DANIEL PEREIRA

In the second half of April 2023, the UN predicts India will become the most populous country in the world, surpassing China. More than 40% of India’s residents are under the age of 25. People over the age of 65 only make up about 7%. India is also on track to become the world’s third-largest economy by 2027.
OODA Loop Sponsor
India is poised to overtake China as the world’s most populous nation, with almost 3 million more people than its neighbor by the middle of this year, data released on Wednesday by the United Nations showed.
India’s population by mid-year is estimated at 1.4286 billion, against 1.4257 billion for China – 2.9 million fewer – in the United Nations Population Fund’s (UNFPA) “State of World Population Report” for this year.
The United States is a distant third, with an estimated population of 340 million as of the end of June, the data showed in a report that reflects information available until February.









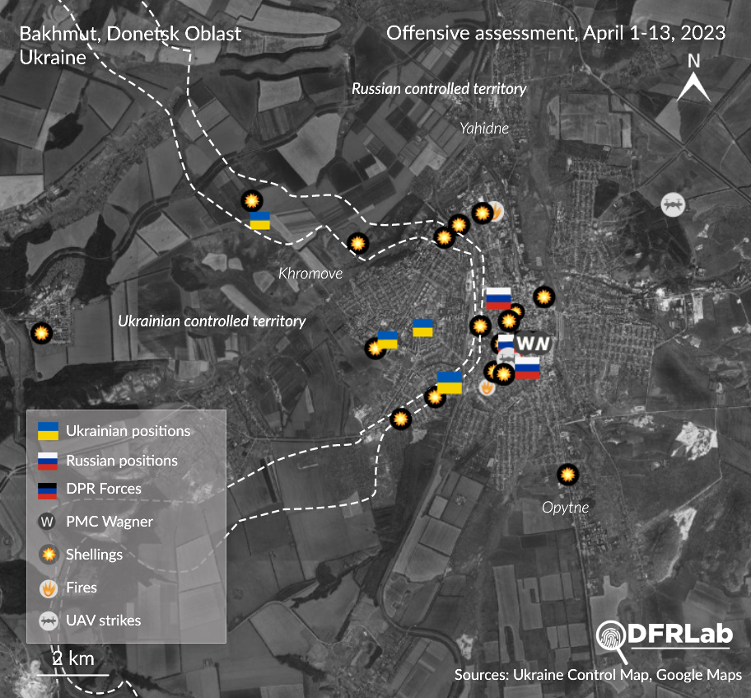 Documented locations of fighting April 1-13, 2023; data gathered from open-source resources. (Source: Ukraine Control Map, with annotations by the DFRLab)
Documented locations of fighting April 1-13, 2023; data gathered from open-source resources. (Source: Ukraine Control Map, with annotations by the DFRLab)









