November 24, 2017: Pakistan has accepted an American offer to cooperate and quickly deal with any cross border activity in eastern Afghanistan that results in Islamic terror attacks in Pakistan. Earlier in the week the U.S. military commander in the region offered a solution and told Pakistan that American forces would be made available to deal with any Islamic terrorist groups Pakistan feels are hiding in eastern Afghanistan and have, increasingly, been attacked with Pakistani artillery fire (rockets, mortars and howitzers firing across the border). Afghans feel the Pakistanis will invent an excuse to reject or sabotage the American offer because over the years Afghans in borders areas regularly hit by the Pakistani rockets and shells have told Afghan and American Special Forces troops that the Pakistanis often fire when there is no one out there or after anti-Pakistan Islamic terrorists have passed through the area days or weeks earlier. Sparely populated regions like Kunar province have plenty of hills and forests to hide in, and few roads to quickly bring in a lot of Afghan soldiers or police. The American offer is backed by the fact that the U.S. has helicopters, UAVs and other aircraft available to quickly act on Pakistani complaints. This could get interesting.
26 November 2017
Rohingya Crisis: Will China’s Mediation Succeed?
By: Sudha Ramachandran
During his visits to Dhaka, Bangladesh and Naypyitaw, Myanmar on November 18 and 19, China’s Foreign Minister Wang Yi put forward a three-phase plan to resolve the Rohingya crisis. First, Wang called for a ceasefire in Myanmar’s devastated Rakhine state, which is at the center of the crisis. Aimed at restoring order and stability in the Rakhine state, the ceasefire is expected to halt the flow of Rohingya refugees to Bangladesh. China envisages that this will pave the way for the second stage: negotiations between Myanmar and Bangladesh to address the refugee problem. The third and final stage will involve the economic development of the Rakhine state to address the underlying causes of the violence (Global Times, November 20). China’s plan has reportedly found acceptance in Naypyitaw and Dhaka and marks the start of a new phase in Beijing’s involvement in the Rohingya conflict (FMPRC, November 20). China’s role has hitherto been limited to providing humanitarian aid to the Rohingya refugees and protecting Myanmar from international censure. Why is China now adopting a mediatory role in the conflict? And is it likely to succeed in bringing peace to a restive region?
China and the World Dealing With a Reluctant Power
By Evan A. Feigenbaum
In 2013, China launched an initiative to establish a new multilateral development institution, the Asian Infrastructure Investment Bank. The AIIB, Beijing argued, could help fill a multitrillion-dollar gap in financing for railways, roads, power plants, and other infrastructure in the world’s fastest-growing region. But the United States treated China’s proposal as a challenge to the existing regional and global development institutions that it had helped establish in the decades after World War II. Washington not only refused to join the bank itself but also launched a quiet diplomatic campaign to dissuade its allies from doing so either.
Saudi Arabia’s Arab Spring, at Last
By THOMAS L. FRIEDMAN
I never thought I’d live long enough to write this sentence: The most significant reform process underway anywhere in the Middle East today is in Saudi Arabia. Yes, you read that right. Though I came here at the start of Saudi winter, I found the country going through its own Arab Spring, Saudi style. Unlike the other Arab Springs — all of which emerged bottom up and failed miserably, except in Tunisia — this one is led from the top down by the country’s 32-year-old crown prince, Mohammed bin Salman, and, if it succeeds, it will not only change the character of Saudi Arabia but the tone and tenor of Islam across the globe. Only a fool would predict its success — but only a fool would not root for it.
ISIS’ Intelligence Service Refuses to Die
Vera Mironova, Ekaterina Sergatskova, and Karam Alhamad
In the darkness of a Mosul safe house in which ten Iraqi soldiers slept, bluish light still emanated from the mobile devices of two intelligence officers busy locating suicide cars, IEDs, and Islamic State (ISIS) bases, and tracking down the names of ISIS members. Providing that information were civilians deep in ISIS territory. On the other side of the battle, the same process was happening in reverse. And those operations were, in many ways, far more sophisticated. Even now that the terrorist organization is disintegrating, its intelligence bureau still presents a major challenge.
