Introduction
Digital technologies offer an array of opportunities to benefit electricity consumers, utilities and the system as a whole, including improved efficiency, cost savings and shorter outage times. They could also help to accelerate clean energy transitions. Connected devices and the Internet of Things, together with other smart grid technologies, can unlock larger demand response resources, improve energy efficiency, and facilitate the integration of higher shares of variable renewables in a cost-effective and secure manner.
The number of connected devices (e.g. smart thermostats and appliances) is growing rapidly, with the global stock projected to double over the next five years to reach 30-40 billion devices by 2025.
However, the growth in connected devices and distributed energy resources – such as distributed generation, electric vehicles and behind-the-meter storage – is expanding the potential cyberattack##anchor1## surface of electricity systems. Increased connectivity and automation throughout the electricity system could also make them more vulnerable to cyberattacks.
A successful cyberattack could trigger the loss of control over devices and processes, in turn causing physical damage and widespread service disruption. In addition to the impacts on critical services, households and businesses that rely on electricity, an attack could result in millions or even billions of dollars in damages for electric utilities, including the costs of dealing with the cyberattack (i.e. detection, investigation, containment and recovery) and its consequences (e.g. from business disruption, information loss, revenue loss and equipment damage).
Digitalisation brings many benefits to the electricity system, but raises risks to cybersecurity
Enhancing resilience
Cyberattacks are among the top ten global risks in terms of likelihood and impact according to the World Economic Forum’s Global Risk Report 2020. For electricity systems, the threat of cyberattack is substantial and growing, and threat actors are becoming increasingly sophisticated at carrying out attacks – both in their destructive capabilities and their ability to identify vulnerabilities.
However, measuring and tracking the risks and impacts are difficult. The first hurdle is the lack of comprehensive publicly available data on cybersecurity incidents. The second is that many incidents may not be reported at all – even to regulators or other authorities – and some attacks may even go undetected. And third is the difficulty of overcoming major differences in scope and definitions, such as what constitutes an “incident” or “attack”. For example, a global database tracking “significant” cyber incidents shows the number of incidents has increased dramatically in recent years, including in the electricity sector.
The substantial and growing threat of cyberattack warrants strong action to enhance resilience
Significant cyber incidents worldwide, 2006-2019Open
Other significant incidents
Disruptions to electricity systems because of cyberattacks have so far been small compared to other causes, such as power outages from storms, equipment failure or operational errors. The 2015 attack on the western Ukraine power grid was the first confirmed cyberattack specifically against an electricity network with impacts on system availability. Attackers accessed and manually switched off substations, resulting in 30 substations going offline and 225 000 people losing power. Despite the limited extent of disruption to date, there are plausible scenarios where cyberattacks could cause substantial harm to electricity systems.
While full prevention of cyberattacks is not possible, electricity systems can be designed to be more cyber resilient – to withstand, adapt to and rapidly recover from incidents and attacks, while preserving the continuity of critical infrastructure operations. The capacity to adapt to new technologies – as well as to new risks and threats – is key. Policy makers, regulators, system operators and industry across the electricity value chain all have important roles to play in enhancing the cyber resilience of the system.
The fundamental principles of cyber resilience, such as embedding a culture of cyber resilience within the organisation and implementing risk management strategies, are generally applicable across a variety of sectors and industries. However, they need to be tailored to account for sector-specific characteristics and needs. In the electricity sector, these include: real-time requirements for and expectations of very high availability
interdependencies and cascading effects within and across systems
a mix of new technologies and legacy assets with long lifetimes.
Enhancing resilience in the electricity sector should also be considered within the broader context of enhancing resilience across all other critical infrastructure and services, including water, transport, ICT, health and finance.
Enhancing the cyber resilience of electricity systems is a continuous process generally involving several stages: 1) identifying and assessing risks and preparedness; 2) implementing a risk management strategy to prioritise risks and actions; 3) in the event of an attack, following robust response and recovery procedures; 4) documenting and incorporating lessons learned from past incidents; and 5) sharing knowledge with other stakeholders. Because cyberthreats are constantly evolving, all organisations need to continuously monitor and evaluate their vulnerabilities and risk profiles and take appropriate action. For example, some organisations may need to exercise effective threat hunting and cyberthreat intelligence activities to prepare for high-end threats from highly capable and motivated attackers.
