Chris Nolan
Executive Summary
The SolarWinds cyber breach was likely the largest in U.S. history, though its full breadth and impact remain unknown. As early as October 2019, Russian hackers penetrated the Texas firm’s software development environment so that when the company pushed patches to its customers, it inadvertently delivered Moscow’s malware as well.1 The hackers exfiltrated data from U.S. government agencies for more than a year before FireEye exposed the operation last December.2
While it could take months or even years to remove the compromised software and implement other remediation measures, and although the costs to the U.S. government alone could be in the hundreds of millions of dollars,3 the breach was not as damaging as feared from an economic perspective, because its primary purpose appears to have been espionage. The breach did not cause large-scale business disruptions like those caused by Russia’s NotPetya attack on Ukraine in 2017. That malware spread around the world, affecting tens of thousands of companies, costing some as much as hundreds of millions of dollars.4
The digital age has increased productivity and efficiency, but many firms are struggling to manage the downside risks that accompany it. Too many companies are prioritizing short-term growth and cost-cutting at the expense of cybersecurity. As the SolarWinds breach demonstrated, one company’s cyber risk can have cascading economic and national security implications.
Twenty years ago, after a wave of corporate scandals undermined public confidence in the securities market, Congress passed the Sarbanes-Oxley Act, requiring greater corporate financial disclosures.5 The law strengthened investor protections and confidence through better accounting standards, improved internal controls and disclosure by companies, and stronger external oversight. Poor cybersecurity is today’s systemic risk, and the potential impact is even greater. Unlike the accounting malpractice and financial scandals of the 1990s and early 2000s that prompted congressional intervention, a single company with deficient cybersecurity could inflict substantial harm on the U.S. government, company shareholders (including retirees dependent on pensions), the public, and critical national infrastructure.
The insurtech firm Intangic developed a digital-risk rating system that uses a combination of financial data and externally observable malicious network activity to price actuarial risk across over 6,000 public corporations, including projected economic and shareholder value losses stemming from breach events. This memo employs the Intangic model to analyze two hypothetical breach scenarios: one targeting a large managed service provider, and a second one targeting a regional utility. The results demonstrate how the deficiencies of a single company can yield economic losses that exceed those caused by major natural disasters.
Confronting and correcting the issue of poor cybersecurity practices will require legislative and policy remedies. This memo prescribes enhanced corporate disclosures related to risk controls, cyber breaches, and vulnerabilities to improve the quality of information available to regulators and investors. Market forces can then incentivize corporate stakeholders to improve their company’s resilience and security. The goal is to minimize the likelihood of cyber breaches on the scale of SolarWinds – or worse – in the future.
UNDERINVESTMENT IN SECURITY IS CREATING SYSTEMIC RISK
Digital technology is now the most valuable asset in the world. It plays a critical role in the function and growth of companies across every industry sector. Technology giants are the most valuable companies in the world today, replacing the energy and manufacturing firms that topped the rankings 25 years ago.
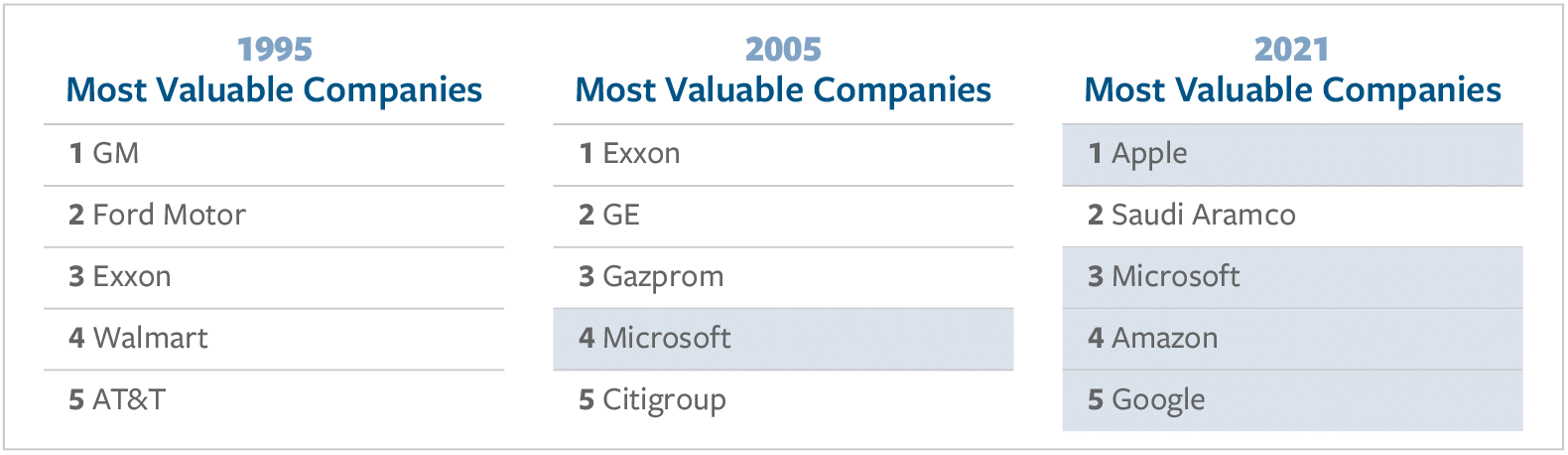
The rate of change is not slowing down. As Microsoft CEO Satya Nadella explained in January, “What we have witnessed over the past year is the dawn of a second wave of digital transformation sweeping every company and every industry.”6 For example, car manufacturing is now so dependent on advanced technology that a global shortage of computer chips at the beginning of 2021 upended production schedules and temporarily shut down some auto plants. Ford, for example, saw a 17 percent drop in production in the first quarter of 2021 due to chip shortages.7
