Maj Gen PK Mallick, VSM (Retd)
The digital era has transformed the way we communicate. Using social media like Facebook and Instagram, and social applications such as WhatsApp and Telegram, one can be in contact with friends and family, share pictures, videos, messages, posts and share our experiences. Social media has become an effective way of influencing human society and behavior, and shaping public opinion. By sharing a post, tweeting an idea, contributing a discussion in a forum and sharing a sentimental picture, we can influence others and sometimes convince into with our opinion.
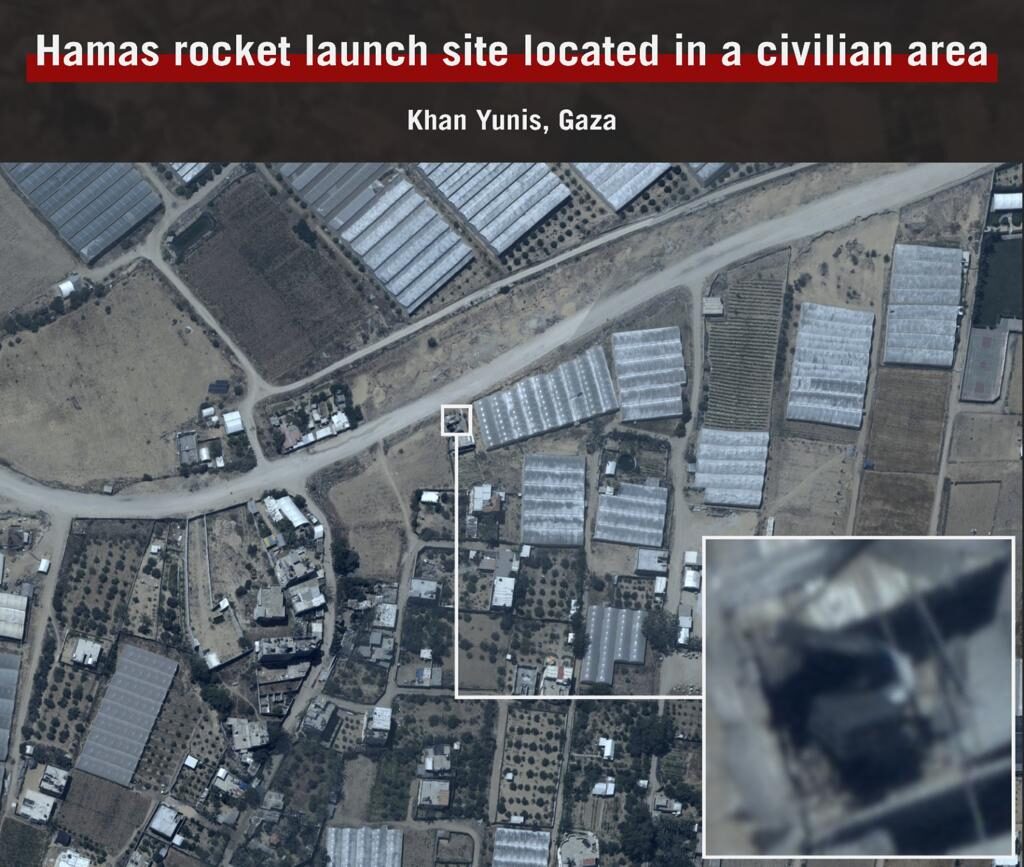
Use of cyber tools and methods to manipulate public opinion is called ‘Cyber Influence Operation’. In the present day, many countries use cyberspace, especially the social media, to accomplish Cyber Influence Operations as a part of Information Warfare. Most of these operations are done covertly. It is difficult to differentiate between legitimate or malicious influence operations. Continue Reading.....











/cloudfront-us-east-1.images.arcpublishing.com/mco/QODFGO5ZHNEJZCZQ72U2XV363M.jpg)