THE INFORMATION WAR
The Caliphate Is Destroyed, But the Islamic State Lives On
BY MICHAEL P. DEMPSEY
 The fall of the town of Abu Kamal in Syria and recent victories by Iraqi security forces in Qaim and Rawa in Iraq mark the collapse of the Islamic State caliphate. With the loss of these towns located along the Iraq-Syria border, the terrorist group no longer controls any major population center in either country. This represents quite a reversal for the Islamic State from its heady days of only three years ago, when it controlled vast swaths of territory, routinely extorted taxes from local businesses, exploited the region’s natural resources (especially oil), and governed a large percentage of the population of both countries. Those days are thankfully done — at least for now — and that’s a development worth celebrating.
The fall of the town of Abu Kamal in Syria and recent victories by Iraqi security forces in Qaim and Rawa in Iraq mark the collapse of the Islamic State caliphate. With the loss of these towns located along the Iraq-Syria border, the terrorist group no longer controls any major population center in either country. This represents quite a reversal for the Islamic State from its heady days of only three years ago, when it controlled vast swaths of territory, routinely extorted taxes from local businesses, exploited the region’s natural resources (especially oil), and governed a large percentage of the population of both countries. Those days are thankfully done — at least for now — and that’s a development worth celebrating.With technology, these researchers are figuring out North Korea’s nuclear secrets
By Anna Fifield
 There were reports going around last month that North Korea had tested another solid-fuel missile engine, a type of engine that can be deployed much faster than the older liquid-fueled ones. Kim Jong Un’s media outlets hadn’t bragged about it — as they had done previously — so the experts at the Middlebury Institute of International Studies’ nonproliferation center got to work. They figured that the North Korean rocket scientists would have used the same immovable concrete block they used for an engine test last year.
There were reports going around last month that North Korea had tested another solid-fuel missile engine, a type of engine that can be deployed much faster than the older liquid-fueled ones. Kim Jong Un’s media outlets hadn’t bragged about it — as they had done previously — so the experts at the Middlebury Institute of International Studies’ nonproliferation center got to work. They figured that the North Korean rocket scientists would have used the same immovable concrete block they used for an engine test last year.Stalingrad To El Alamein: What November 1942 Tells Us About Today's Russians - And The Brexit Mindset
by Ben Shepherd
Russia to the United Nations: Don’t Try to Stop Us From Building Killer Robots
BY PATRICK TUCKER
 Arms control advocates had reason for hope when scores of countries met at the United Nations in Geneva last week to discuss the future of lethal autonomous weapons systems, or LAWS. Unlike previous meetings, this one involved a Group of Governmental Experts, a big bump in diplomatic formality and consequence, and those experts had a mandate to better define lethal autonomy in weapons. But hopes for even a small first step toward restricting “killer robots” were dashed as the meeting unfolded. Russia announced that it would adhere to no international ban, moratorium or regulation on such weapons. Complicating the issue, the meeting was run in a way that made any meaningful progress toward defining (and thus eventually regulating) LAWS nearly impossible. Multiple attendees pointed out that that played directly toward Russia’s interests.
Arms control advocates had reason for hope when scores of countries met at the United Nations in Geneva last week to discuss the future of lethal autonomous weapons systems, or LAWS. Unlike previous meetings, this one involved a Group of Governmental Experts, a big bump in diplomatic formality and consequence, and those experts had a mandate to better define lethal autonomy in weapons. But hopes for even a small first step toward restricting “killer robots” were dashed as the meeting unfolded. Russia announced that it would adhere to no international ban, moratorium or regulation on such weapons. Complicating the issue, the meeting was run in a way that made any meaningful progress toward defining (and thus eventually regulating) LAWS nearly impossible. Multiple attendees pointed out that that played directly toward Russia’s interests.What the US U-turn on net neutrality means to India
 The US Federal Communications Commission has ruled to repeal net-neutrality guidelines, which had suggested equal rights to the internet for all, and prevented broadband providers from favouring their own apps and services. Commission chairman Ajit Pai, in a proposal, Restoring Internet Freedom, has said that the US government will "stop micromanaging the internet", from hereon.
