James E. Cartwright and Jags Kandasamy
Executive summary
In March 2022, the US Department of Defense (DOD) released the Joint All-Domain Command and Control (JADC2) strategy, which describes the urgent need for an “enterprise-wide, holistic approach” to integrate command-and-control (C2) capabilities and empower joint-force commanders across all domains, theaters, and threats. This paper employs the JADC2 decision-cycle vision of “sense” (integrate information across domains), “make sense” (leverage intelligence to understand the environment), and “act” (decide and disseminate based on intelligence) through the lens of data, artificial intelligence (AI), and the edge continuum. It then presents a four-layer edge computing architecture for the DOD.
Sense: The DOD has deployed sensors at every vantage point in recent years, and a reflexive instinct has emerged in DOD to address operational problems by deploying more sensors for information gathering. As more sensors are added to the picture, even more data are being generated—for example, aircraft sensors and onboard equipment gather up to a terabyte of data during a flight. Yet, at the same time, more data bottlenecks are being created as communication networks fail to keep up with expanding data and sensor locations, a situation akin to freeways with the addition of more automobiles.
Make sense: Data without proper context and analysis are insufficient for actionable insights. Better understanding and analysis of the data provides information for decision-makers. This “make sense” paradigm becomes increasingly complex as the volume, velocity, and variety—the “three Vs”—of data coming from the sensors continue to grow. The DOD faces challenges in efficiently processing and analyzing the vast amounts of data generated by its operations in remote and hostile environments. AI and machine-learning (ML) algorithms have proven to be the optimal solution to make sense of the “three Vs” of the data conundrum. The emergence of AI at the edge (processing on or near devices where the data are created) has brought a significant opportunity for the DOD to filter the signal from the noise and enable real-time decision-making.
Act: Sensing and computing are distributed throughout the theater, from ground and aerial to geospatial sensors. Visualizing the connectivity of these assets enables the idea of the edge continuum. The edge continuum conceptualizes the distribution of resources and software assets between centralized computing clusters and deployed nodes and sensors in the theater as a path connecting the sensors to the command. Positioning key services and analytics along this edge continuum provides significant decision advantage by analyzing the data at the appropriate level and supporting the decision-makers at the unit, formation, and command levels, while relieving the bandwidth bottleneck.
AI/ML algorithms are viable services to be deployed along this edge continuum.
This proposed computing architecture for the DOD with AI at the edge is designed to address the challenges of efficiently executing the “sense,” “make sense,” and “act” cycle on the vast amounts of data generated by DOD operations in denied, disrupted, intermittent, and limited-bandwidth (DDIL) network environments. The architecture comprises four edge layers: Tactical, Operational, Command, and Strategic Edge. The architecture assumes that all layers, except the strategic layer, operate in constrained and denied environments, and that all layers are subject to denial-of-service (DoS) and deception attacks. The key principle of this architecture is to utilize the distributed computing power and to execute this cycle as close to the edge as possible, while preserving the ability to pass harder problems securely and confidently up the continuum as necessary.