Enhancing cyber resilience is a continuous process, and the collective responsibility of all stakeholders across the electricity value chain
Cyber resilience activity needs to be integrated into the culture of the organisation and rather than being considered as a separate, technical issue. Without this integration, organisations could fail to address the challenges that come with digital transformation in a holistic, appropriate and consistent way.
In the event of an attack, it is crucial that organisations follow robust response and recovery procedures while documenting and incorporating lessons learned from past incidents. Cyber resilience is a combination of preventive and corrective measures, building on lessons learned after a cyberattack. Reflecting on past attacks can inform the implementation of new measures, as well as reinforce or redesign existing ones as needed. Equally important is communication with external stakeholders in order to improve the threat awareness of the community and to help detect blind spots and vulnerabilities.
Actions by policy makers, regulatory authorities, regulated entities and other stakeholders can enhance cyber resilience across the electricity system and ensure appropriate measures are implemented. Many tools and frameworks are available to provide guidance on and support resilience-building efforts.
Cyber resilience needs to be integrated into organisational culture
Overview of potential actions to enhance cyber resilience
Stakeholder
Potential actions to enhance resilience
Utilities Incorporate cyber resilience into the organisational culture and integrate cybersecurity considerations into enterprise risk management frameworks.
Identify and assess risks and implement a risk management strategy to prioritise areas of action.
Implement robust response and recovery procedures to help maintain operations in the event of a cyberattack, with clearly allocated responsibilities.
Improve existing measures and implement new ones based on lessons learned internally from past incidents, and from external organisations via information sharing and analysis centres (ISACs) or knowledge-sharing platforms.
Exercise threat hunting and cyberthreat intelligence activities to prepare for high-end threats from highly capable and motivated attackers.
Equipment suppliers Participate in certification programmes to increase trust and security in products, processes and services.
Focus cybersecurity standards on risk management approaches and the processes by which security is maintained once equipment is commissioned.
Promote co‑operation to avoid potential fragmentation that might be expected from having different regulators and supervisory bodies.
Policy makers and regulators Understand cybersecurity risks and communicate effectively to raise awareness.
Apply or adapt existing tools and guidance for key stakeholders.
Exercise caution when using assessments to compare different organisations.
Develop policies that foster sector-wide collaboration and response procedures.
Set up research partnerships with industry and academia to foster R&D on cyber resilience in electricity.
Facilitate and incentivise the sharing of best practices and vulnerabilities through workshops, bulletins, training, on-line communities, etc.
Provide direction and assistance in setting up ISACs, and participate in international ISACs.
Policy and regulatory approaches
Around the world a number of evolving policy approaches to cyber resilience have already been adopted. These can be categorised on a scale ranging from highly prescriptive approaches with specific mandatory requirements, to less prescriptive performance-oriented framework-based approaches.
A more prescriptive approach entails a detailed set of implementation requirements, monitoring and reporting based on predefined standards, fixed into regulatory, licensing or prequalification requirements. A prime example of this approach are the cybersecurity regulations implemented in the United States through the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards. The advantage of such approaches is that they allow for more streamlined compliance monitoring. But, they can face pushback as industry see itself as too burdened by reporting requirements. Furthermore, there may be mismatches between the cycles of hardware, cybersecurity software and regulations. Regulatory updates that recognise technology changes and keep pace with evolving cyber risks are necessary.
