Joseph Downing and Richard Dron

Critical Security Studies has acknowledged how everyday practices, such as CCTV operation, have embedded security concerns increasingly in everyday life (Huysmans 2011). Social media has dramatically escalated this process, “democratising” the ability of the individual to “speak” security and become producers of the speech acts, so central to the elite centric work of the Copenhagen School (Buzan et al. 1997) and the generations of security scholars that they inspired. As we are ever more immersed in the social media age, it is ever more vital that critical security studies, and international relations more broadly, thoroughly and critically engages with theoretical and empirical challenges presented by the digital communications revolution.
This is especially important for the discursive turn in security studies since, while individuals still have little material control of the security environment, they increasingly have the ability to shape the security debate. The constructivist turn in security studies began with the elite centric Copenhagen School (Buzan et al. 1997). Here, elites competed to structure security debates and threats and move issues between emergency and non-emergency politics. However, the hierarchical nature of this work leaves little room for understanding how “non-elites” discuss, redefine and contest security narratives. Thus, the Copenhagen school cannot offer a conceptualisation of how constructivist notions of security apply outside of the context of the elite.
A contemporary response has been vernacular security studies (Bubandt 2005; Jarvis 2019) which consider the voice of non-elite actors within security debates. This brings “lay” actors into the equation, offering insights into how security is constructed through local idioms. This, however, does not allow for a conceptualisation of the tension between the democratised landscape of social media which is also replete with hierarchies of influence. Thus, while social media provides important insight into vernacular security speak, it is not completely “flat” and some vernacular speak becomes “more equal” than others. Social media presents constructivist security scholars with a theatre of study sitting somewhere between the “flat” plane of vernacular and hierarchical notions of the Copenhagen school in that, whilst anyone theoretically can “speak” security on social media, only a few will become influential doing so. This article contributes to understandings of constructivist security through analysing social media outputs to understand who is influential in the security debate and how. Working at the intersection of “flat” vernacular and “hierarchical” Copenhagen School understandings of security, it identifies mechanisms of security influencers’ rise to prominence, speaking to the reality of the social media landscape that renders security speak neither radically flat nor rigidly hierarchical. This enables incorporation of notions of non-elite actors speaking security in ways that enable novel theoretical insights for both schools of critical security.
Influencers are primarily considered within marketing as representing independent third-party endorsers shaping audience attitudes through shared online content. Although there have been significant academic definition influencers (Bakshy et al. 2011) and quantifying influence (Anger and Kittl 2011) there is little consideration of typologies. This presents important areas in which we can consider how individuals become influential within key security debates. We used an innovative mix of discourse and social network analysis to understand the contours of the social media landscape and how influencers emerged in the 48 hours after the Manchester bombing on Twitter.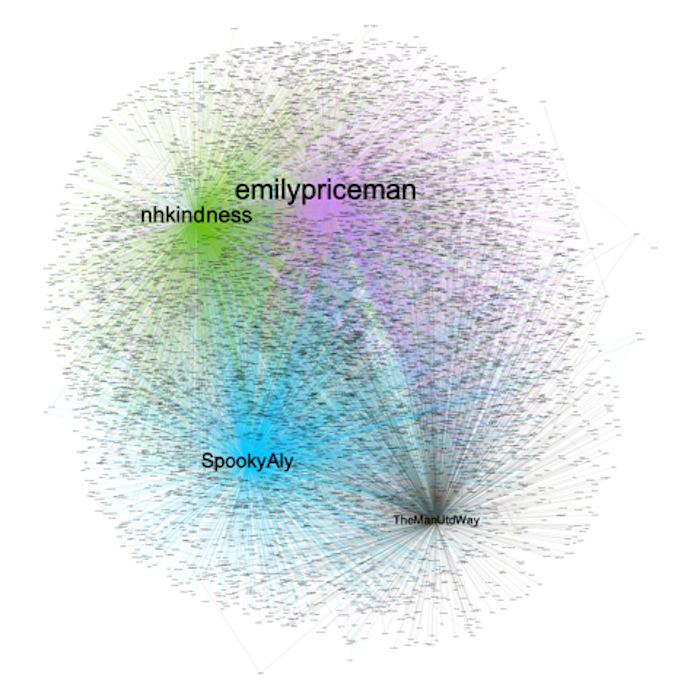

Figure 1: Visualisation of the 4 most influential sub-network structures.
