By SYDNEY J. FREEDBERG JR
 Soldiers from the 781st Military Intelligence Battalion, the Army’s offensive cyber unit, in training
Soldiers from the 781st Military Intelligence Battalion, the Army’s offensive cyber unit, in training
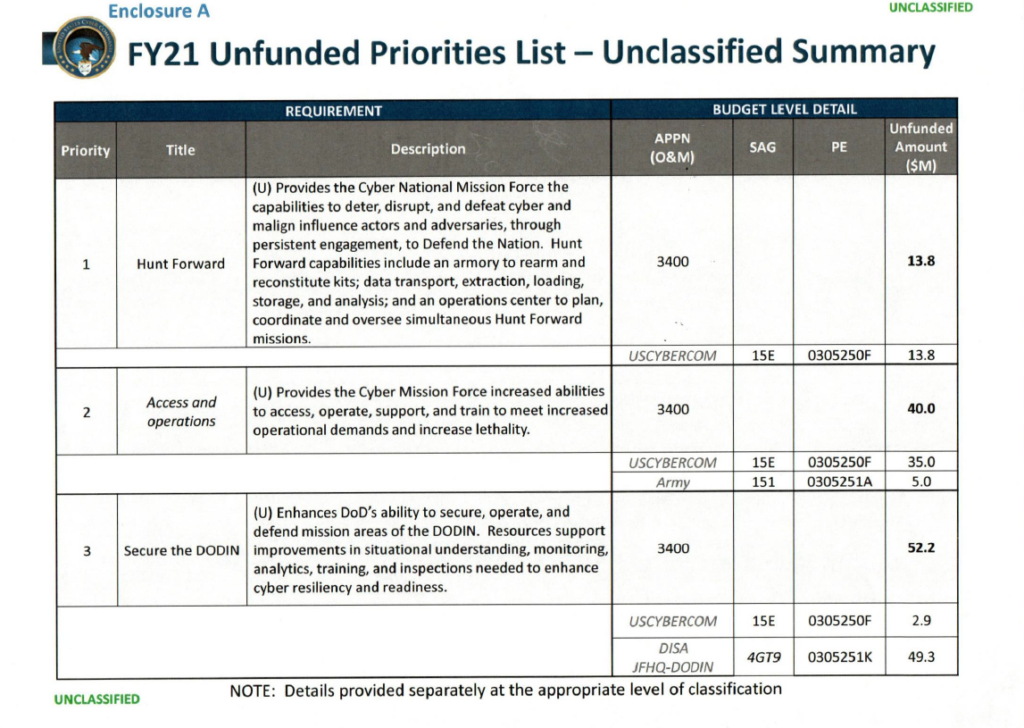
WASHINGTON: Alongside the detailed multi-billion-dollar wishlists released by other parts of the Pentagon, there’s a single-page unclassified summary of US Cyber Command’s Unfunded Priorities List with just three items, totaling $106 million.
“NOTE: Details provided separately at the appropriate level of classification,” says a terse note at the bottom of the page.
Co-located with the notoriously secretive National Security Agency on Fort Meade, Maryland, and commanded by the same four-star officer, Army Gen. Paul Nakasone, CYBERCOM inhabits a world of digital cloak-and-dagger where the very act of revealing a capability exists makes it infinitely easier to defeat. Even a journalist committed to transparency can understand the need for strict classification.
But we can still offer our interpretation of the document, guided by public comments by Gen. Nakasone and others that sketch what CYBERCOM is doing.