Setting effective cyber resilience regulation is a delicate balancing act between enforcement and innovation
Spectrum of cyber resilience approachesOpen
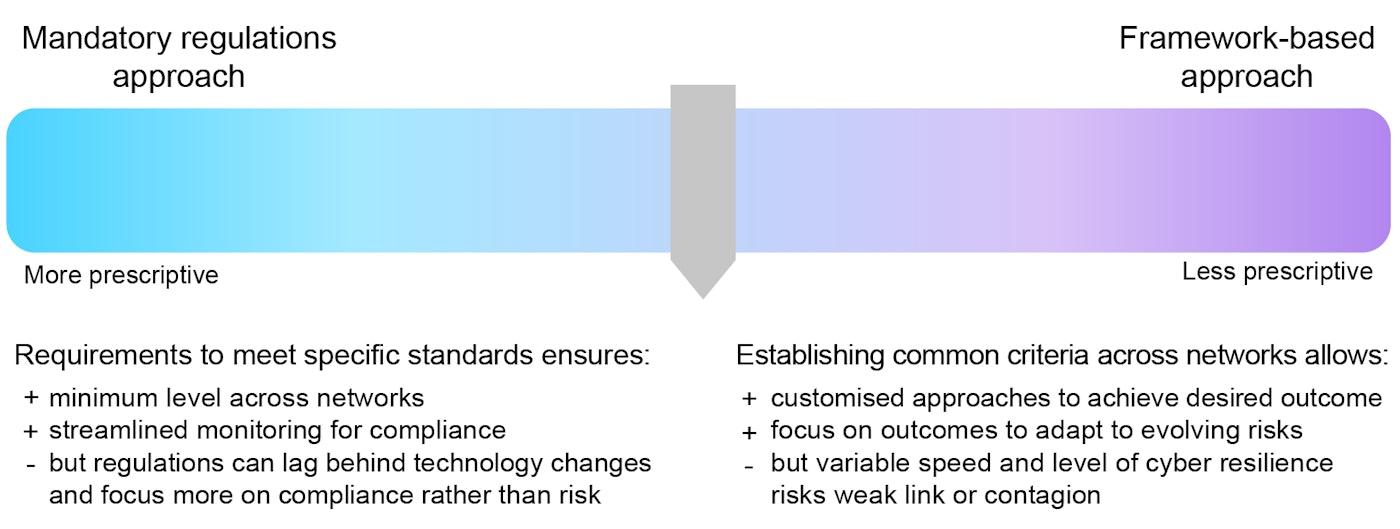
Less prescriptive, principle-based, performance-based or framework-based approaches are those that broadly indicate the structure of actors and safeguards that are to be put in place to secure the electricity network. Principle-based approaches aim to fulfil security principles while giving the operator some freedom when implementing the measures. Performance-based approaches, by contrast, are based on a number of metrics to assess the progress or the quality of implementation. Regulators can define specific target metrics, such as achievement of specific standards or time required to address a service disruption, leaving it to the operator to decide on the specific measures that will cost-effectively satisfy these metrics (NARUC, 2020).
An example of a framework-based approach is one adopted recently by the European Commission through the NIS Directive and follow-up legislation on the security of network and information systems. This particularly allows for different approaches and implementation speeds across jurisdictions, which has raised questions around how to establish a coherent and robust transnational approach to cybersecurity with tangible and effective impact. Moreover, as the NIS Directive is a cross-sector framework, it requires further measures to be implemented effectively in each sector. In the coming years, updates to grid codes are expected to bring more clarity as to concrete actions that can be implemented at the transmission and distribution level.
When the approach remains too conceptual and policy strategies have limited actual impact in mitigating risk exposure, the system is de facto depending on the voluntary initiatives of all electricity organisations active in the sector. A lot can already be achieved this way, and many countries and individual organisations have made enormous progress over the past decade. Policy intervention will be essential to ensure appropriate minimum security requirement levels are set for all actors, to overcome conflicts between operators and manufacturers, to nurture information sharing and to achieve international collaboration. Policies should not necessarily aim to bring every organisation to the same security level, nor to bring every organisation to the level of the most advanced one. However, weak spots need to be avoided in a system that is digitally, electrically and supply chain interconnected.
Prescriptive requirements evidently give the benefit of being very clear on who needs to do what. However, the scope of application set by an authority may simply follow from its own powers and may not necessarily be optimal. The case of NERC CIP in the United States provides an interesting example. While being clear on what applies to all bulk electricity system utilities, it does not cover smaller entities simply because they do not fall under NERC’s jurisdiction rather than being a rational choice. When devising policies to ensure cyber resilience in the power system, policy makers should ensure they instigate ecosystem-wide resilience, covering all actors interacting with the power system and their interlinkages rather than only network or system operators.
In addition to the choice of regulatory instrument for cyber resilience, there is the question of implementation. For more prescriptive approaches, a compliance-based strategy or checklist can be helpful in linking specific measures with known security risks. However, such approaches run the risk of becoming too focused on ticking boxes to meet the requirements, as well as facing the issue of a lag between technological change and the pace of regulatory change. Alternatively, prioritisation criteria can be applied as a sort of iterative risk assessment, identifying the logical next steps to make the system more secure. Such implementation may lend itself to more dynamic cyber resilience policies, but, as with performance-based regulations, may lack a clear direction or baseline for threat prevention, complicating evaluations of effectiveness or cost recognition by regulators.
