DANIEL PEREIRA
Google’s Cybersecurity Action Team was launched in early October of this year, as part of the company’s $10 billion pledge to strengthen cybersecurity, all of which grew out of the launch in August, by CISA Director Jen Easterly, of the CISA JCDC (Joint Cyber Defense Collaborative). Google is a partner company with CISA in the JCDC.
The Cybersecurity Action Team’s efforts begin with Google Cloud. They recently released their first publicly available intelligence offering – Threat Horizons, Cloud Threat Intelligence, November 2021, Issue 1 – a monthly report based on “threat intelligence observations from the Threat Analysis Group (TAG), Google Cloud Security and Trust Center, Google Cloud Threat Intelligence for Chronicle, Trust and Safety, and other internal teams.” The report provides:
- Actionable intelligence that enables organizations to ensure their cloud environments are best protected against ever-evolving threats; and
- Threat horizon scanning, trend tracking, and Early Warning announcements about emerging threats requiring immediate action.
At the same time as the launch of the Cybersecurity Action Team initiative by Google, the company announced that CrowdStrike will provide endpoint protection and Palo Alto Networks will provide network protection for Google Cloud customers. The entire cybersecurity initiative is also aligned with the NIST Cybersecurity Framework.
From the Inaugural Threat Horizons Report
Due to the sheer scale of Google and Google Cloud, the company’s findings and recommendations promise to be best-in-class and the entire report is worth a detailed review. The report begins by reinforcing that cybersecurity fundamentals still matter: “While cloud customers continue to face a variety of threats across applications and infrastructure, many successful attacks are due to poor hygiene and a lack of basic control implementation.”
Current threats observed include:
- Compromised Google Cloud Platform (GCP) instances used for cryptocurrency mining: Malicious actors were observed performing cryptocurrency mining within compromised Cloud instances. Of 50 recently compromised GCP instances, 86% of the compromised Cloud instances were used to perform cryptocurrency mining, a Cloud resource-intensive, for-profit activity. Additionally, 10% of compromised Cloud instances were used to conduct scans of other publicly available resources on the Internet to identify vulnerable systems, and 8% of instances were used to attack other targets. While data theft did not appear to be the objective of these compromises, it remains a risk associated with the cloud asset compromises as bad actors start performing multiple forms of abuse.
- North Korean actors impersonate employment recruiters: TAG observed a North Korean government-backed attacker group that has previously targeted security researchers posing as Samsung recruiters and sending fake job opportunities to employees at multiple South Korean information security companies that sell anti-malware solutions. The emails included a PDF allegedly claiming to be of a job description for a role at Samsung; however, the PDFs were malformed and did not open in a standard PDF reader. When targets replied that they could not open the job description, attackers responded with a malicious link to malware purporting to be a “Secure PDF Reader” stored in Google Drive which has now been blocked.
- Fraudsters employ new Threat, Tactics, and Procedures (TTPs) to abuse Google Cloud resources: TAG observed a group of attackers abusing Google Cloud resources to generate traffic to YouTube for view count manipulation. Attackers have also used various approaches to gain free Cloud credits, including the use of free trial projects, abusing start-up credits with fake companies, and joining Google Developer Communities for free projects. Upon detection and enforcement by Google’s Cloud abuse team, the attackers quickly switched to Qwiklab projects and the Cloud abuse team pivoted to counter this offensive.
- Black Matter ransomware rises out of DarkSide: Based on research from Google Cloud Threat Intelligence for Chronicle, Black Matter is one of many ransomware families currently being used to extort money from victims by locking their files using encryption; however, the ransomware does not transfer files off-network as its ransom note claims. While the Black Matter group is a relatively new player in this space, evidence suggests it is the immediate offspring of DarkSide. Black Matter is capable of encrypting files on a victim’s hard drive and network shares in a relatively short period of time by distributing the workload across multiple threads.
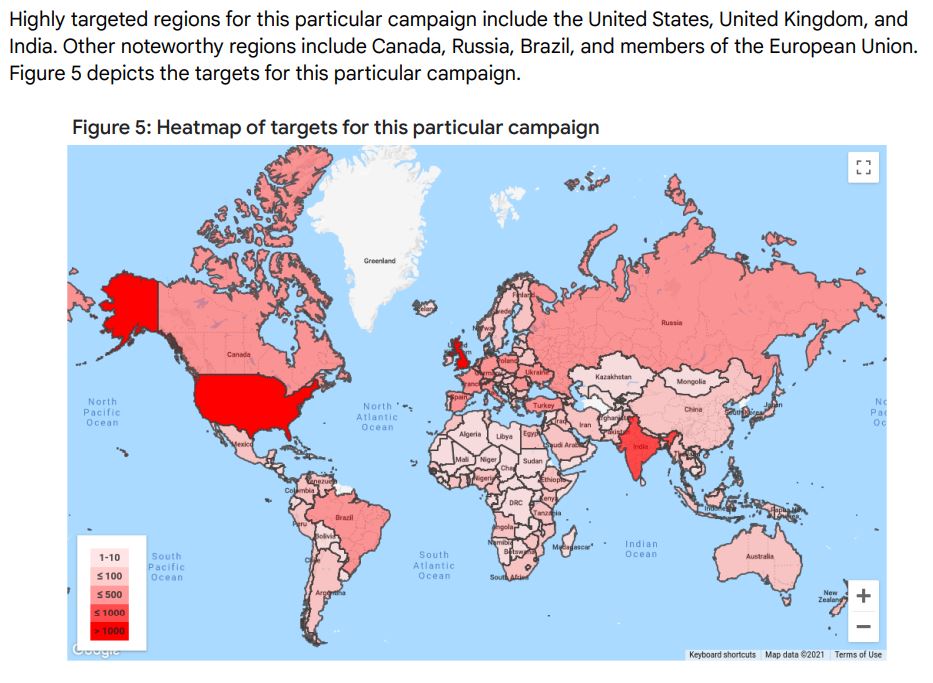
- Russia launches Gmail phishing campaign: Based on research from Google’s Threat Analysis Group (TAG), the Russian government-backed attackers APT28/Fancy Bear, which typically targeted Yahoo! and Microsoft users, was observed at the end of September sending a large-scale attack to approximately 12K+ Gmail accounts in a credential phishing campaign. The attackers were
using patterns similar to TAG’s government-backed attack alerts to lure users to change their credentials on the attacker’s phishing page. Google blocked these messages and no users were compromised.
No comments:
Post a Comment