Fast Facts
Federal IT systems and our nation's critical infrastructure are at risk of attack from malicious actors, including those acting on behalf of other nations. Such attacks could result in serious harm to human safety, national security, the environment, and the economy.
The federal government should:establish a comprehensive cybersecurity strategy
mitigate global supply chain risks
address the federal cybersecurity worker shortage
ensure the security of emerging technologies
We’ve made 335 public recommendations in this area since 2010. Nearly 60% of those recommendations had not been implemented as of December 2022.

Highlights
Overview
We have made about 335 recommendations in public reports since 2010 with respect to establishing a comprehensive cybersecurity strategy and performing oversight. Until these are fully implemented, federal agencies will be more limited in their ability to protect private and sensitive data entrusted to them. For more information on this report, visit https://www.gao.gov/cybersecurity.
Develop and Execute a More Comprehensive Federal Strategy for National Cybersecurity and Global Cyberspace
The White House’s September 2018 National Cyber Strategy and the National Security Council’s accompanying June 2019 Implementation Plan detail the executive branch’s approach to managing the nation’s cybersecurity. In September 2020, we reported that the strategy and implementation plan addressed some, but not all, of the desirable characteristics of national strategies. In June 2021, the Senate confirmed the first National Cyber Director to head the Office of the National Cyber Director and serve as the principal advisor to the President on cybersecurity policy and strategy.
Extent to Which National Cyber Strategy and Implementation Plan Addressed the Desirable Characteristics of a National Strategy
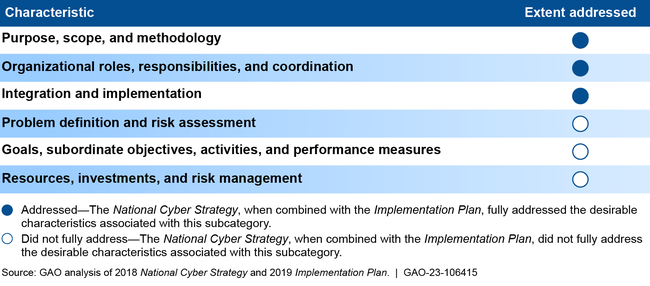
➢We recommended that the National Security Council work with relevant federal entities to update cybersecurity strategy documents to include goals, performance measures, and resource information, among other things. As of August 2022, according to the Office of the National Cyber Director, the development of a national cybersecurity strategy by the administration is underway.
Mitigate Global Supply Chain Risks
Federal agencies face numerous information and communications technology (ICT) supply chain risks, which could lead to disrupted mission operations, theft of intellectual property, and harm to individuals. In December 2020, our review of 23 civilian agencies found that none had fully implemented all of the seven foundational practices for supply chain risk management and that 14 had not implemented any of the practices.
Extent to Which the 23 Civilian Agencies Implemented Information and Communications Technology (ICT) Supply Chain Risk Management (SCRM) Practices
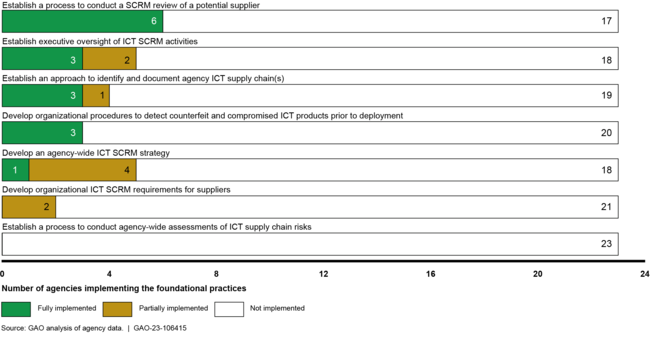
➢We recommended that the 23 agencies fully implement foundational practices in their organization-wide approaches to ICT supply chain risk management.
Develop a Government-wide Reform Plan that Addresses the Cybersecurity Workforce Shortage
In April 2020, we examined the extent to which reform plans from the Office of Management and Budget (OMB) and lead agencies addressed key practices for effectively implementing government-wide reforms such as those addressing the cybersecurity workforce shortage. We found that OMB and the Department of Homeland Security (DHS) partially addressed most key practices, including training employees to fill vacant cybersecurity positions and streamlining hiring processes. However, neither agency had established a dedicated implementation team or a government-wide implementation plan, among other practices.
Extent to Which the Government-wide Plan to Solve the Cybersecurity Workforce Shortage Addressed Key Reform Practices

➢We made several recommendations aimed at addressing continuing cybersecurity workforce challenges, including developing a government-wide workforce plan and related supporting practices. Government-wide leadership responsibility for cyber workforce issues transitioned in 2022 from OMB and DHS to the Office of the National Cyber Director. The office has committed to developing a national strategy that addresses key issues.
Ensure the Security of the Emerging Technologies
Secure Internet-connected Devices
The nation’s critical infrastructure sectors rely on electronic systems, including Internet of Things (IoT) and operational technology (OT) devices and systems. In December 2022, we reported that the Departments of Energy, Health and Human Services, Homeland Security, and Transportation had cybersecurity initiatives underway intended to help protect three sectors. However, none of these agencies developed metrics to assess their efforts to mitigate sector risks or conducted IoT and OT cybersecurity risk assessments.
Overview of Connected IT, Internet of Things (IoT), and Operational Technology
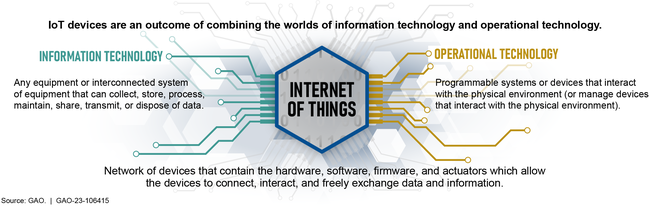
➢We made eight recommendations to the Departments of Energy, Health and Human Services, Homeland Security, and Transportation to establish and use metrics to assess the effectiveness of sector IoT and OT cybersecurity efforts and evaluate sector IoT and OT cybersecurity risks.
Quantum Computing Major Cybersecurity Risks
Quantum technologies collect, generate, and process information in ways existing technologies cannot. We reported in September 2022 that quantum technologies could dramatically increase capabilities, including high-value applications in security and cryptography. However, such technology could create major cybersecurity risks such as a full-scale quantum computer to breaking standard encryption technologies. Consequently, the federal government’s cybersecurity infrastructure will need to evolve to address such threats.
For more information about this Snapshot, contact: Marisol Cruz Cain, Director, Information Technology & Cybersecurity, cruzcainm@gao.gov, (202) 512-5017.
Full Report
No comments:
Post a Comment