SYDNEY J. FREEDBERG JR.

Robert Joyce, director of cybersecurity at the National Security Agency (NSA), speaks during a Senate Armed Services Subcommittee hearing in Washington, D.C., U.S., on Wednesday, April 14, 2021. (Al Drago/Bloomberg via Getty Images)
WASHINGTON — Russia’s invasion of Ukraine last year sent American tech firms scrambling to shore up their operations, especially those with workers in danger zones. But a Chinese invasion of Taiwan would have even more chaotic consequences for which businesses should start planning today, said the National Security Agency’s director of cybersecurity, Rob Joyce.
“We had a lot of companies who had to had to endure hard decisions and take rapid action at the time of the invasion” in February 2022, Joyce said at the Center for Strategic & International Studies this morning. “Often they had people in Ukraine that were now going to be in a war zone and they had to think about getting them out. They had Russian or Ukrainian sysadmins [systems administrators], and they had to think about what privileges they wanted them to have. They had network segments in Russia or Ukraine and they had to think about whether they severed that or firewalled that. They had to think about whether they just pulled all the way out of their Russian businesses and what the implications were.”
Joyce said for all that complexity, a Chinese invasion of Taiwan would even worse, considering “how [much] more intertwined” Taiwan is with the global economy and how much more of a cyber threat China may pose compared to Russia.
“That’s a really hard problem,” he emphasized, “and you don’t want to be starting that planning the week before an invasion when you’re starting to see the White House saying it’s coming. You want to be doing that now and buying down your risk and making those decisions in advance — and it’s really hard, so tabletop it and see where your pain points are.”
Ukraine is a major global supplier of grain and a throughway for Russian oil and gas, which continues to flow through pipelines to Europe right across the war zone, so the war had global economic impacts, including potential famines in poor countries. Ukraine is also a significant source of cyber crime, much of it historically aligned with Russia, so conflicts between formerly friendly Russian and Ukrainian hackers have disrupted the criminal world.
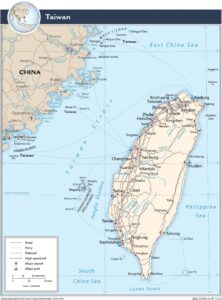
But Taiwan is the global hub of semiconductor manufacturer, producing 60 percent of all chips and 90 percent of the most advanced ones, with a GDP three times larger than Ukraine’s. And unlike Ukraine, Taiwan’s an island, with no neighbors to drive or take the train to when companies need to evacuate people and assets. Any movement on or off Taiwan would have to pass through disputed waters where Chinese forces can attack, while anything leaving Ukrainian territory headed west has legal sanctuary as soon as it crosses the land border.
Major transportation routes on and off Taiwan (Source: CIA World Factbook)
And China is a much bigger country than Russia, with more GDP and more technical talent to deploy. “The threat of China is capacity and resources,” Joyce said. “We’re used to kind of a narrative of this unsophisticated, loud threat — and yes, there is an enormous amount of unsophisticated, loud Chinese threat. But there are also elite units that have tools and tradecraft that [are] very sophisticated…. That’s the concern, [if] they’re able to scale and use that elite set of concepts and tools at a much bigger pace.”
Despite the differences, Joyce said “there’s a lot of lessons to learn from how the Ukrainians protected themselves” that apply to other scenarios, including US firms operating on Taiwan.
“They were very resilient. How did they get that? They got there because they practiced for years,” he said. “They’ve gotten to the point where, you know, the Ukrainian sysadmins knew they had to have backups, and when they got a [data destroying] wiper virus they shrugged their shoulders, they cleaned the machine, they reloaded from backup and they moved on.”
What’s more, he said, “around the invasion … they got an uplift from the US government providing resources, but [also] a lot of pro bono industry support, to make them much harder targets.” One of the most important cyber-maneuvers: moving activity off of data centers physically on Ukrainian territory to cloud servers in the West. So instead of being on servers amidst the war zone, with a handful of Ukrainian systems administrators struggling with power outages, bombardments, and even potential takeover by Russian troops, Ukrainian networks increasingly ran off servers in sanctuary, on Western territory with vast teams of Western government and industry cyber defenders.
“You now went from two people who were maintaining and operating those servers to teams of hundreds or thousands,” Joyce said. What’s more, he said, those centralized Western cloud providers were easy points of contact for the NSA and other government backup — support that could never have found its way to all the individual small operations previously scattered across Ukraine.
No comments:
Post a Comment