Dr. Valentin Weber
2010 was a seminal year. Stuxnet, an American-Israeli cyber operation sabotaged Iranian uranium enrichment centrifuges. It became publicly known as the first cyber operation in history that destroyed physical objects. This operation had the clear goal of degrading Iran’s uranium enrichment capability, but in general there has been little research as to why hegemons launch destructive cyber operations. This brief argues that the main motivations are threefold: territorial conquest, threat prevention, and retaliatory actions.
KEY FINDINGS
Iran, North Korea, South Korea, Ukraine and Taiwan have been the main targets of destructive great power cyber operations.
For the US, future targets will possibly be limited to countries that aim to acquire nuclear weapons – Iran and North Korea.
Given ongoing border disputes, China and Russia will likely target neighboring countries with such destructive campaigns – for China those are Vietnam, the Philippines, and Japan, and for Russia they are Georgia, Moldova, and Japan.
To prevent destructive cyber operations, Germany and other EU states have been engaged in cyber capacity building and threat-intelligence sharing across continents. But Berlin needs to set priorities.
When it comes to combatting state-sponsored cyber campaigns, Germany should deepen ties with non-EU countries that have been or likely will be targets of damaging rather than merely disruptive operations, i.e., in Southeast Asia, East Asia, the Caucasus, and Southeast Europe.
The online version of this Policy Brief doesn't contain footnotes. To see the footnotes, please download the pdf version here.
When pundits and policy makers characterize the operations of great powers in cyberspace, they often label the United States as precise, responsible, and stealthy, China as loud, and Russia as reckless. This commonly held distinction between these actors has become less applicable as the great powers have increased such activities. In some recent operations, China has been very stealthy. It has tried to remain covert and maintain long-term access to the systems it has breached . Russia, too, was surgical in its operation targeting Texas-based SolarWinds, one of the most sophisticated cyber operations in US history, which spread undetected for months to the company’s clients, allowing Russian hackers to infiltrate major US corporations and government agencies.
But this policy brief is not about how great powers conduct cyber operations. Rather, it examines an aspect that has been less explored. It aims to provide a comparative analysis of why hegemons conduct destructive cyber campaigns and to provide recommendations as to what Germany and other European Union member states can do to mitigate them.
This brief defines destructive cyber operations as having the following effects:
Death or human injury
Considerable physical damage
Demolition or modification of information, making data useless if significant efforts are invested to make systems work again
But there are a few caveats. It does not examine state behavior aimed at non-state actors (e.g., the US targeting ransomware gangs or Islamist extremist groups), nor does it explore cyber operations solely consisting of distributed denial of service (DDoS) attacks, which overwhelm servers with internet traffic, or website defacements (e.g., Russian attacks on Estonia and Georgia, both in the late 2000s), as those are mostly disruptive but not destructive. This brief also does not examine cyber operations during large-scale hostilities where countries face each other in a major war (Russia attacking Ukraine in 2022). Here it is important to note that destructive cyberattacks, especially wipers (malware that destroys data), have been used frequently by Russia against Ukraine since its full-scale invasion in 2022.