There are inherent differences in the implementation of these general approaches, stemming partly from institutional contexts, for example differences in regulatory jurisdictions. This makes direct comparison difficult. While being the examples most often referred to, the United States and the European Union are certainly not the only jurisdictions developing policy frameworks for cybersecurity. Countries around the world, such as Australia, Brazil and Japan, show that it is possible to enact mixed approaches, borrowing on the strengths of both general approaches, but tailoring implementation closer to the realities of very diverse power systems.
Despite these differences in implementation, however, there is a degree of scope for establishing common approaches to cyber resilience. This is particularly important both because of the global nature of vulnerability to cyberattacks, and because many original equipment manufacturers supply globally, so once a vulnerability is identified in standard equipment it could be exploited in other power systems. For policy makers, this implies co‑ordinating with and establishing guidelines for equipment manufacturers.
While policies can enforce a compliance check for the implementation of measures, a true outcome-based approach does not exist specifically for cybersecurity, in contrast to conventional electricity quality of service regulations (for grid development, regulated tariff setting and general SAIDI or SAIFI##anchor2## targets). It remains questionable whether an outcome-based approach can be fully relied upon as a reasonable strategy for the resilience of critical infrastructure. The situation differs from that in grid development, where an investment can be motivated by system modelling analysis showing reduced operational costs or higher reliability, and where the actual impact on grid losses or interruption durations can be measured. A cyber resilience investment can hardly ever be weighed against a monetisable benefit or proven to be effective in retrospect by demonstrating prevented attacks. It is exactly because simply setting targets is not a realistic option that cybersecurity policies for the electricity sector are a complex issue for policy makers.
Implementation strategies should be tailored to national contexts while considering the global nature of risks
As electric vehicles, other behind-the-meter distributed energy resources, and connected devices become more prevalent, the potential for cyberattacks to cause significant disruption to electricity systems could grow. A recent study demonstrated that a targeted attack on personal electric vehicles and fast-charging stations using publicly available data could cause significant disruptions to local power supply. Another study demonstrated how high-wattage devices connected to the Internet of Things, such as air conditioners and heaters, could be used to launch large-scale co‑ordinated attacks on the power grid, resulting in local power outages and, in the worst cases, large-scale blackouts.
Research is underway in the United States to better understand the potential vulnerabilities of distributed energy resources, and to develop early warning systems and response algorithms to protect power supply. These efforts are particularly important following the enactment of the latest Rule 21 guidelines in California, which require all new solar and storage installations to use smart inverters with remote connectivity, a regulatory trend that is taking place in many power systems around the world.
Protection systems in end-consumer devices are often beyond the typical scope of energy ministries or energy regulators. Their regulation may lie with other government bodies such as consumer protection authorities, public safety and civil protection bodies, energy efficiency departments and even special agencies for IT security as is the case in Germany and France. In this sense, it is important for energy policy makers to engage across various government levels as well as with manufacturer associations and standards bodies to understand the potential risks to the system and how best to address them efficiently and effectively.
In addition, it is important to foster supply chain robustness to ensure that manufacturers have access to reliable, secure components, and that utilities, system operators and grid users have the means to track the security-readiness of the assets and systems they deploy. This applies equally to electricity grids, consumer-facing technologies, and industrial and commercial processes. As companies become increasingly interdependent for industrial and service processes, it is important to build supply chain resilience. Policy makers should ensure that there are platforms for industries and businesses to validate, communicate and improve on any potential cyber-related vulnerabilities in the supply chain. A further important consideration for policy makers is whether this is steered via transparency and trust, or if this is enforced by certification, incentives and penalties.
It is essential to ensure resilience at the grid edge and across the entire electricity system value chain
The electricity system has a unique set of operational conditions and requirements, vulnerabilities and solutions compared to other sectors. Enhancing the cyber resilience of electricity systems warrants tailored policies and strategies.
Energy policy makers have a critical role to play in enhancing cyber resilience across the electricity system, beginning with raising awareness and working with stakeholders to continuously identify, manage and communicate emerging vulnerabilities and risks. Policy makers are also well placed to play a central role in facilitating partnerships and sector-wide collaboration, information exchange programmes and research initiatives across the electricity sector and beyond.
No comments:
Post a Comment