DDoS attacks have increased in the past year, mainly targeting railways, and ransomware is the most common type of cyber attacks, the European Union Agency for Cybersecurity (ENISA) finds in its first cyber threat landscape report dedicated to the transport sector. The rise in DDoS attacks is primarily related to the Russian war in Ukraine, where cyber attacks on railway operators on both sides took place.
The report covers the period of January 2021 to October 2022, in which 21 incidents targeting the railway sector were analysed, out of a total of 98 cyber attacks. The data collection and analysis primarily focusses on incidents observed in EU member states, but also around the world.
Across all subsectors in transport, authorities and bodies were being targeted, 38 per cent of the incidents targeted transport authorities. In the railway sector, however, incidents almost exclusively targeted railway undertakings and infrastructure managers. The category ‘all transport’ in the figure below refers to attacks that target either all four sectors or, more commonly, ministries of transport.
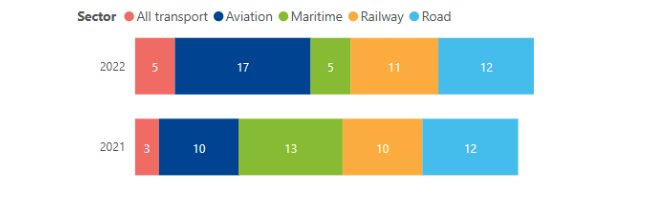 Annual observed incidents in each sector (January 2021 to December 2021, January 2022 to October 2022), source: ENISA
Annual observed incidents in each sector (January 2021 to December 2021, January 2022 to October 2022), source: ENISAThe total amount of reported cyber attacks grew slightly from 2021 to 2022, but ENISA notes that this does not necessarily mean that the number of attacks has actually increased. The change could be (partly) due to the sector maturing in terms of incident detection and reporting. This could be related to the effect of a legal obligation to report incidents under the NIS directive and/or national regulations.
The 98 analysed cyber attacks are also by no means a complete list of all incidents that occurred in this period, the actual number would be much higher. In general, cyberattacks are rarely reported, especially those with non-significant impact or near misses. Most organisations prefer to deal with the problem internally and avoid bad publicity, notes ENISA, and it is very hard to keep track of the actual number of attacks.
Regarding the questions of who is behind cyber attacks, ENISA reports that cybercriminals are responsible for the majority of attacks on the transport sector, accounting for 54 per cent, though for railway or other subsections specific, the report does not lay out the actors of the attacks in percentages.
Main attack types targeting railways
The majority of the attacks observed in railway targeted the IT systems of railways, relating to passenger services, ticketing systems, mobile applications and display boards, for example. These caused some disruptions due to the unavailability of these services, but mostly did not cause train operations itself to be shut down.
Ransomware and data-related threats are the two main threats targeting the railway sector, with 45 and 25 per cent, respectively. Ransomware has been steadily increasing according to ENISA, and the transport sector has been affected similarly to the other sectors. The next most prevalent type in rail are DDoS attacks, with an increasing rate comparing 2022 to 2021. Compared to the other types of transport, DDoS attacks occurred the most in rail in the incidents analysed by ENISA.
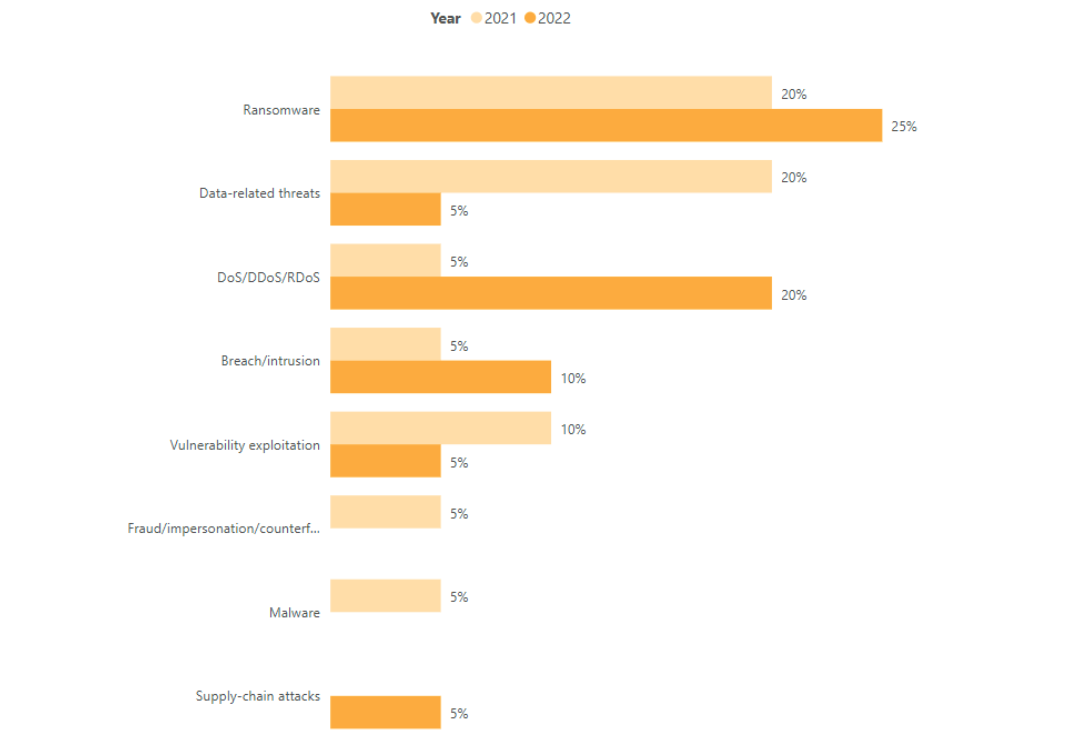 The type of cyber threats of the analysed attacks targeting the railway sector per year, source: ENISA
The type of cyber threats of the analysed attacks targeting the railway sector per year, source: ENISANotable ransomware attacks include the targeting of Swedish regional transport operator Skånetrafiken in August 2021, which caused the site and app to be down for several hours. It was not the first ransomware attack for the operator.