A Short History of Destructive Cyber Campaigns
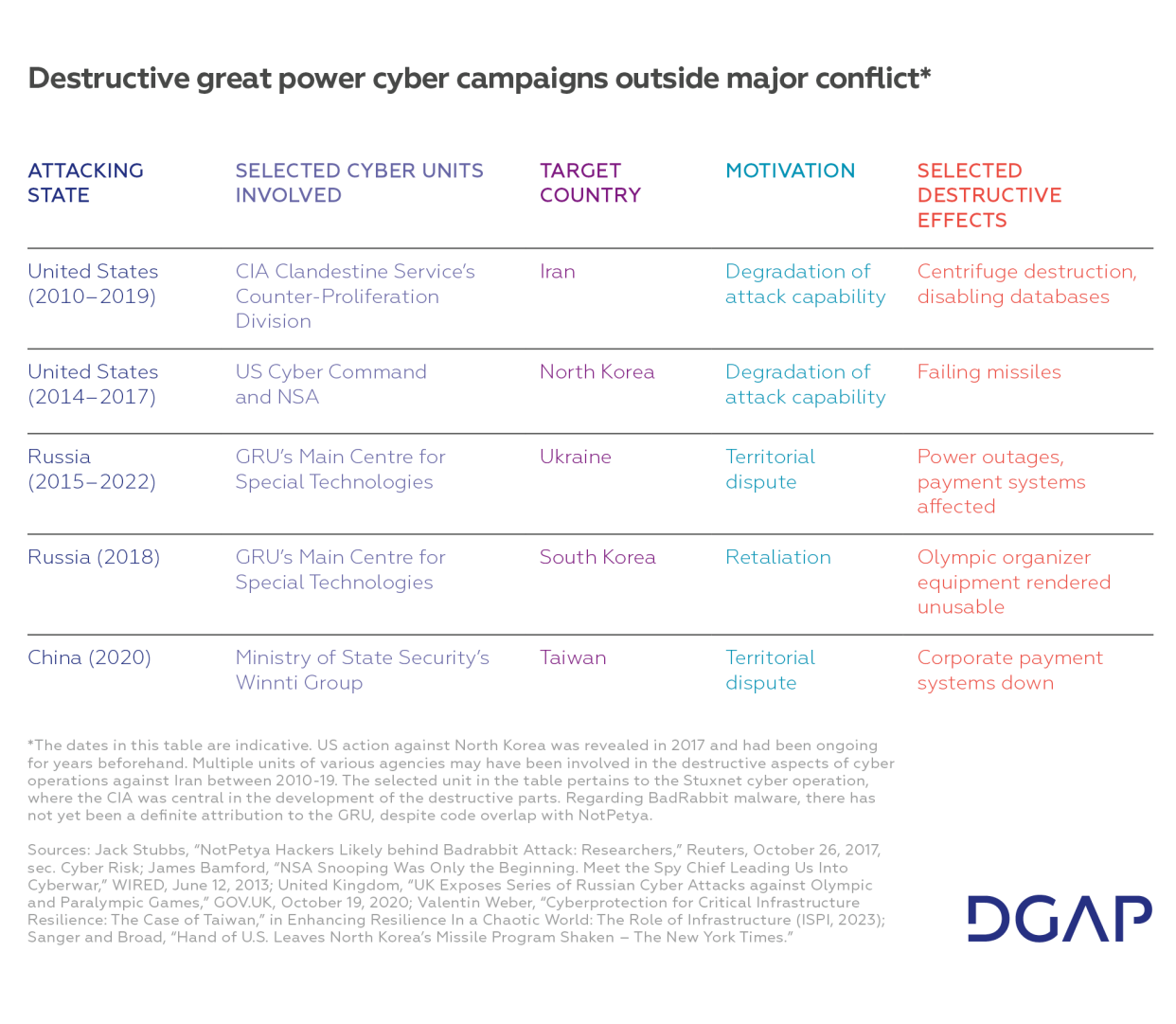
The sample size of destructive great power cyber operations targeting states outside of a major conflict is rather limited. Historically, there have been five series of destructive operations (i.e., cyber campaigns), which will be discussed in more detail below. These include the US targeting Iran’s nuclear sector and databases (2010-2019) and North Korea’s missile program (2014-2017), China targeting Taiwan’s oil and gas, telecommunications, and other critical sectors (2020), and Russia inserting malicious code into a host of Ukrainian critical infrastructure (2015-2022) and systems of the Olympic games organizers in South Korea (2018). Each of these campaigns consisted of multiple cyber operations. In this brief, they count as one series of destructive cyber behaviors – a destructive cyber campaign.
US-Iran (2010-2019)
The first cyber campaign examined relates to the US-Iranian dyad. In 2010, a destructive cyber operation known as Stuxnet hit nuclear enrichment facilities in Natanz, Iran. In addition, in 2019, the US disabled Iranian databases that Tehran had used to attack oil tankers in the Gulf.
US-North Korea (2014–2017)
Since the mid-2010s, most North Korean missiles have exploded mysteriously, long before reaching their target. The US was alleged to have interfered with Pyongyang’s missile program to delay and degrade its missile strike capabilities. This may have been achieved by subverting supply chains and tampering with nuclear command and control systems. According to a Reuters report, the US may have simultaneously targeted North Korean and Iranian nuclear programs. While the US had been successful in Iran already in 2010, the cyber campaign in North Korea took a few years to show effects, and was helped by its reinforcement in early 2014 under then-President Barack Obama.