Social network analysis Social network analysis of Twitter data offers insights into “influence” because it identifies who is central to security speak in any given context. The SNA also demonstrates how influencers’ conversations have little interaction with others: conversations analysed remain discrete and contestation/agreement occur within specific clusters without spreading, even though they emerge thematically and are empirically similar in message. However, it should not be mistakenly assumed that “influence” is a synonym of “agreement” as a significant amount of engagement that drives an individual or hashtag (#) into prominence on social media comes in the form of contestation or value-neutral engagements. Our paper established this in the security context as we applied both discourse and sentiment analyses to all tweets within the four influential networks. This enabled us to understand not only how tweets were engaged with, but importantly on what terms they were engaged with a what drove this particular security debate.
Our results identified a typology of four kinds of security influencers within the discussion of Muslims in the aftermath of the Manchester bombings.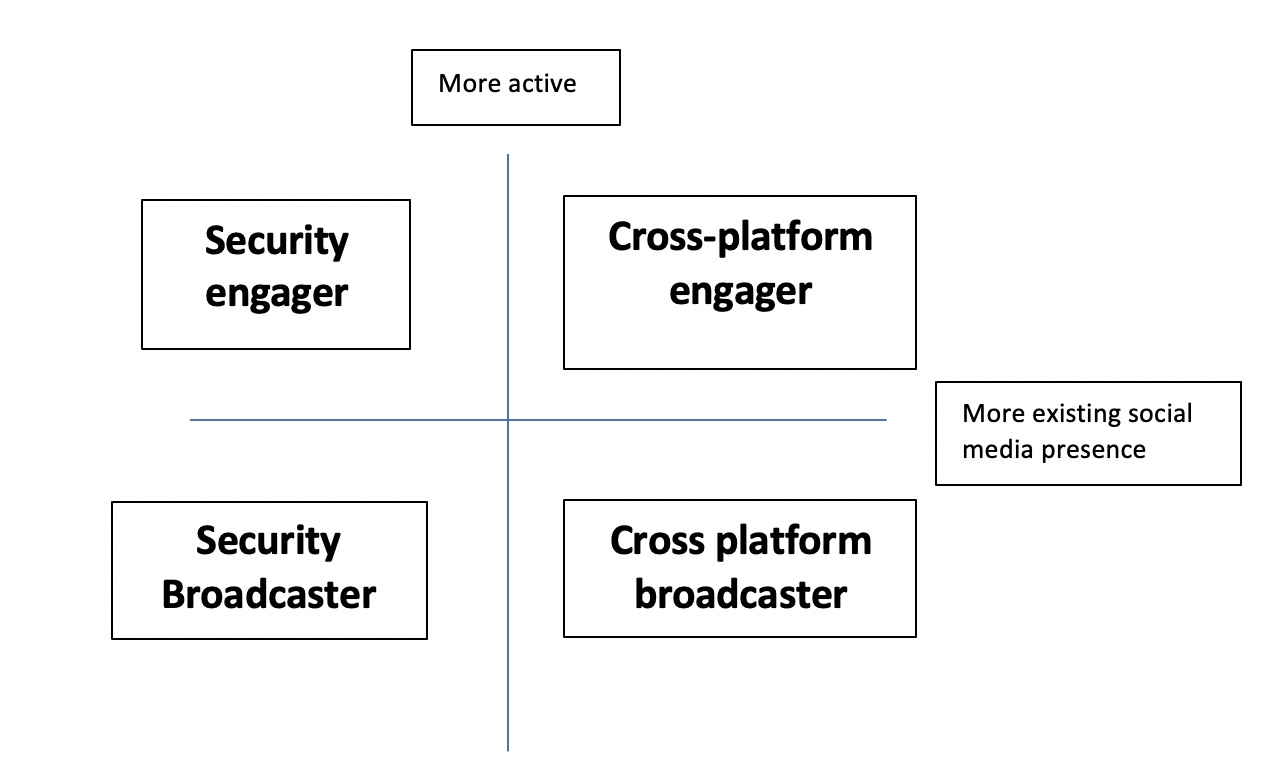

Figure 2: Typology of security influencers
These four kinds of influencers demonstrate the undulations and complexities of the hierarchies of security speak on social media. The first type of influencer the “security broadcaster”. This type of security influencer simply broadcasts a message that becomes influential without further engagement from the influencer. This is interesting because critical security studies conceptualise elite generated security discourse in this way. The Copenhagen school sees the elite as in a position of power projecting their security narratives to the audience (Huysmans 2011). However, this individual does not have to have previous forms of social media influence. As such they are not even amongst the ranks of the social media “elite” but rather rise, without any particular reason other than the salience of their message at that moment, to prominence and then fall back to obscurity again. This demonstrates the unpredictability of the social media landscape and presents challenges to scholars who want to build a theory on. Nevertheless, the other type of “passive” broadcaster identified did have some “elite” credentials on social media – but from a total security unrelated domain as a super fan of a particular pop star. Thus, the cross-platform broadcaster has existing influencer capital in a non-security domain that they pivot to discussing security. Both types of broadcaster demonstrate some interesting aspects of the increased immersion in security debates experienced by non-elites and how they are now confident to express opinions on security issues.