In March 2022, Italian state railways Ferrovie dello Stato Italiane faced a ransomware attack, resulting in customers not being able to buy tickets. The only cases were Operational Technology (OT) systems and networks were affected, which are critical for the rail operations itself, were either when entire networks were affected or when safety-critical IT systems were unavailable.
This was the case when one of Danish train operator DSB’s ICT service providers faced an alleged DDoS attack in October 2022. This resulted in service disruptions on the Danish railway network. The incident reportedly affected the accessibility of a key safety-critical IT system, thereby disrupting DSB operations for several hours that day.
Cyber attacks rise related to Russian war in Ukraine
DDoS attacks, an attempt by cybercriminals to send an overwhelming amount of requests to websites to make them inaccessible to users, in general were on the rise in 2022, reaching one fifth of the attacks on the railway sector.
This is primarily due to the increased ‘hacktivist’ activity following Russia’s invasion of Ukraine. Hacktivist groups with pro-Russian or anti-NATO sentiments have been conducting DDoS attacks against railway companies, mainly in Eastern Europe. In April 2022 pro-Russia hacker group Killnet claimed to be behind attacks on Romanian government websites, including railway transport operator CFR Calatori. In June 2022, Killnet claimed to have disrupted the website of Lithuanian Railways, preventing passengers from purchasing train tickets online, and in August that year the group claimed responsibility for attacks to more than 200 state and private Estonian institutions, including Estonia Railway. Latvian passenger train company SJSC faced DDoS attack in June 2022, also likely by pro-Russian hacktivists.
On the opposing side, anti-Russian hackers also targeted railways, with the specific goal to disrupt Russian troop movements, many of which occurred via railways. Hacktivists launched a ransomware attack on the Belarusian state-run train company in January 2022. Though this was before the start of the invasion into Ukrainian territory, Russian troops were already spotted near the border and were stationed in Belarus.
An internal doc requesting to replace outdated workstations in the Belarus Railway that still work on Windows XP… pic.twitter.com/wtqpErfPFK
— Belarusian Cyber-Partisans (@cpartisans) January 25, 2022
The hacker group named Belarusian Cyber-Partisans deployed modified ransomware to bring down the railway system and encrypted servers, databases and workstations belonging to the Belarusian railway service. The railway’s online ticketing system was successfully taken down for a while, and the group posted images of having accessed the backend of Belarusian Railway systems. The group called for the release of 50 political prisoners detained in the midst of the country’s protests against dictator Alexander Lukashenko, as well as a commitment from Belarusian Railways to not transport Russian troops.
Anonymous-linked group GhostSec claimed to have accessed an IT system of Russian metro safety systems provider Metrospetstekhnika in April, 2022. According to ENISA, increased hacktivist activity targeting the transport sector is likely to continue, as well as an increasing rate of DDoS attacks targeting railways and the transport sector in general.
Stealing of data
There were also cases of data thefts among railway operators, where for example personnel and/or medical records were stolen. These are often closely linked to ransomware, as a ransomware attack is often followed by data leakage or exfiltration. For example, the case of US rail freight operator OmniTRAX which faced a double-extortion ransomware attack. Also Metropolitan Transportation Authority (MTA) and Norfolk Southern Railroads in the United States were targeted for data theft, as well as UK operator Merseyrail and Danish regional operator Lokaltog A/S.
Cyber attacks usually come as a surprise, and the more vulnerable a system, the more chance of success. Sometimes, vulnerabilities in a system are however pointed out before it is too late. For example, Canadian transportation agency Metrolinx temporarily took down their website in December 2021 as a precautionary measure after being informed by the federal government about a cyber vulnerability. In January 2022, an anonymous hacker reported a vulnerability impacting the Swiss national railway system and potentially allowing access to customers’ personal data.
The report makes clear that there are different types of cyber attacks that can negatively impact railways, and they are likely to increase, warns ENISA. The agency deems that the significant increase in hacktivist activity, which followed Russia’s unprovoked invasion of Ukraine, and the increasing rate of DDoS attacks are highly likely to continue. Though currently, most cyber attacks had little impact on train services itself, it also foresees that ransomware groups will likely target and disrupt Operational Technology (OT) systems in the foreseeable future, partly due to the ongoing digital transformation in the transport sector and the increased connectivity between IT and OT networks.
No comments:
Post a Comment