The US Federal Communications Commission has ruled to repeal net-neutrality guidelines, which had suggested equal rights to the internet for all, and prevented broadband providers from favouring their own apps and services. Commission chairman Ajit Pai, in a proposal, Restoring Internet Freedom, has said that the US government will "stop micromanaging the internet", from hereon.The Cost Of Making The IPhone X
by Felix Richter
Nobody can get any extra information about you once you link your mobile to your UID
By RS Sharma
In November 2008, 10 members of Lashkar-e-Taiba carried out terrorist attacks across Mumbai, killing 164 persons. The attackers used at least three SIM (subscriber identification modules) cards purchased on the Indian side of the border with Bangladesh. Would the terrorists have been deterred if they could not obtain disposable SIM cards on bogus ID papers? Probably not. But the security agencies may have had a sliver of hope in nabbing them and preventing the deaths. In the dystopian view of alarmists, if we verify the subscriber’s identity using his Aadhaar number, it would destroy the privacy of citizens. That is far from the truth. What is retained by the telecom company after acquiring or verifying the subscriber’s ID is the record of authentication, not the biometric data itself. It is like a ‘verified’ tickmark in the record.
Why AI Is Tipping the Scales in the Development of Self-driving Cars
THE U.S. MILITARY IS PREPARING FOR WAR IN SPACE: WE'RE DRAFTING LAWS TO BE READY FOR IT
BY DALE STEPHENS AND DUNCAN BLAKE
A war in outer space sounds like the stuff of science fiction but it is something we need to consider. Its impact on everybody on Earth and its implications for future human space exploration would be devastating. Right now, there are laws that are relevant to the prospect of war in space, but currently it is unclear exactly how these might be applied. We and our colleagues from around the world—including experts from Australia, Canada, the U.K., Russia and China—are undertaking a multi-year project to provide a definitive guide on how law applies to military uses of outer space. The aim is to develop a Manual on International Law Applicable to Military uses of Outer Space (MILAMOS) that covers times of tension and outright hostility. The ultimate goal is to help build transparency and confidence between space-faring states.
Ransomware Attacks: An Increasingly Common Threat
 Ransomware attacks sourced to the Wanna Decryptor (a.k.a. Wannacrypt) virus have been identified in over 70 countries across Europe and Asia, as well as in the United States. Over 36,000 Wannacrypt cases have been detected worldwide. The ransomware exploits a vulnerability in Microsoft systems discovered initially by the U.S. National Security Agency, reportedly around 2013. This hacking tool was lifted in the summer of 2016 by a previously obscure group calling itself the “Shadow Brokers.”
Ransomware attacks sourced to the Wanna Decryptor (a.k.a. Wannacrypt) virus have been identified in over 70 countries across Europe and Asia, as well as in the United States. Over 36,000 Wannacrypt cases have been detected worldwide. The ransomware exploits a vulnerability in Microsoft systems discovered initially by the U.S. National Security Agency, reportedly around 2013. This hacking tool was lifted in the summer of 2016 by a previously obscure group calling itself the “Shadow Brokers.”Here’s how NATO is preparing for cyber operations
By: Mark Pomerleau
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/TD3IQLVBIBHRLFV6TPNVRIKSTA.net636051379069165919) It’s been more than a year since NATO declared cyberspace an operational domain of warfare akin to air, sea and land and while the alliance is still working its way through the practical implications of this pronouncement, behind the scenes leaders have taken a series of steps to fortify NATO’s cyber operations.
It’s been more than a year since NATO declared cyberspace an operational domain of warfare akin to air, sea and land and while the alliance is still working its way through the practical implications of this pronouncement, behind the scenes leaders have taken a series of steps to fortify NATO’s cyber operations.
The alliance’s initial focus has been primarily on cyber defense; strengthening NATO’s infrastructure and member nations pledging to take concrete steps to harden their systems as well.