Every company now uses advanced technology to generate more value. The combinations of hardware, software, data management tools, and other programs – collectively known as the technology “stack” – of companies today are increasingly complex. There are myriad, overlapping tools with redundant capabilities, and patches and updates are pushed out daily.
Procuring technology is the easy part. Managing it well is what separates more secure companies from their weaker peers. A misconfiguration in any one tool can create serious security vulnerabilities. Technology management and cybersecurity impact financial performance just like return on equity, return on investment, free cash flow, or any other traditional metric.
Ransomware breaches are economically and financially damaging because they impact things that directly impact the balance sheet, such as productivity and cost efficiencies. The cost of the ransomware payment – the issue that receives most of the attention – is minor compared to the cost of repairing the breach, the loss of revenue, the erosion of profit margins, and the shareholder (and reputational) losses that typically linger for several quarters or even years.8
Gaps in Cyber Risk Disclosures
In 2018, the Securities and Exchange Commission (SEC) issued guidance stating that cybersecurity risk is material to a company’s financial health and business operations, but did not require publicly traded companies to disclose cyber risks or cyber incidents.9 The guidance acknowledges that companies may require time to discern the implications of an incident, and recommended that companies that suffer a cyber breach amend prior disclosures during their investigation into the breach. In practice, however, most companies do not provide additional information in subsequent reports. As a result, it can appear to investors that a breach never happened or had a negligible impact.
The SEC guidance also recognizes that cyber policies and procedures are important elements of overall risk management. As such, the guidance encourages companies to adopt comprehensive policies, to conduct self-assessments of their compliance with their own policies, and to self-assess their controls and procedures to ensure information is provided to senior leadership for the purpose of disclosures and certifications. Yet there has never been a disclosure of this kind, which suggests that companies are not actually conducting rigorous self-assessments – or they are not reporting. On the whole, companies are not following the SEC guidance.10
Even when companies disclose breaches, they often are not fully transparent about the financial impact. Companies use terms such as “ongoing expenses” and “materially adverse impact on financial performance” in the wake of significant breach events.11 This lack of transparency limits investors’ understanding of the extent of the damage from the incident.
INSURANCE-RELATED DISCLOSURES
While cyber insurance coverage can be an important risk management tool for enterprises, many organizations have nonexistent or insufficient coverage, and underwriters struggle to price policies properly due in part to the challenge of accurately modeling the likely frequency and severity of breaches. Thus, cyber insurance cannot effectively compensate for deficient cybersecurity practices.
The Foundation for Defense of Democracies (FDD) has explored the value of cyber insurance in improving resilience and aiding recovery from cyberattacks.12 To date, however, companies affected by malicious cyber incidents have found limited success filing claims. The insurance has either been insufficient, as in the case of Norsk Hydro,13 or providers have denied claims, as in the case of Target’s $138 million claim following a 2013 breach.14 Litigation between insurers and claimants (such as Maersk, Merck, and Mondelez) over the NotPetya malware attack of 2017 also reveals the limitations of insurance in the case of attacks by nation-state actors. In general, even when insurance provides relief from a cyberattack, the payment rarely covers the damage inflicted, especially the indirect costs such as operational shutdowns and loss of potential revenue.15 In short, cyber insurance is not yet providing companies with the essential risk-transfer function that other forms of corporate insurance (such as property and casualty insurance) typically provide. This will likely change as the insurance industry’s approach to digital risk improves, including through the use of better actuarial models and more sophisticated underwriting solutions, such as parametric insurance.