Russia-Ukraine (2015-2022)
Even before Russia’s full-scale invasion of Ukraine in 2022, the target of its most destructive operations appears to have been Ukraine. In 2015 and 2016, the GRU (Russia’s military intelligence service) conducted operations against Ukraine’s power grid. In 2015, this resulted in six hours of power outages, affecting 225,000 customers. In 2016, another Russian cyber operation knocked out a Kyiv electricity substation for around an hour. Further destructive campaigns on state institutions affecting the Ministry of Finance and the State Treasury Service took place in 2016. During the next year, the malware NotPetya, attributed to the GRU, hit Ukraine and the wider world causing significant destruction and economic costs.
Russia-South Korea (2018)
In 2018, Russia targeted South Korea. Prior to the Pyeongchang Olympics in 2018, a cyber operation disabled the organizer’s ticketing system, Wi-Fi and TV screens around several Olympic facilities. A solid effort by the organizer’s security defenders averted the worst. But even if major havoc was avoided, the cyber activity was destructive in nature, since it contained data-wiping components and obstructed data recovery procedures. As Warren Mercer, threat researcher for Cisco Talos notes, “Wiping all available methods of recovery shows this attacker had no intention of leaving the machine useable. The purpose of this malware is to perform destruction of the host, leave the computer system offline, and wipe remote data.”
China-Taiwan (2020)
In May 2020, a wiper attack hit several critical infrastructure companies in Taiwan, including oil and gas importer Taiwan Chinese Petroleum (CPC), encrypting systems. In financially motivated attacks, a decryption key would have been offered in exchange for a ransom. The lack of a ransom component in this case makes a destructive intent plausible: “A closer look into the malware revealed this particular variant of ColdLock [malware] had removed all the payment information, contact email, and the RSA public key. This indicates that no information could be provided for decryption.” While the effect on the Taiwanese economy was to some extent disruptive (people couldn’t use CPC payment cards to buy gas), affected data on CPC systems was deleted and rendered unusable due to encryption. CPC had to reconstruct some of its infrastructure after the cyber operation. Taiwan’s Ministry of Justice attributed the activities to the Winnti Group, a threat cluster affiliated with the Chinese Ministry of State Security.
More operations could have been included in this analysis, but were excluded due to non-definitive attribution claims. Those would have been China causing power outages in India in 2021 and shutting down a port in Japan in 2023, as well as the US causing explosions of a Russian gas pipeline in 1982.
Commonalities of Past Destructive Cyber Campaigns
Motivation – The Strong Do What They Can
All five cyber campaigns by the US, China, and Russia examined in this policy brief were conducted on national security grounds.
Beijing and Moscow have for some time been advancing territorial claims in Taiwan and Ukraine, respectively. The primary reason for the Russian cyber campaigns conducted between 2015 and 2022 was that Russia did not recognize Ukraine’s territorial sovereignty and saw cyber operations as a way to punish Ukrainians for striving to liberate themselves from Russian influence. China’s main motivation for its campaign against Taiwan was to exert political deterrence. The wiper attacks occurred weeks before Taiwan’s inauguration of a president Beijing did not approve of, and may have been meant to signal to Taiwanese citizens that this would come with costs. Similar non-destructive hacktivist cyberattacks of Chinese origin, with the aim of inducing fear, surfaced during U.S. House Speaker Nancy Pelosi’s visit in 2022.
The reason for US destructive behavior is to degrade an adversary’s attack capabilities. Based on this goal, the US deployed destructive campaigns against North Korea and Iran to delay their acquisition and deployment of offensive weapons. The underlying motivation behind the US cyber campaigns is threat prevention, both nuclear (Stuxnet) and conventional (attack on Iranian databases). Although the US never officially confirmed its cyber campaigns, former senior US intelligence officials stated that Stuxnet was intended to help the US convince Iran to abandon its pursuit of a nuclear bomb. Similarly, the officials said the attacks against databases were meant to signal that “the United States has enormous capabilities which they [Iran] can never hope to match, and it would be best for all concerned if they simply stopped their offending actions.”
The third reason for destructive behavior is retaliation. A case in point is Russia’s sabotage of the Olympic games in South Korea. These came after Russian athletes were banned from competing under the Russian flag in the Olympics and receiving medals for their country, due to Russia’s systematic manipulation of doping regulations.