The NATO Communications and Information Agency, is also undergoing a major IT modernization effort mainly focused on centralization and virtualization of services.
91st Cyber Brigade activated as Army National Guard’s first cyber brigade
By Cotton Puryear
 FORT BELVOIR, Va. — The Virginia National Guard activated the Bowling Green-based 91st Cyber Brigade as the Army National Guard's first cyber brigade at a Sunday ceremony at Fort Belvoir.
FORT BELVOIR, Va. — The Virginia National Guard activated the Bowling Green-based 91st Cyber Brigade as the Army National Guard's first cyber brigade at a Sunday ceremony at Fort Belvoir.
The new brigade provides training and readiness oversight for cyber units across 30 states and deploys personnel to meet the demands of growing cyber mission sets throughout the U.S. Army and Department of Defense. Virginia Gov. Terry McAuliffe and members of his cabinet joined Lt. Gen. Timothy Kadavy, director of the Army National Guard, Maj. Gen. Timothy P. Williams, the adjutant general of Virginia, as well as numerous other senior military and civilian leaders, fellow Soldiers and family members for the ceremony activating the brigade, also known as the Shadow Brigade.
Amazon’s New ‘Secret Region’ Promises Easier Sharing of Classified Data
Amazon Web Services unveiled a cloud computing region for the CIA and other intelligence community agencies developed specifically to host secret classified data.
The AWS Secret Region will allow the 17 intelligence agencies to host, analyze and run applications on government data classified at the secret level through the company’s $600 million C2Scontract, brokered several years ago with the CIA. AWS already provides a region for the intelligence community’s top secret data.
COMMISSIONING DA VINCI: DEVELOPING CREATIVITY, COMMUNICATION, AND CRITICAL THINKING IN TOMORROW’S MILITARY LEADERS
Rick Montcalm
 The future operating environment is not only complex, but unpredictable and potentially unknowable. That this prediction has been repeated so often as to risk making us numb to its significance—it is highlighted repeatedly in the Army Operating Concept and draft concept for Multi-Doman Battle—does not make it any less true. To succeed in such an environment, the Army will increasingly require leaders at all levels to demonstrate initiative to identify and exploit temporary windows of advantage while creating multiple dilemmas for the enemy.
The future operating environment is not only complex, but unpredictable and potentially unknowable. That this prediction has been repeated so often as to risk making us numb to its significance—it is highlighted repeatedly in the Army Operating Concept and draft concept for Multi-Doman Battle—does not make it any less true. To succeed in such an environment, the Army will increasingly require leaders at all levels to demonstrate initiative to identify and exploit temporary windows of advantage while creating multiple dilemmas for the enemy.On the Business Models of War
By Everett C. Dolman
 The American military is infatuated with the latest business models and their potential application for war. Bureaucracies are not agile organizations, as a rule, and just as the Pentagon institutes the previous decade’s top-selling business management method, it seems corporate America has already moved on to the Next Big Thing. A list of the 25 top-selling business management books, sorted by publication date, reads like a slightly delayed litany of ideal business-to-war manifestos.[1] Nonetheless, in his most recent memorandum, Secretary of Defense Jim Mattis echoed many of his predecessors in encouraging all members of the military to “bring business reforms to the Department of Defense.”
The American military is infatuated with the latest business models and their potential application for war. Bureaucracies are not agile organizations, as a rule, and just as the Pentagon institutes the previous decade’s top-selling business management method, it seems corporate America has already moved on to the Next Big Thing. A list of the 25 top-selling business management books, sorted by publication date, reads like a slightly delayed litany of ideal business-to-war manifestos.[1] Nonetheless, in his most recent memorandum, Secretary of Defense Jim Mattis echoed many of his predecessors in encouraging all members of the military to “bring business reforms to the Department of Defense.”25 November 2017
Professional Military Education - An Indian Experience
Maj Gen P K Mallick, VSM (Retd)
Professional Military Education (PME) has always been a critical component of developing military leaders. It is based on two key principles: train for certainty, so that military personnel gain and master the skills needed for known tasks and educate for uncertainty, so that they have the broad base of knowledge and critical thinking skills needed to handle unanticipated and unpredictable situations.