Modeling Cyber Risk
Despite the rising frequency and increased costs of business-interruption events such as ransomware, technology risk remains largely unregulated. Markets and regulators need to identify objectively and transparently whether companies are properly managing digital technology and related risks.
Until now, a paucity of data on breaches has hampered cyber risk modeling. Most risk assessments are based only on disclosed cyber breaches, which account for only a fraction of total incidents. According to Mandiant’s Security Effectiveness Report, 53 percent of attacks infiltrate corporate networks without detection.16 Of the remaining 47 percent, companies disclose only those breaches in which customers’ personally identifiable information (PII) is stolen or ransomware causes an obvious disruption in service, as those are the situations requiring action pursuant to current data-breach notification laws. Companies are otherwise unlikely to volunteer information, thus preventing investors, insurers, the government, and U.S. taxpayers from getting an accurate picture of the impact.
Instead of relying on an incomplete dataset, it is possible to model digital risk based on financial disclosures and externally observable malicious network traffic. Using only publicly available information, Intangic has built a digital-risk rating system and actuarial model to estimate the economic and financial costs of cyber risks. A licensed third-party index provider audits these company risk ratings. Published results demonstrate that across every industry sector, companies with one- or two-star ratings suffer breaches more frequently than firms with four- or five-star ratings.17 This is the rating system Intangic uses in its actuarial model for insurance purposes. The individual company ratings are not public, though corporate customers have access to their own ratings. The results of the ratings have also been measured against the stock market for over four years and are published monthly in the form of a publicly available index covering the U.S., UK, and EU markets.
Intangic updates the results of these assessments every month and validates them against externally verifiable information. The company’s data science lab then runs over a million tests per month to validate the risk ranking for companies. These predictive results are measured against the following factors to demonstrate accuracy:
Negative changes in enterprise value on an overall and sector-specific basis
Negative changes in income statement, cash flow statement, or balance sheet
Probability of debt default (credit ratings)
Probability of negative earnings surprise due to poor cyber hygiene
Predictive value of the economic-loss model post-breach
Because operational performance impacts stock prices over the long run, Intangic’s cyber ratings are measured against the stock market. As of November 2020, over the past three years, companies with “good” scores on Intangic’s digital-risk rating system outperformed “bad” ones by 46 percent in the United States and by 60 percent in the European Union. The model thus enables investors to make informed financial decisions, allows insurers to price premiums based on risk, and helps companies make better decisions about their own digital transformations, including risk transfer and security expenditures.
Intangic’s ratings also serve as an early-warning system for significant cyber incidents. Companies with poor cyber risk ratings are more likely to suffer a cyberattack and are less prepared to recover from one. By detecting the highest-risk companies (those with one- or two-star ratings), the model can anticipate where remediation of vulnerabilities may be necessary to avoid a breach and how company resources can be best allocated to mitigate vulnerabilities and lower the probability of an event.
For example, for one year leading up to the SolarWinds breach announcement, Intangic’s ratings model ranked SolarWinds as a high-risk company because, relative to its peers, the company had:
high expenses related to mergers and acquisitions but low annual research-and-development spending, suggesting the company prioritized short-term growth over continued technological development, including security;
high network and technological complexity18 and weak liquidity, indicating that if the company suffered a cyber incident, it would lack the financial capacity to remediate the issue effectively; and
more externally observable malicious network activity.
For SolarWinds, in particular, the fact that thousands of companies and numerous U.S. government agencies bought, deployed, and relied upon SolarWinds software made the company an increasingly attractive target for hackers.
Operational disruption and downtime are the costliest effects of cyberattacks. When a company’s disruption causes cascading effects on its customers, Intangic’s model estimates an economic impact on par with that of recent catastrophic weather events. Such events provide an approximation of what to expect in terms of operational downtime from losses of electricity and other utilities as well as transportation and logistics services.
