BYJOSEPH TREVITHICK

On Nov. 16, 2020, Virginia-based cybersecurity firm Shift5, Inc. announced that it had received a $2.6 million contract from the Army's Rapid Capabilities and Critical Technologies Office (RCCTO) to "provide unified cybersecurity prototype kits designed to help protect the operational technology of the Army's Stryker combat vehicle platform." The company says it first pitched its plan for these kits at RCCTO's first-ever Innovation Day event in September 2019.
"Shift5 is answering the call to arms about military weapon system cybersecurity vulnerabilities," Josh Lospinoso, the company's CEO, said in a statement. "Our products are currently deployed protecting commercial rail and aircraft, and this newest engagement will integrate our products onto military ground vehicle platforms."

US ARMY
An XM1296 Stryker Dragoon.
"Over the course of a year, Shift5 will develop, test, and refine an enhanced vehicle security system prototype and deliver a transition-ready product," the firm's press release added. "The Shift5 solution will increase the cyber survivability of the vehicle across the full lifecycle."
It remains unclear exactly how the Stryker Dragoon, also referred to as the Infantry Carrier Vehicle-Dragoon (ICV-D), or other variants in that family of vehicles are vulnerable to cyber attacks and how Shift5's kit will help protect against or otherwise mitigate those threats. We do know that the Army has been aware of these issues since at least 2018 and that the vulnerabilities are real.

US ARMY
A US Army Stryker Infantry Carrier Vehicle (ICV) variant, carrying British Army troops, fires the .50 caliber machine gun mounted in its remote weapon station during a multinational exercise in Poland.
"Adversaries demonstrated the ability to degrade select capabilities of the ICV-D when operating in a contested cyber environment," according to an annual report from the Pentagon's Office of the Director of Operational Test and Evaluation, or DOT&E, covering activities during the 2018 Fiscal Year. "In most cases, the exploited vulnerabilities pre-date the integration of the lethality upgrades."
The "lethality upgrades" referred to here center on the integration of a turret armed with a 30mm automatic cannon onto the Infantry Carrier Vehicle (ICV) variant of the Stryker, resulting in the Dragoon version. The indication here is that the cyber vulnerabilities were present in systems also found on unmodified ICVs, suggesting that the issues are, or at least were, impacted other Stryker variants, as well.
This is further supported by a brief mention of the threat cyber attacks posed to the entire Stryker family in DOT&E's annual review of activities for the 2019 Fiscal Year. "Government testing revealed cybersecurity vulnerabilities," that report said bluntly. The reports for both the 2018 and 2019 Fiscal Years both recommended actions to "Correct or mitigate cyber vulnerabilities." It's interesting to note that the 2019 Fiscal Year ended on Sept. 30 of that year, the same month that Shift5 says it first pitched its cybersecurity kits for the Strykers to the Army.
It's also still not clear who the "adversaries" mentioned in the DOT&E report for the 2018 Fiscal Year were and where those apparent attacks occurred. It remains very possible that this was a reference to Russian forces in Europe, who have been linked to cyber and electronic warfare attacks in the region, including against U.S. troops, in the past. Russia has carried out electronic warfare attacks on U.S. military aircraft and drones in Syria.
Although it seems less likely, it may also have been a reference to American troops playing the role of adversaries, also known as the Opposing Force (OPFOR), during training. We know that the Army has been increasingly working to integrate electronic and cyber warfare attacks into exercises, and rightly so as it will only become more likely that U.S. forces will experience these kinds of threats during actual operations around the world as time goes on.
The scope of what cyber warfare encompasses on the battlefield will expand, as well. As it stands now, Russia and China, among others, have demonstrated the ability to spoof, as well as generally interfere with satellite navigation systems, which could impact the ability of U.S. forces on the ground, as well as in the air and at sea, to maneuver and determine the accurate position of other friendly forces. At the very least, it could disrupt commercial support infrastructure that would be critical to any war effort.
There have also been reports for years now that some cyber warfare attacks are capable of commanding certain systems to perform various tasks, such as pointing radars in the wrong direction, or just crashing their software and disabling their hardware components, remotely. Industrial controls, in general, are a known risk. There is also the risk of vulnerabilities that a hostile actor could exploit to gain access to sensitive networks and the data therein.
A 2018 report from the Government Accountability Office (GAO), a Congressional watchdog, highlighted digital radios, radar receivers, and other wireless links as potential vectors for cybersecurity attacks on American weapon systems. These were in addition to more physical pathways to gaining access to systems or networks, such as USB and other ports on computers and other pieces of equipment, and getting hardware that has been tampered with in some way into the supply chain.
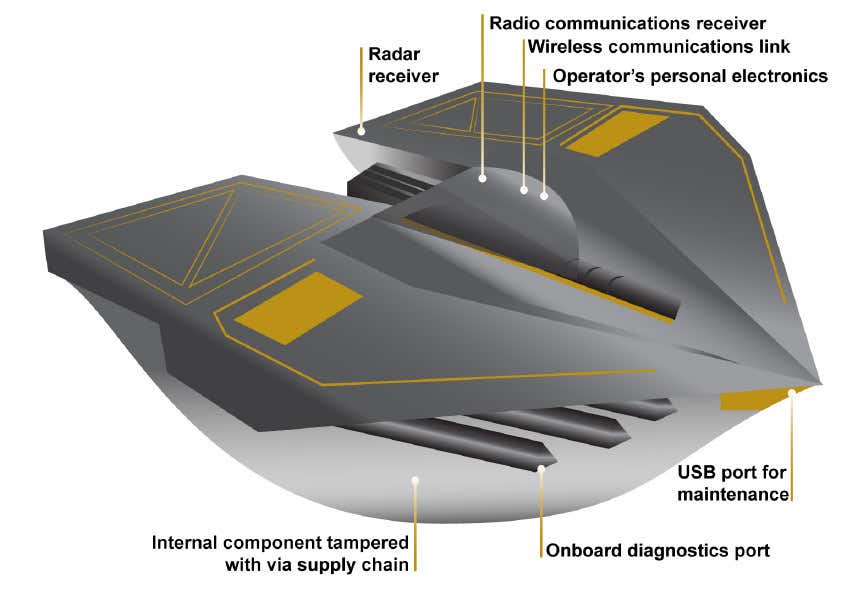
GAO
A graphic from a 2018 Government Accountability Office report showing various potential vectors for cyber attacks on a fictitious weapon system.
It's good that the Army is finally working to harden its Strykers against these kinds of threats, but how long it has taken to just begin prototyping these cybersecurity kits shows that there is still much work to be done.
No comments:
Post a Comment