Power Dichotomy – The Weak Suffer What They Must
In addition to these commonalities, all cyber campaigns examined took place in a dichotomy. Power asymmetries were extensive. Great powers were able to conduct cyber operations as they felt secure and did not fear any major backlash. Russia, for instance, has not conducted major damaging operations against NATO countries, but it did target the Ukrainian power grid twice in the mid-2010s. The US felt at liberty to go after the nuclear missile programs of both Iran and North Korea, countries that can be situated at the medium and lower spectrum of national power. China, too, was not deterred in its cyber operations against Taiwan.
Leading a crippling campaign against another great power in the cyber domain has most likely not occurred yet, although Washington, Moscow and Beijing may have placed logic bombs in each other’s critical infrastructure – malicious code that only activates under certain conditions. The US seems to have taken this path, specifically by planting damaging malware in Russian infrastructure, in response to perceived Russian incursions into critical US systems.
The next section will examine the lessons of past destructive cyber operations for analyzing future damaging operations.
Locating the Next Big Destructive Cyber Campaign
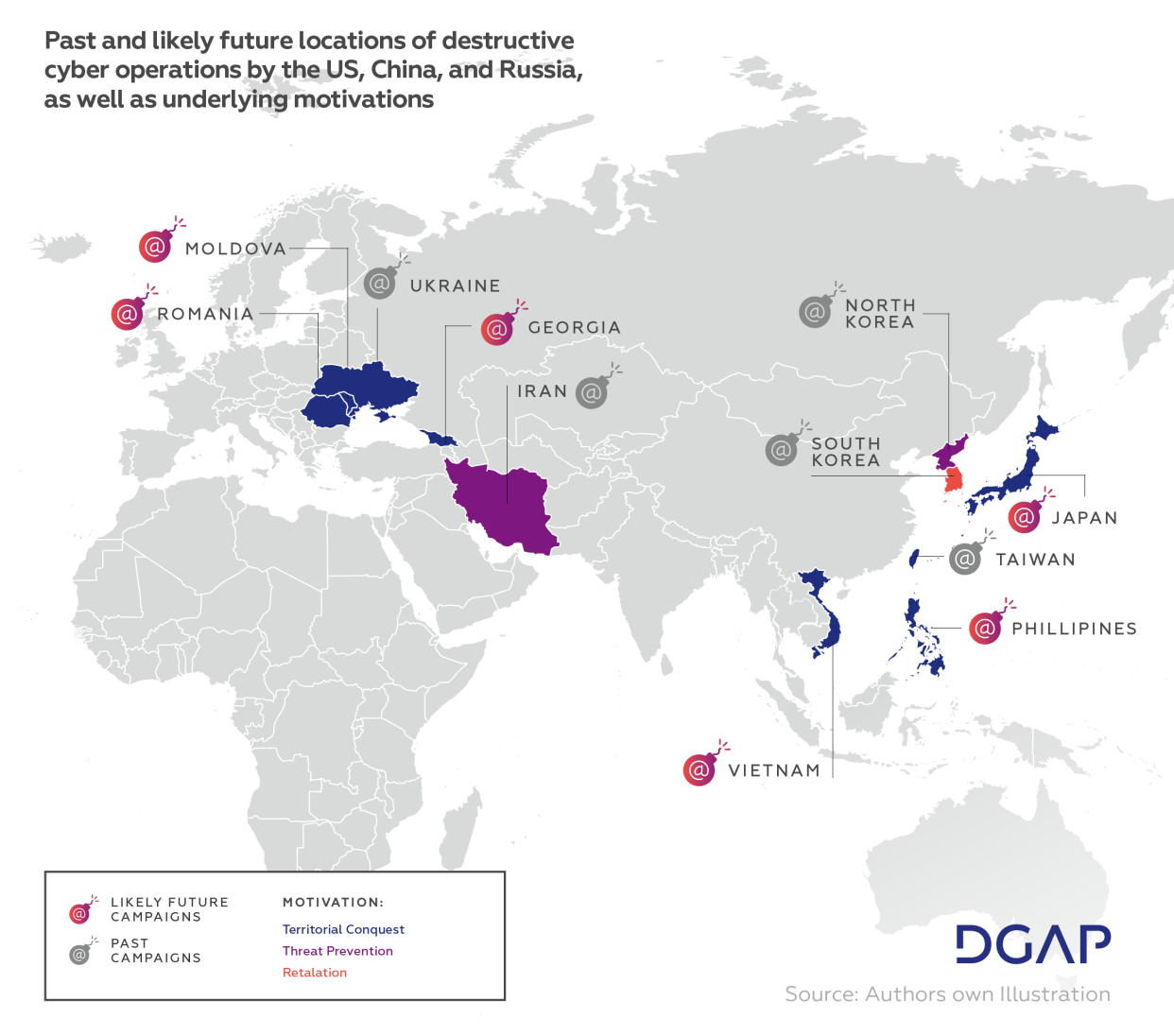
Beyond renewed destructive operations by the US against Iran and North Korea, China against Taiwan, or Russia against Ukraine, the following great power cyber flares are likely. The US has deployed its most devastating cyber capabilities against non-friendly countries that aim to become nuclear powers. As there are currently no other adversarial states going down this path, such operations against other countries are unlikely. China and Russia, however, will likely be driven by their motives of territorial conquest and retaliation to conduct destructive cyber operations against new targets.