Other influencers are way more active and follow up their initial messages with further engagements with other social media users, especially those who contest their initial messages and do not agree with them. The security engagers not acting simply like traditional security elites conceptualised by the Copenhagen school (Buzan et al. 1997) who “broadcast” their message to the audience, but rather they engage further with responses to their messages on social media. Again, nonetheless, we identify the unpredictability of this process as one of the security broadcasters has no previous social media capital nor security credentials and rises to prominence to only fall back into obscurity. However, the cross-platform engager is very different in that they pivot existing social media influence from a non-security field into the security discussion. In this case a Manchester United fan account with significant existing influence in the domain of sports pivots to engage in the security debate. This demonstrates the increased enmeshment of security with everyday social and cultural themes, with football team-based forms of identity being established as important in expressions of discursive resistance to the so-called Islamic State (Downing 2020).
A broader theme within security speaks also emerges that cuts across both the active security engagers and the passive security broadcasters. This is the difference in the balance of contestation and agreement that is present depending on how the broadcasters depict Muslims/Islam within the Manchester bombings context. Increased contestation was identified when influencers structured their security speak on the defence of Islam as an abstract global religion. Such a process resulted in other social media users being more likely to disagree with their messages and respond with tropes of Islam being inherently prone to produce violence and extremism. However, when the defence was structured around a defence of Muslims as a social group, users were more likely to agree and differentiate Muslims as a social group from terrorism and violent extremism. This is important as social media users here directly connect Muslims to the local context of Manchester. Thus, this evidences discursive processes of the “banalisation” (Downing 2019) of Muslims as a social group through their connection to everyday social roles instead of the exceptional episodes of acts of religious and political violence.
Social media is clearly under conceptualised in critical security studies at almost every turn. The Copenhagen school, some two decades old, looks increasingly limited when it comes to understanding security speak on social media, with the few exceptions of “security elites” such as President Trump, who used social media to such effect to produce and disseminate speech acts. However, the Copenhagen school offers the opportunity to conceptualise hierarchies of importance when we consider competing security narratives in any given situation that still exist on social media due to discrepancies of influence between social media users. This challenges dominant conceptions that the communications revolution brought about by social media is universally democratising. We can see within Manchester that there is no formula for deciding who on social media rises to prominence as a security influencer in any given context, and security influence in this case is ephemeral and short-lived.
The more recent vernacular turn in CSS is under-utilised when considering the social media landscape. Vernacular voices on security come from a number of unexpected areas – such as football or music fans – and thus we need to consider how the increasingly enmeshment of security with the everyday twists and shifts security narratives in unexpected ways. However, a dominant distinction remains where between narratives about Muslims as relatable human beings in a specific social context, and the more abstract discussions of Islam as a global religion, where social media users are clearly literature in dominant debates about relationships between terrorism and religion. Within this the “local” “banal” Muslims are easily distinguished from those who commit acts of mass violence, whereas great suspicion is directed at Islam as a religion.
No comments:
Post a Comment