Litigating Tejas LCA’s quality & utility
by Bharat Karnad
 No pilot who has actually flown the indigenous Tejas light combat aircraft has had anything but the highest praise for the fighter plane. This includes two recent IAF chiefs. ACM Arup Raha called it “a wonderful aircraft” after a sortie in Bengaluru in 2016. The present CAS, ACM Dhanoa, after his LCA flight on the first day of AeroIndia 2017 seemed very satisfied and left, a project a staffer told me, with “a very positive aura”. One can, moreover, imagine that, as a seat of the pants flier, ACM Dhanoa couldn’t have resisted taking control from the back seat of the Tejas, with the National Flight Test Centre head AVM AP Singh in the lead cockpit. After all, Dhanoa is the first air chief to have flown solo — and that too a MiG-21 bis after becoming CAS, after ACM Anil Tipnis in the fin de siecle.
No pilot who has actually flown the indigenous Tejas light combat aircraft has had anything but the highest praise for the fighter plane. This includes two recent IAF chiefs. ACM Arup Raha called it “a wonderful aircraft” after a sortie in Bengaluru in 2016. The present CAS, ACM Dhanoa, after his LCA flight on the first day of AeroIndia 2017 seemed very satisfied and left, a project a staffer told me, with “a very positive aura”. One can, moreover, imagine that, as a seat of the pants flier, ACM Dhanoa couldn’t have resisted taking control from the back seat of the Tejas, with the National Flight Test Centre head AVM AP Singh in the lead cockpit. After all, Dhanoa is the first air chief to have flown solo — and that too a MiG-21 bis after becoming CAS, after ACM Anil Tipnis in the fin de siecle.Will Coca-Cola’s New India Strategy Have Fizz or Go Flat?
Chinese State Sponsored Hacking
By Sam Bocetta
For the past several years, China has denied any role in the exploitation of U.S. networks.Yet mounting evidence suggests China is involved in widespread hacking activity. In many cases, the sources of these attacks are difficult to trace, and therefore challenging to deter under current U.S.-Chinese cyber agreements. Both states signed a no-first-use agreement back in 2015, and some have argued the Chinese Communist Party’s control over hackers inside its own country is quite minimal. Given this, China’s claim that such attacks occur without the express guidance and sanction of central authority seems at least plausible.
China's Military Is Upgrading Its Hardware (and Its People)
James CharRichard A. Bitzinger
 In the period leading up to the recently concluded 19th Chinese Communist Party (CCP) congress, civil-military relations in post-Reform China had previously been viewed under the lens of Party-army relations. More recently, however, such a paradigm—following Xi Jinping’s consolidation of the trifecta of Party-state-military power—no longer seems true, with some People’s Liberation Army (PLA) watchers alluding to a shift towards a model of Xi Jinping-PLA relations. Notwithstanding that the PLA has supported its commander-in-chief in his consolidation of power in attaining his present unassailable position in the Party-state, the extent to which the CCP’s coercive forces can count on China’s new paramount leader to fully translate his considerable political clout into the former’s growing professionalization, however, is open to debate.
In the period leading up to the recently concluded 19th Chinese Communist Party (CCP) congress, civil-military relations in post-Reform China had previously been viewed under the lens of Party-army relations. More recently, however, such a paradigm—following Xi Jinping’s consolidation of the trifecta of Party-state-military power—no longer seems true, with some People’s Liberation Army (PLA) watchers alluding to a shift towards a model of Xi Jinping-PLA relations. Notwithstanding that the PLA has supported its commander-in-chief in his consolidation of power in attaining his present unassailable position in the Party-state, the extent to which the CCP’s coercive forces can count on China’s new paramount leader to fully translate his considerable political clout into the former’s growing professionalization, however, is open to debate.Tehran Is Winning the War for Control of the Middle East
 And there’s no indication that, despite Mohammed bin Salman’s bold moves, Saudi Arabia stands a chance of turning the tide.