Image
(South) East Asia
China has 17 ongoing territorial disputes. The most likely of these to escalate are those with perceived enemies, such as Vietnam, the Philippines, Japan, and South Korea. With India, too, China might use damaging cyber means, and there are reports that this has already occurred. Because the power dichotomy between India and China is relatively small (both countries have sizeable militaries), and because both are nuclear armed, China’s use of destructive cyber power is less likely than in the other border disputes listed above.
Russia is also involved in several border disputes that could lead to destructive behavior. The spat with Japan over the Kuril Islands (which Russia has been militarizing) has flared up again since Russia’s invasion of Ukraine. The Russian assault brought about a shift in thinking in Tokyo, which has increasingly distanced itself from Russia, including in negotiations over the islands.
Caucasus and Southeast Europe
On its southern border, Russia occupies Georgian territory of South Ossetia and Abkhazia. Moscow has also repeatedly led disruptive cyber campaigns against Georgia, e.g., in 2008 and 2019. Moldova, too, has territorial disputes with Russia over Transnistria and has been subjected to Russian cyberattacks. Moscow could extend these to become destructive, since the power dichotomy between Russia on the one hand and Georgia and Moldova on the other is large and because the latter two are not shielded by NATO.
In addition to this, Moscow could retaliate against perceived injustice, as with the cyber operations during the Olympics in South Korea. These activities with retaliatory motives are the most difficult to predict, as Russia is irritated by many international events and not all its retaliatory actions are destructive, but rather disruptive. In addition to this, the Kremlin does not always act upon its threats. What is more, all Olympic games in the coming five years will be held on NATO territory, making destructive Russian attacks in the Olympic context unlikely.
What to Do
What Should Be Done Against Destructive Cyber Campaigns?
Germany and other EU member countries that champion cyber capacity building at the United Nations ought to increase their capacity building efforts in Ukraine, Moldova, and Georgia. This could be done through existing EU or NATO initiatives or bilaterally to complement multilateral efforts. While Ukraine has done remarkably well in defending its assets in cyberspace, there is always room for more cooperation and (monetary) assistance for Kyiv to further shore up its cyber defenses. Georgia especially appears to have continuous difficulties with DDoS attacks, despite their low sophistication. Tbilisi’s preparedness for and resilience to destructive cyber operations is likely to be low. These three countries (Ukraine, Moldova, and Georgia) are the most likely to experience severe Russian cyber campaigns. Further, capacity building should focus on Southeast Asia (Vietnam and the Philippines), where countries will likely experience Chinese destructive cyber activities. With Japan and South Korea, European partners should increase threat-intelligence sharing regarding Russian and Chinese threat actors to more swiftly mitigate potential vulnerabilities.
Second, NATO and EU countries should not change their policies of supporting Ukraine based on Russian threats. Russia has threatened to target arms and humanitarian shipments to Ukraine and by extension, also the countries supporting them. But until now, only cyber disruptions have occurred, not destruction The military strength of the EU/NATO vis-à-vis Russia is likely to serve as a powerful deterrent against destructive activities.
Third, the energy sector, and in particular, the electrical grid, should receive a more prominent role in international norm setting, as destructive cyber operations have targeted it the most. While the energy sector, like all critical infrastructure, is already protected by international law, countries should work multilaterally and bilaterally to reduce vulnerabilities in this sector. Regarding the electrical grid in particular, Germany ought to promote an international norm requiring that states refrain from conducting any cyber operations against the electrical grid in peacetime, including cyber espionage operations or the planting of logic bombs. The electrical grid deserves this special protection, as all other critical infrastructure relies on it.
No comments:
Post a Comment