By Eduard Kovacs
Organizations have been investing more in the cybersecurity of industrial control systems (ICS) and operational technology (OT), and the results are showing, but many still perceive the risk as severe or high, according to the SANS 2019 State of OT/ICS Cybersecurity Report published on Wednesday.
This year’s report was sponsored by Cisco, Forescout, Yokogawa, Radiflow, Owl Cyber Defense, and Nozomi Networks and it’s based on data collected from nearly 340 professionals, mostly from organizations with operations in the United States, Europe and Asia.
The previous report was published in 2017, when 69% of respondents rated their overall risk profile as severe (critical) or high. The percentage has now decreased to just over 50%.
People are seen as the greatest risk for compromise (62%), followed at a distance by technology (21%) and processes (14%). The risks posed by people include both internal and external actors, and malicious and accidental actions.
Unprotected devices on the network, external threats (e.g. hacktivists and nation-state actors), and internal accidents represent the top concerns for organizations, while least concerning are phishing scams, malicious insiders and industrial espionage.
The overall number of security incidents involving OT and ICS in 2019 has increased significantly compared to 2017. Experts believe this could be due to the formalization of incident response programs, improved ability to detect incidents, the categorization of certain types of events that in the past may have been ignored as security incidents, and the increased exposure in OT attack surfaces. Another factor that has likely contributed to this increase is the willingness of companies to publicly acknowledge incidents. On the other hand, many organizations still have internal policies that prevent their employees from sharing information about security incidents outside official channels.
While hackers, similar to 2017, have remained the number one source of malicious incidents, the number of incidents involving nation-state actors and organized crime groups has increased significantly in 2019. Of all the incidents, 61% had a disruptive effect on OT activities.
The time it has taken organizations to detect an incident has also decreased compared to 2017, with nearly 80% of respondents saying they had detected incidents within 7 days.
The SANS report shows that the most common initial attack vector was physical access (e.g. USB drives and direct access to equipment), followed by remote access that involved bypassing intended architecture.
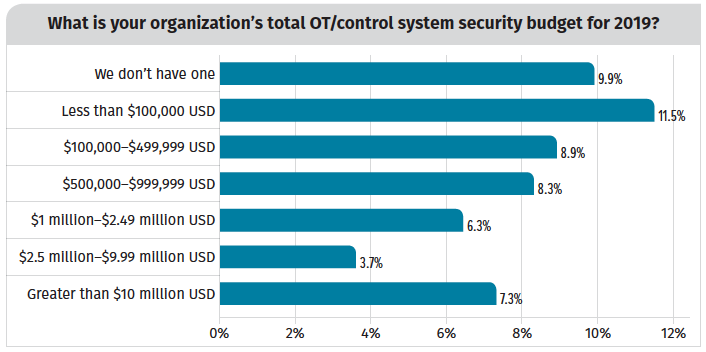
Budgets and the actions taken show that ICS threats are being taken more seriously. In the latest report, 42% of respondents said their budget for control system security increased in the past two years, compared to only 29% in 2017. Moreover, 69% said they conducted a security audit of their OT systems in the past year.
Other encouraging statistics include 60% relying on trained staff to look for events (up from 37% in 2017), and 44% using anomaly detection tools to identify trends (up from 35% in 2017).
Nearly half of respondents named increasing visibility into control systems a priority for 2019 and over a quarter plan on implementing anomaly and intrusion detection systems on their industrial networks.
As for IT/OT convergence, 65% said the current collaboration level is either better or moderate, and 84% have already implemented, are implementing or they plan on implementing an IT/OT convergence strategy. Furthermore, 30% of respondents named security awareness programs for IT, OT and hybrid personnel a top priority for 2019, and 27% named bridging IT and OT initiatives a top priority.
No comments:
Post a Comment