonging to O2, a British operator, and SoftBank, a Japanese one. Among the best ways of limiting the damage that bugs—or hackers—can cause, says Mr Tafazolli, is to build resilient networks. And a way to do that is to use equipment from rival suppliers, so that a problem in one manufacturer’s devices does not bring down the entire network. But given the concentration in the market, any network keen on diversity will find it hard to avoid Huawei’s products.
British cyber-security officials say it is possible to finesse all these worries. One measure is to exclude Huawei from government networks. Another is to use it for less sensitive equipment at the edge of networks, such as transmission equipment, but not the more sensitive data-processing “core”. That is harder to do with 5g networks, in which more data-crunching happens closer to the network’s periphery, to boost speed. But monitoring of network activity can help flag anything suspicious, as can healthy scepticism about Huawei’s reassurances. Ian Levy, the ncsc’s technical director, has said it operates on the assumption that China does indeed attempt cyber-attacks against Britain and that its government can compel any Chinese firm, including Huawei, to do whatever it wants.
Trouble ahead
Britain’s experiences, and its willingness to make its conclusions public, are likely to influence other nations’ decisions about how to handle Huawei, particularly in the absence of anything similarly concrete from the Americans. But Huawei faces other pressures, too. In December Meng Wanzhou, the firm’s chief financial officer and daughter of its founder, Ren Zhengfei, was arrested in Canada at the behest of the Americans. She faces extradition on charges that she—and Huawei—conspired to dodge American sanctions on Iran. The firm is also accused of trying to steal trade secrets from t-Mobile, an American subsidiary of Deutsche Telekom.
The theft charges are small beer. They centre on a robot called “Tappy”, designed to test smartphone screens. The sanctions-busting case, though, could have serious repercussions. zte, another Chinese technology firm, was convicted on similar charges in 2017. When it became clear in 2018 that zte was trying to dodge its punishments, officials banned American firms from doing business with it. The effects were catastrophic. zte relies on technology from American firms such as Qualcomm, a chipmaker, and Google, which develops Android, a smartphone operating system. zte was forced to stop production and its shares were suspended. Bankruptcy was averted only when Donald Trump, America’s president, agreed to lift the ban as a “favour” to Xi Jinping, his Chinese counterpart. American lawmakers have called for similarly tough sanctions should Huawei be found guilty.
Cyber-security, sanctions-busting and Tappy are, in turn, only parts of an argument that is fundamentally about the relationship between technology and geopolitics, says Janice Stein at the University of Toronto. America, the incumbent superpower, is under no illusions about the relationship between technology and power, of both the hard and soft sort. Neither is China, which aspires to the same status. Huawei is widely seen as a Chinese national champion. It is an important part of “Made in China 2025”, a programme designed to boost China’s abilities in many different fields of technology.
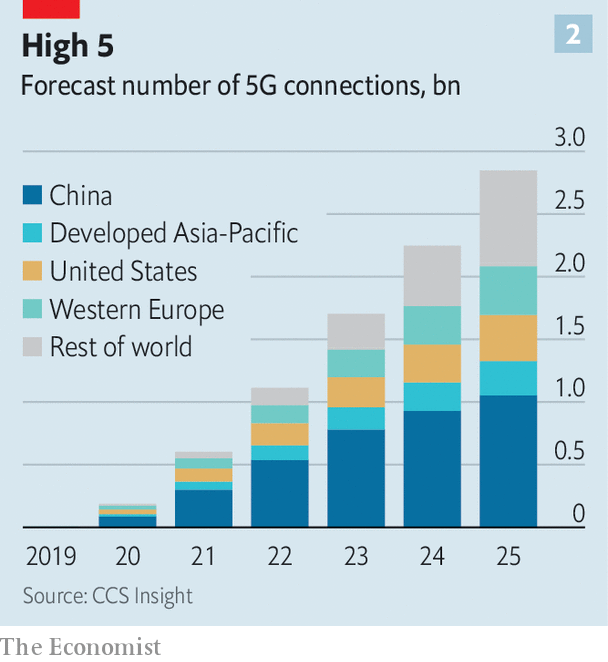
Seeing the arguments through a geopolitical lens throws up interesting questions, says James Lewis at the Centre for Strategic & International Studies, in Washington, dc. One is the effect of sloppy coding, which cuts both ways. If installing Huawei’s buggy gear is a security risk for the West, then it is a security risk for China, too, which is forecast to lead the world in 5g deployments (see chart 2). The West, after all, has hackers of its own, as do China’s neighbours, such as India and Russia. “I would guess that the dozen or so countries with strong sigint [electronic espionage] capabilities jump for joy when they hear someone else is installing Huawei’s stuff,” says Mr Lewis.
He also thinks Western countries, as a counterbalance to Huawei and other Chinese tech firms, should consider whether domestic firms that provide digital infrastructure should be designated as strategically important, as arms-makers and steel firms often are. America has already blocked deals on grounds of national security, some tenuous. A planned $117bn takeover of Qualcomm, for instance, was blocked because the buyer, Broadcom, despite a heavy presence in America, was domiciled in Singapore. (It has since moved back to Delaware.)
Huawei or the highway?
These discussions will become more urgent as the world grows increasingly computerised, says Ms Stein. The electronics that power connected cars are assembled in China, as are those that sit inside smart medical devices and energy meters, and in the financial networks over which the world’s banks transact. Lawmakers are already beginning to make the connections. American politicians have started agitating about whether Huawei’s solar panels pose a risk to the country’s electricity grid.
Weighing all these arguments is difficult even for cyber-security experts, says Mr Crowcroft. One reason is that the modern mix of superpower rivalry, globalisation and high-tech societies is unprecedented. In the cold war, trade across the Iron Curtain was minimal. These days America and China square off atop planet-spanning supply chains that blur the distinction between “Western” and “Chinese” companies. Chinese firms rely on Western technology in their products; Western ones rely on Chinese parts and factories to assemble them. Even the risks are hard to evaluate. Nobody is quite sure just how much cyber-havoc could be caused by a determined nation state, says Mr Crowcroft, largely because there has yet to be a full-scale war between high-tech powers.
While this debate rages in the West, Huawei goes from strength to strength. The firm says it has signed 40 different 5g contracts, more than any of its rivals. It already has a big presence in Africa, Asia and South America. Huawei will see Britain’s approval, however qualified and half-hearted, as another feather in its cap. For all its flaws, the firm—and, therefore, China—will end up building a great deal of the infrastructure on which the world will increasingly depend.
No comments:
Post a Comment