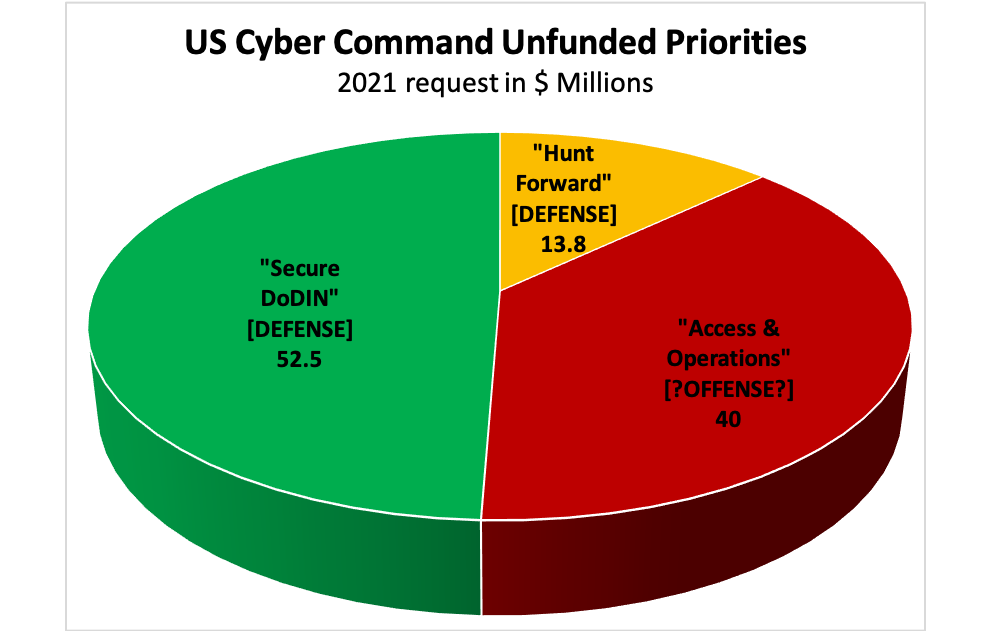
The least controversial category is also the largest: “Secure the DoDIN.” That stands for Department of Defense Information Networks, a deceptively precise-seeming term for the vast agglomeration of different and often incompatible computer networks across the DoD, including leased commercial systems. Gen. Nakasone has a subordinate command, Joint Force Headquarters – DoDIN – led by a three-star general who also runs the Defense Information Services Agency (DISA) — that is solely devoted to this mission. It’s also undeniably defensive.
By contrast, the Pentagon is understandably leery of discussing offensive cyber warfare. But the NSA jargon for hacking foreign networks to conduct espionage is Tailored Access Operations. That strongly suggests CYBERCOM’s $40 million request for blandly named “Access & Operations” is also oriented towards the offense. (Our colleagues at Fifth Domain, who’ve covered this intimately, make the same assessment).
Also suggestive is the brief unclassified description: “Access and operations… provides the Cyber Mission Force increased abilities to access, operate, support, and train to meet increased operational demands and increase lethality.” Lethality is a Pentagon buzzword, favored by former Defense Secretary Jim Mattis, that gets used in all sorts of ways, including for completely non-lethal systems, but the common denominator is having some kind of direct effect on an adversary.
Finally, there’s the $13.8 million request for “Hunt Forward,” which sounds more ominous than it actually is. In recent years, Cyber Command has talked about “defending forward,” which includes establishing a presence in adversaries’ networks to passively monitor their operations and, in at least some cases, to actively disrupt an attack before it begins. More recently, they’d added the concept of “hunting forward,” which specifically means getting friendly nation’s permission to deploy US cyber experts on their territory and hunt for hostile activity on their networks. (Yes, this means “hunt forward” is actually more defensive than “defend forward.” That’s Pentagonese for you).
“In a hunt forward operation, we are able to work with partner nations and receive an invitation to execute operations in their country,” Army Brig. Gen. William Hartman, head of CYBERCOM’s National Mission Force, said recently. “These are generally countries that are in the near abroad of adversaries that we’re potentially concerned about.”
The list includes 12 additional F-35s, and funding to speed development of the GPS anti-jam M-Code signal.
“Near abroad,” incidentally, is originally a Russian term for the now-independent states of the former Soviet Union, such as Ukraine, Georgia, and Estonia, which Moscow considers to be its natural sphere of influence.
No comments:
Post a Comment