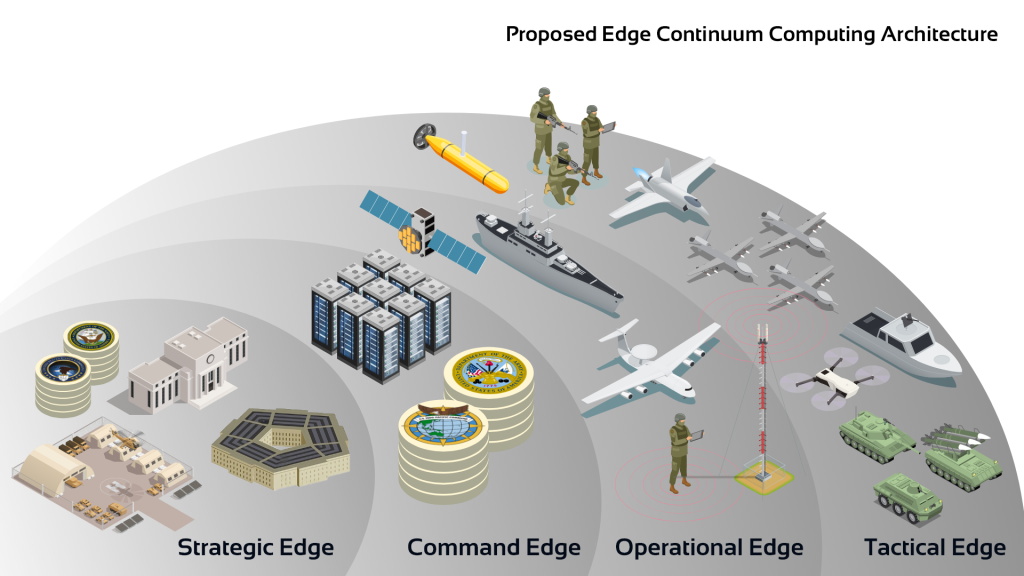
Tactical Edge: The Tactical Edge layer consists of various sensors converting analog to digital. These sensors mostly function as part of a platform (e.g., unmanned aerial systems, unmanned underwater vehicles, and tactical assault kits (TAKs) are part of the “sense” ecosystem). This layer operates in DDIL mode. The devices on this layer are predominantly low in size, weight, and power (SWaP). They possess limited storage memory onboard, and should have the ability to throttle data sent over communications based on connectivity. Any anomalies identified in this layer will be communicated to the operator and the next layer with expedience. This layer needs to be able to run AI models that are accurate and do not use a lot of memory, while also processing a lot of data quickly. In this layer, the models will have the ability to analyze known and frequently encountered signals, with the ability to filter and pass the unknowns and other criteria as defined by the operational parameters to the Operational Edge layer. This layer is capable of machine-to-machine (M2M) and machine-to-human (M2H) communications. The M2H communication will primarily be visual representations embedded in consoles and visualizations available in this layer. The sensor-to-shooter loop is the shortest in this layer and can enable autonomous (M2M) or human-enabled (M2H) fire control.
Operational Edge: The Operational Edge layer acts as a bridge between the Tactical and Command Edge layers. It receives filtered data from devices mostly in the same domain and, based on operational requirement, can ingest data from other domains, apply pre-processing algorithms, and transmit the relevant data to the Command layer. This tier forms the first layer for sensor fusion. This layer also has SWaP requirements with better access to power, and still operates on tactical communications-based connectivity. The models in this layer are analyzing the complex high velocity of Tactical Edge delivered data, providing feedback, and augmented situational awareness in a given tactical situation. This layer should have the ability to pass its raw data (already filtered at Tactical Edge) or transmit only the awareness it garners from the models at this layer. This layer is capable of both M2M and M2H communications.
Command Edge: The Command Edge is defined as the last layer of tactical communications. This layer collects processed data from multiple Operational Edge devices in a given scenario. The models in this layer are processing a high velocity and variety of data from different sensors, processed through Operational Edge devices. The Command Edge may operate in a stationary or mobile capacity for better survivability. The optionality allows the computing capabilities to be SWaP compatible at a different scale. This layer should provide information mainly for the human operators to make decisions (M2H). The layer should be capable of adding context to the data and transferring them for new training runs and for storage.
Strategic/Enterprise Edge: The Strategic or Enterprise Edge is the final layer of the architecture and is responsible for receiving and analyzing the data processed by the Command Edge layer. This layer consists of the DOD’s central data centers, national command and control, and continuity-of-government sites, and is hardwired to the rest of the network. The Strategic or Enterprise Edge layer provides the necessary infrastructure for data storage, analysis, and decision-making. Models here should have the ability to run on real-time as well as historical data to identify strategic needs for current and future needs. This layer consists of the AI/ML model factory, with the services solely responsible for training, optimizing, securing, and provisioning the AI/ML models. The services’ personnel in each combatant command at the respective layers are tasked exclusively with updating the model based on operational intelligence and data identified at the Tactical Edge.
Conclusion
This architecture is designed to enable real-time data analysis and decision-making in denied and degraded environments. This architecture ensures reliable, secure and disconnected decision-making between the various edge layers, and can be applied to individual domains and joint domains in data-centric warfare. As stated in the JADC2 strategy, maintaining information and decision advantage is key to command-and-control capabilities.
No comments:
Post a Comment