Studies of the impact of Hurricane Sandy in 2012 on small- and medium-sized businesses (SMBs) in New York, New Jersey, and Connecticut, and of the impact of 2017’s Hurricane Harvey on SMBs in the Houston area, show not only widespread operational disruption but also long-term costs. For example, Sandy impacted one-third of all firms in the greater New York metro area.19 Firms reporting losses due to utility disruption on average lost $5,000 per employee. Meanwhile, Hurricane Harvey cost an estimated 55,000 to 75,000 jobs over the short term,20 and half of the surveyed firms had not fully recovered one year later. Eight percent reported that their businesses would never recover, and 9 percent closed permanently.21
Like cyberattacks, extreme weather events also impact firms’ future risk management plans.22 Forty percent of firms impacted by Harvey reported increasing their savings and/or credit, a process of de-risking that negatively impacts overall GDP growth. Twenty-five percent of firms impacted by those two hurricanes increased their insurance coverage even though insurance was of little help to companies impacted by the hurricanes.23
Disruptive cyber incidents can cause similar short- and long-term damage. In fact, cyber incidents can exact an even greater economic cost than extreme weather events, because the bulk of the economic losses from weather events are from property damage.24 Intangic’s model focuses on digital assets such as software, which are much more valuable for most companies in terms of revenue generation, cost efficiency, and profit growth. The indirect effects of a cyberattack often include increased strain on the financing and credit worthiness of affected companies and increased debt. These impacts linger for at least several months and, in some cases, years following the event, whereas property damage can often be more easily remedied.
Scenario Analysis: Cascading Effects of Cyber Incidents
The following scenarios depicting hypothetical cyberattacks illustrate how a single company’s deficiencies can create systemic risks and losses. These scenarios are not improbable. Similar attacks have already occurred.
Scenario #1 – Managed Service Providers: SMBs are the source of nearly half of all private-sector jobs in the United States.25 Unlike Fortune 500 companies, which often have advanced, in-house cyber defense capabilities, SMBs usually have limited defenses.
As companies have accelerated digitization efforts in recent years, they have often outsourced information technology (IT) functions to managed service providers (MSPs), increasing their operational reliance on these third parties. Growing digital interconnectedness makes it increasingly difficult to distinguish a corporate network from that of a supplier, partner, or customer. The expansion of telework during the COVID-19 pandemic has only increased the attack surface by expanding remote access into enterprise IT networks.26
Vendors are a known risk, according to specialty insurer Beazley.27 In addition to the SolarWinds breach, several large MSPs suffered breaches within the past two years.28 In the decade-long “Operation Cloud Hopper,” Chinese hackers infiltrated MSPs to bypass the cyber defenses of dozens of companies to steal intellectual property and confidential business data.29 By compromising one MSP in New York, for example, hackers gained access to clients across the financial, telecommunications, manufacturing, automotive, energy, and other sectors.30
Unfortunately, MSPs do not always adequately protect their own technology and that of their customers. There are critical IT service providers with below-average security ratings whose vulnerabilities heighten the probability of a successful malware attack.31 This is the “third-party paradox”: The corporate drive for greater efficiency and cost savings has created additional cyber-related vulnerabilities that most companies had not considered when they elected to outsource.32
Because MSPs have privileged access to the backend IT infrastructure of the customers they serve, SMBs with strong cybersecurity can still be affected by a breach targeting their vendors. According to Intangic data, if a customer is operationally dependent upon a service provider, a disruption affecting that provider may also compromise the customer, regardless of its cyber rating.
Imagine the following:33 An MSP succumbs to phishing attacks. Once the hackers gain access to the MSP’s internal systems, the hackers inject malware into the backend systems of the MSP’s customers. This breach lasts for several months without detection, as none of the MSP’s systems detect malicious activity.
