Vinugayathri Chinnasamy
The entire world is warning nations about cyberwarfare. Regardless of the inexplicably overlooked warning, we predict that cyberwarfare will be the new frontier of wars between countries – but why?
While cyber space is the digital savior during this COVID-19 era, we are witnessing incidents related to cyber-attacks, hacking and data breaches, which highlights that the internet is not safe. It is imperative to be aware of cyberwarfare, as awareness is the first most important step to mitigating it.
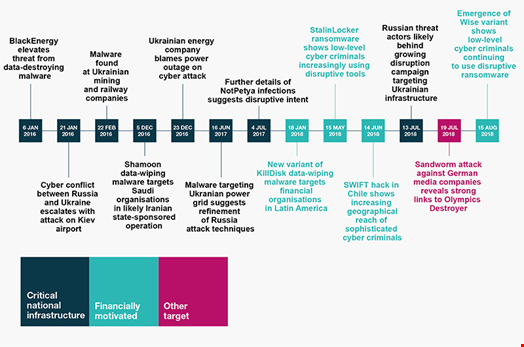
Cyberwarfare is not new, it’s already happening; here is the history of attacks and consequences:
What Does Cyberwarfare Look Like?
Cyberwarfare refers to cyber-attacks executed by one country or state against another; however, it can also be an attack by hackers or terrorists aimed at furthering the mission of the individual nation. In most cases, the computers are not the final target, but the systems they control.
A well-planned attack could alter stock prices, knock out traffic light systems, knock out emergency services, weaken military responsiveness and disrupt the economy.
Cyberwarfare can be launched instantly, leaving room for speculation and making it difficult to counter. The weapons of cyberwar are like those being used by cyber-criminals. It can vary from the very sophisticated to the complete basic. DDoS is one of the unruly weapons. Spear-phishing and social engineering are other standard weapons used to introduce an attacker to the computer of an opponent.
In a cyberwar, the chance of early warning is non-existent; hence, it is difficult to realize who may attack you or even who has attacked you.
Cybersecurity Trends Too Dangerous to Ignore
Cybersecurity is the battlefield where attackers (hackers) and defenders are looking to defeat each other. Right now, attackers are on the winning side.
Hackers are overcoming defenders by unveiling new viruses and malware every day. Varonis has recently uncovered a new malware called Monero cryptojacking malware, which covertly plagued an enterprise for a year. According to the Hackerpocalypse: A Cybercrime Revelation report, the cost of cybercrime damage will reach $6tn by 2021.
No modern invader would resist the urge to disrupt, confuse or destroy enemy communications, sensors and decision-making loops. In addition, attackers are more innovative now. According to RiskBased Security, 3813 data breaches were reported during the first half of 2019, exposing over 4.1 billion records.
The cloud explosion has created another issue. As more companies move to the cloud, so do the cyber-criminals. Researchers have noted massive security attacks on the G Suite and Office 365 using the IMAP protocol.
Political interference will become more common and more sophisticated to disrupt democratic practices.
For example, in a state election, ‘Party A’ involves changing the sentiment through misinformation campaigns in social media channels while simultaneously hacking the website of their direct competitor ‘Party B’ with cyber-vandalism or DDoS attacks. This aspect of cyberwarfare is viewed as hybrid warfare.
The same vulnerabilities and increasing cyber-threats open the doors for cyberwarfare on state and national infrastructure.
How to Prepare for Cyberwarfare
Since there is no international law that governs the use of cyber-arms, the legal status of this new frontier is still blurred. However, this does not mean that cyberwarfare is not covered by the law.
The Cooperative Cyber Defence Centre of Excellence (CCDCoE) has released a textbook called Tallinn Manual, which covers the rare but serious cyber-threats. The manual sets out when a cyber-attack is a breach of international law and how nations can respond to such violations.
Under the pressure of cyberwarfare, the governments of many countries have unveiled a viable national security policy to ensure the security of their information infrastructure in cyber space. Here are a few examples of strategies:
• Creating a secured ecosystem
• Creating cybersecurity awareness
• Encouraging open standards
• Creating an assurance framework
Moreover, as a company, you should strengthen your cybersecurity to reduce the advantages of the attacker’s cost-benefit equations. Here are a set of initiatives which should be followed to ensure company and national security:
• Making it difficult to breach networks
• Rapidly detecting, examining and expelling attackers with WAF (AppTrana from Indusface, for example)
• Building a hostile environment
• Rapidly remediating the effects of breaches and returning to business as usual faster
• Enabling public and private sector cooperation
• Using hackers as your resource
Together with the convenience technology has brought, it has also caused a surge in cyber-threats, which tells another story. However, there is no need to stop adopting technology, but we should determine what rules will control its uses. In the same line, cyberwarfare is an uncharted area, which will raise risk situations. Undoubtedly, by increasing security and collecting intelligence, we can build new policies and strengthen security practices moving forward.
No comments:
Post a Comment