FIGURE 1: ECONOMIC LOSSES FROM DISASTERS ($ IN BILLIONS)
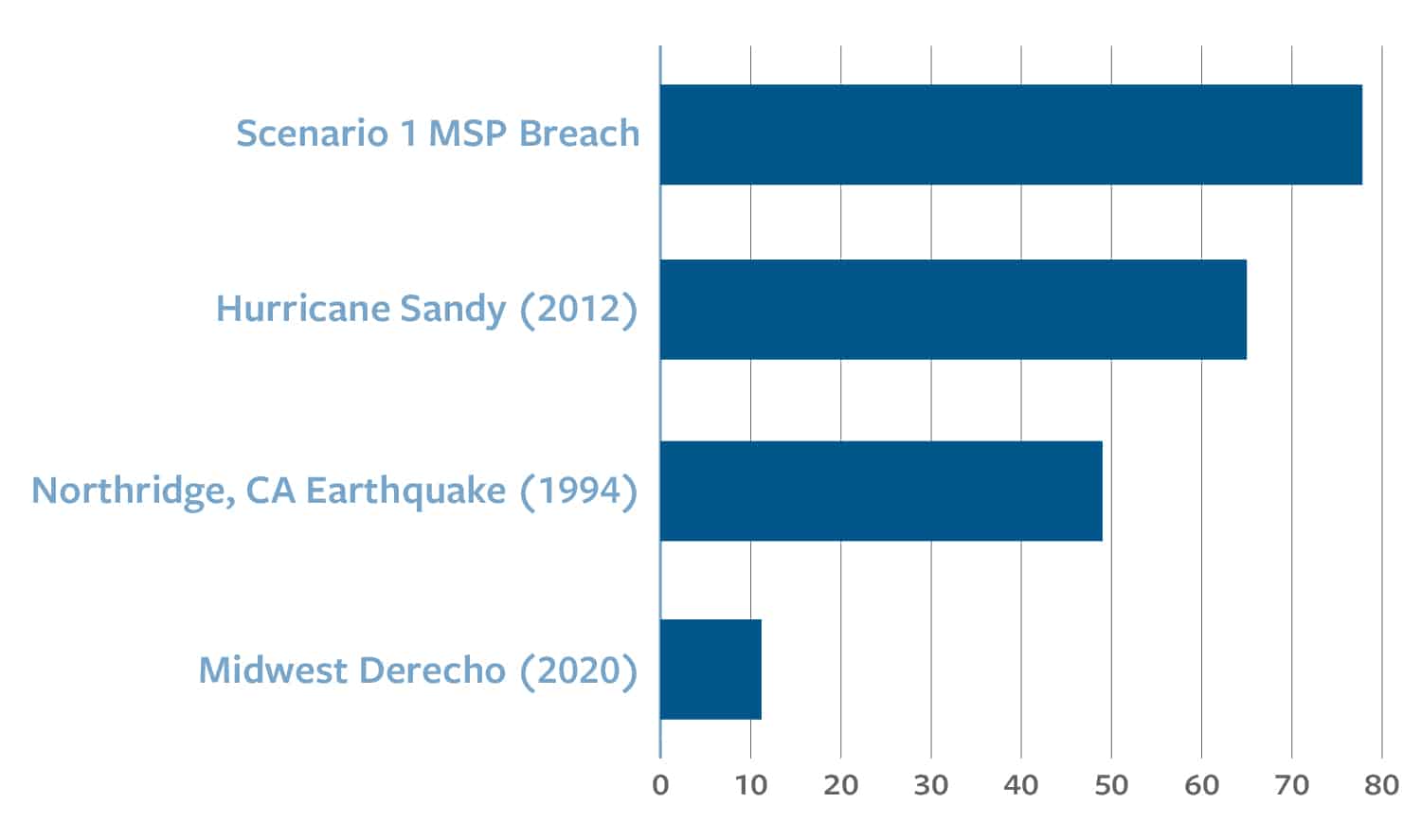
The hacking group then launches a coordinated ransomware attack on the MSP and many of its customers, resulting in significant business disruption for more than three days.34 This impacts 600 SMBs35 across the industrial, chemical, energy, IT, and communications sectors. Impacted companies span every region of the United States and every major industry sector.
In such a scenario, Intangic forecasts that the economic losses would approach $80 billion, costing tens of thousands of jobs.36 The exact figure ($77.8 billion) is equal to 31 percent of the Dow Jones Industrial companies’ annual net income.37 This estimate exceeds the economic damage inflicted by Hurricane Sandy (approximately $65 billion).38 See Figure 1.
Scenario #2 – Critical Infrastructure: The risk of a disruptive cyberattack on critical infrastructure is rising. Hackers have successfully breached electric utilities.39 Within the electricity sector, hackers are particularly focused on companies that manage generation, transmission, or distribution of energy across the country, according to industrial cybersecurity firm Dragos as well as the Government Accountability Office.40 Hackers have already developed ransomware specifically designed for industrial control systems upon which critical infrastructure often depends.41
The merging of operational technology (OT) and IT has also drastically increased the cyber threat surface for companies. OT systems are increasingly controlled by IT systems for remote maintenance of large, physical devices,42 leaving them vulnerable to insider threats and external hackers breaching the IT environment. For example, while the FBI and Department of Homeland Security confirmed that the May 2021 DarkSide ransomware attack did not breach Colonial Pipeline’s OT networks, the company “proactively disconnected certain OT systems to ensure the systems’ safety.”43 As Dragos notes, sometimes “halting operations becomes the safest choice” because of the dependency of OT systems on IT networks.44
OT systems have no built-in cybersecurity mechanisms. They often have a lifespan measured in decades rather than the months or years of IT systems. This matters because older OT systems were not designed to include cybersecurity. Indeed, no one anticipated their connection to IT systems and the wider internet. For example, 70 percent of large power transformers in the United States are at least 25 years old and were not designed for the digital age.45
With the increased adoption of Internet of Things devices by utility companies, industrial control systems have become more connected and thus more vulnerable to attack. The rollout of new digital tools for managing both the grid and downstream digital services for customers have introduced greater complexity and vulnerability to IT networks. The greater the number of direct customer-interface points, the more potential entry points for threat actors.
Electric utilities generally have stronger cybersecurity than other sectors,46 particularly municipally owned water utilities, which are notoriously vulnerable.47 Electric utilities, however, feel the same business pressures to expand profit margins and to grow through acquisition. Acquisition increases the probability of attack, because the process of merging the companies’ networks tends to have an adverse impact on cybersecurity in the short term.48
Security teams across the utility sector are often stretched thin as they cope with the expanded threat environment that comes with not only the merging of OT and IT, but also the risks that come with a remote workforce. In short, while the cyber defense capabilities of companies in the electricity sector are often more sophisticated than those of their peers in other sectors, there is still a range of capabilities, and some companies are less secure than others.49
It is not difficult to imagine a major regional electric utility in the United States making a series of choices that puts it at increased risk of an attack with economically devastating consequences. Such a company might have long struggled with its digital transformation process and the merging of OT and IT. With a short-term-oriented business strategy, its CEO and board might pursue growth through acquisition to pad the balance sheet, acquiring a smaller regional competitor. While integrating the complex IT and OT systems of the acquired company’s network and getting a handle on new digital tools, an overwhelmed security team might fail to implement security patches.
During this period, a sophisticated hacker group might detect vulnerabilities in the company’s cyber defenses and launch a campaign. If the hackers obtain the login credentials of a key employee, they would gain administrator-level access to all internal network functions, including OT. The hackers could then launch a business-disruption attack on the regional utility, paralyzing its internal systems, including the command-and-control function for the grid itself. Even if the company were able to regain control of the network, repel the hackers, and restore operations relatively quickly, Intangic projects that a breach that disrupts power generation across the grid for five days would cause an economic loss of $193.5 billion.50 This is equivalent to approximately 30 percent of the Department of Defense’s 2021 budget.51
FIGURE 2: ECONOMIC LOSSES FROM DISASTERS ($ IN BILLIONS)
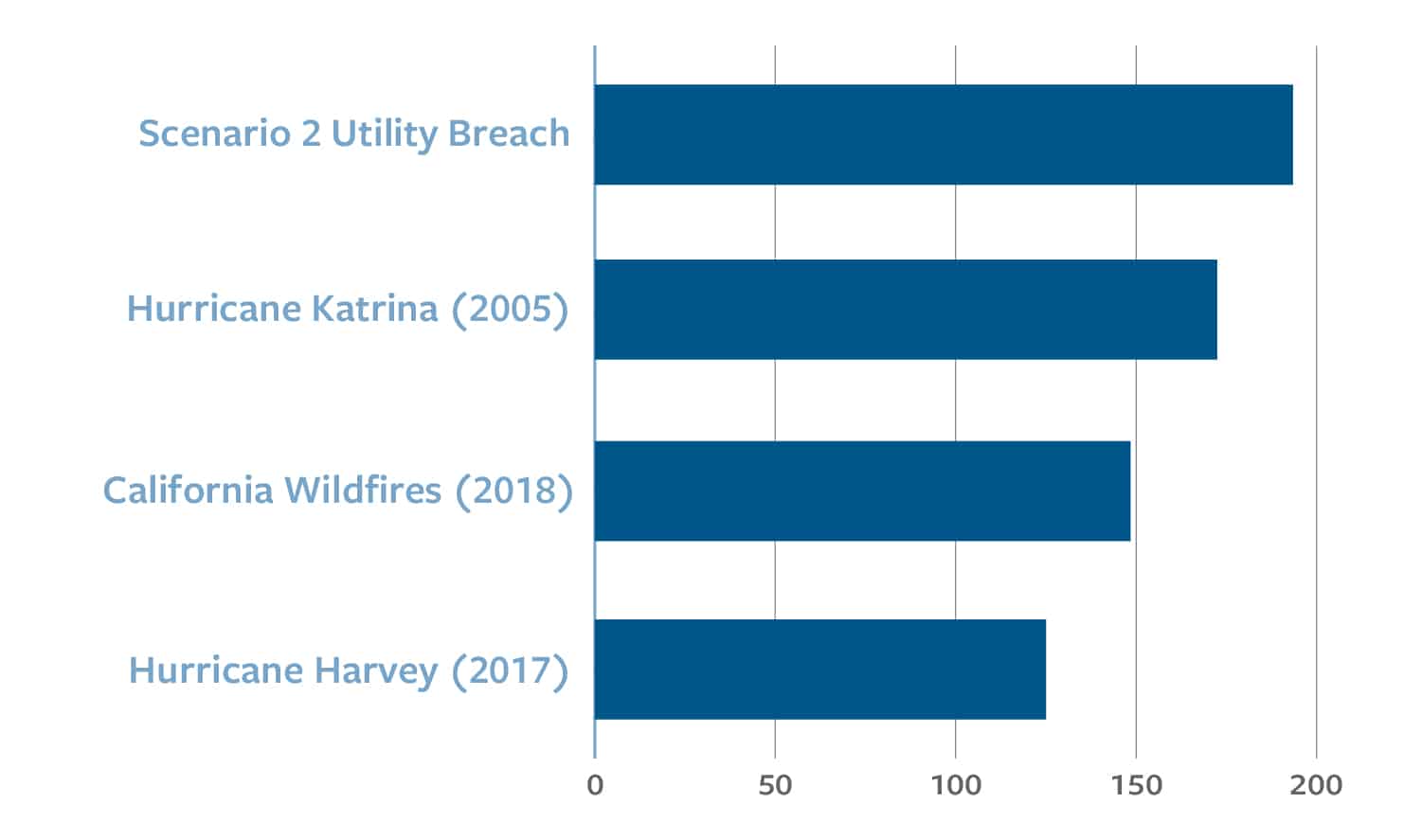
Disruption of a major regional electric utility would likely affect 1,500 SMBs across sectors ranging from healthcare and energy to industrials. The impacted area would depend on the location of the utility but could cross multiple state lines. More than 100,000 jobs might be lost as a result.52
Recommendations
Improving poor cybersecurity practices will require comprehensive legislative and policy remedies. Greater disclosure of cyber breaches and vulnerabilities would improve the quality of information available to regulators and investors about market risks. This transparency would increase investor confidence in the ability of public companies to protect their most valuable assets – technology and intellectual property. Greater transparency would also help address systemic risk and strengthen security controls, enhancing national resilience against a range of cyber threats. As with all regulation of industries, the government will need to determine the right combination of requirements and incentives to achieve greater transparency regarding the economic costs of cyber incidents. The following recommendations focus on requirements, acknowledging that tax or other incentives may be necessary to encourage the adoption of best practices. Transparency alone will not eliminate cyber breaches, but better disclosure will reduce their frequency and can lessen the severity of breaches when they occur.
Pass a National Breach-Notification Law: One year ago, the congressionally mandated Cyberspace Solarium Commission (CSC) concluded that, inter alia, Congress ought to pass a national data-breach notification law. The commission observed that the current “patchwork” of state laws is not serving the American people, and that a federal law (which supercedes state laws) would “standardize consumers’ expectations and provide regulatory certainty” to businesses.53 Currently, breach-notification laws focus on notification of customers when PII is compromised. Breaches of this nature, however, represent a fraction of total breaches. As noted, ransomware attacks rarely result in the compromise of PII, so under current law, many companies need not disclose being the victim of a highly disruptive attack. For example, few of the 100 companies affected by the SolarWinds breach need to answer to either regulators or customers. Without a federal breach-notification law that includes disruption as a criterion for disclosure, American citizens may never understand the full economic effects and market impact of the breach.
Amend Sarbanes-Oxley to Include Cybersecurity Reporting Requirements: Congress should amend Sarbanes-Oxley to codify and expand upon the SEC’s 2018 guidance, specify corporate responsibility requirements for cybersecurity, and require management assessments of cyber risk.54 The CSC also recommended codifying this SEC cybersecurity language. Using Sarbanes-Oxley as a guide, mandating self-disclosure of vulnerabilities can incentivize companies to re-examine their own security controls just as Sarbanes-Oxley forced companies to re-evaluate financial controls.55 The new language should require disclosure of the financial and operational impact (in dollar terms) of breaches when they occur.
Require Dollar-Based Risk and Breach Disclosures: Dollar-based breach disclosures should be required as part of any mandatory breach notification. Financial and economic loss estimates should be provided in the reporting periods immediately following breaches.
Dollar-based risk disclosure should also be part of a company’s proactive disclosure of risk factors. Risk assessments alone are not sufficient to protect investors or provide market-based incentives for companies to achieve consistently higher levels of security. Rather, when companies disclose financial estimates associated with risks – as is consistent with the practice for any significant financial risk – investors better understand how well companies are managing risk. This transparency will help create market incentives for companies to invest in security. Such disclosures would also help investors understand which losses may be covered by cyber insurance, analogous to how a company would disclose dollar-based costs stemming from damage from other unforeseen events.
Require Third-Party Cyber Assessments: By using available technologies such as security validation, it is possible to assess the general cyber health of any company in real time. Such an assessment can identify not only what security controls exist but also how effective the controls are at protecting a company’s digital assets. The disclosure of security controls and their effectiveness and related weaknesses is already recommended in the 2018 SEC guidance and should be mandated. These disclosures should occur quarterly to reflect the rapidly changing nature of corporate IT networks. The combination of mandatory disclosures and third-party assessments would parallel quarterly financial reporting coupled with external credit ratings that help investors make informed decisions.
Provide Cyber Hygiene Guidance for SMBs: Poor technology management leads to underperformance in the market. This is costly for investors and businesses alike. SMBs, however, may not have in-house cybersecurity expertise. The S. government, private cybersecurity firms, risk management firms, and cyber insurers should offer clear cyber hygiene guidance to SMBs that explains things such as National Institute of Standards and Technology (NIST) security controls56 in terms these businesses can easily understand. Evaluating SMBs’ implementation of this guidance should become part of third-party cyber assessments.
Conclusion
Cyber vulnerabilities pose a systemic risk to the U.S. economy. Through the right mix of policy and standard-setting, the U.S. government can help create a market with more informed risk-taking and more resilient companies. With better information, market forces can incentivize investments in security and better technology management to reduce risk. It is possible to improve the functioning of the insurance market and equip investors with the information to reward good, and punish poor, cyber risk management. To do so, the market needs dollar-based estimates of digital risk. Collectively, information from independent external assessments, disclosures from companies of cyber breaches and risk controls, and more transparency paint an accurate picture of this risk. The ultimate goal is to incentivize enterprise cyber resilience and, by extension, create greater national resilience against all forms of cyber threats.
Appendix: Objective Metrics With Dollar Value
For the scenarios included here, Intangic used its actuarial model to calculate the economic impact of hypothetical incidents. Previously, Intangic’s model accurately predicted the financial and economic impact of operational disruption. The model wields externally verifiable data, including market and financial results. It has proven accurate in distinguishing between high- and low-risk companies in all industries in the United States, United Kingdom, and European Union.
For example, before Pitney Bowes suffered a significant (over three-day-long) ransomware attack in October 2019, Intangic (then Cyberhedge) rated the company as a two-star. Immediately following the breach in October, the Intangic model estimated the attack would result in a $25 million to $35 million operational and financial impact on the company. Pitney Bowes then disclosed a $29 million hit to free cashflow and a $19 million reduction in earnings before interest, taxes, debt, and amortization (EBITDA) in February 2020.57
Travelex is another example of the Intangic model’s accuracy in predicting financial and economic losses. A cyberattack stopped Travelex’s operations in late 2019. Due to loss of cash, the company never fully recovered and filed for bankruptcy. On January 10, 2020, Intangic projected $450 million in market losses. One month after the breach, Travelex announced that it had lost $443.8 million.58
In February 2020, after ISS World suffered a ransomware incident, the company’s management sought to reassure investors of the event’s limited impact, noting there was “no indication that any customer data or systems have been breached.” Operational disruptions such as ransomware, however, are more financially costly and take longer to recover from than customer-data breaches. At the time, Intangic (then Cyberhedge) warned its clients that the impact of the incident would have “little to do with customer data loss and everything to do with business disruption.”59
Six months later, the reported damage exceeded one-third of the company’s annual operating income. After six months, the company announced that it had regained a “vast majority” of its operations and disclosed the financial cost of the attack.
In February 2020, Intangic projected $356 million in economic losses resulting from the breach. In June 2020, ISS World disclosed $255 million in losses, with additional costs likely in 2021 as IT assets are rebuilt.60
These ransomware events share two key similarities:
The cost of repairing systems after a breach is always much higher than initially estimated.
The damage suffered by companies and their shareholders is much greater than the direct costs such as software repair and replacement, which companies normally highlight. These costs are a fraction of the true economic and financial losses caused by operational disruption.
No comments:
Post a Comment