And there’s no indication that, despite Mohammed bin Salman’s bold moves, Saudi Arabia stands a chance of turning the tide.
Saudi Arabia appears to be on a warpath across the Middle East. The Saudi-orchestrated resignation of Lebanese Prime Minister Saad Hariri, and Saudi officials’ bellicose rhetoric after the launch of a ballistic missile targeting Riyadh from Yemen, appear to herald a new period of assertiveness against Iranian interests across the Middle East.
Newly Declassified Documents Prove America's North Korea Strategy Has Failed
The State Department, the Defense Department and the White House were increasingly concerned either that the North Korean regime was hiding components of its plutonium program from the International Atomic Energy Agency (IAEA), or that it would exploit any negotiating track to stall the international community while improving its nuclear capacity. The motives of the Chinese, Pyongyang’s biggest trading partner and bankroller by far, were unclear—adding more complication to a problem that was already far too complicated.
Dealing With North Korea
By Paul Cook
So far this year, North Korea has conducted multiple nuclear weapon tests, a series of intercontinental ballistic missile tests, and has continued to prioritize the development of nuclear weapons over the well-being of its own citizens. North Korean dictator Kim Jong Un assumes that provoking the U.S., threatening our allies, and developing nuclear weapons will secure the future of his regime. He is wrong in this assumption. This threat is critical to the national security of the United States and for the safety of the world.
North Korea has disregarded almost every agreement and commitment it has made to the U.S. and our allies. The regime has also demonstrated a proclivity for breaking international law and undermining international oversight of nuclear development. It is imperative that as North Korea’s nuclear capability increases, we continue to put pressure on Kim Jong Un and his regime.
Germany Is Europe’s Newest Problem
JUDY DEMPSEY
“Today there was no progress but rather there were setbacks because specific compromises were questioned,” Free Democrat leader Christian Lindner said. “It is better not to rule than to rule the wrong way. Goodbye!”
Merkel, long known for her skills at forging compromises, was visibly taken aback by Lindner’s decision.
“It’s a day at the very least for a profound examination of Germany’s future,” Merkel told reporters after the talks ended. “As chancellor, as caretaker chancellor, I will do everything to make sure this country continues to be well governed through the tough weeks ahead,” she added.
Germany’s preliminary coalition talks collapse
 AS COALITION talks in Berlin dragged on through Sunday evening there were rumours of progress, of a nearing accord. After four weeks Angela Merkel’s Christian Democrats CDU, the Bavarian Christian Social Union (CSU), the pro-business Free Democrats (FDP) and the Greens had sailed past two self-imposed deadlines. Now, perhaps, a deal was close. But not long before midnight everything changed. With the rest of the FDP leadership at his side, Christian Lindner appeared without warning outside the negotiation venue and announced that he was breaking off talks.
AS COALITION talks in Berlin dragged on through Sunday evening there were rumours of progress, of a nearing accord. After four weeks Angela Merkel’s Christian Democrats CDU, the Bavarian Christian Social Union (CSU), the pro-business Free Democrats (FDP) and the Greens had sailed past two self-imposed deadlines. Now, perhaps, a deal was close. But not long before midnight everything changed. With the rest of the FDP leadership at his side, Christian Lindner appeared without warning outside the negotiation venue and announced that he was breaking off talks. Terrorism Spreading but Less Deadly
By Murray Ackman
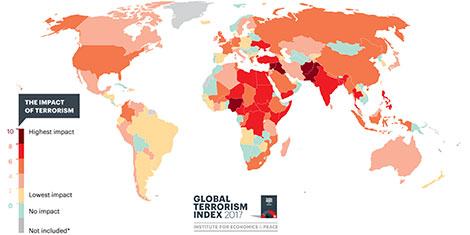 The fifth edition of the Global Terrorism Index highlights that for the second consecutive year, deaths from terrorism have decreased. There were 22 per cent fewer deaths when compared to the peak of terror activity in 2014, with significant declines in terrorism in the epicentres of Syria, Pakistan, Afghanistan and Nigeria. Collectively these four countries, which are among the five most impacted by terrorism, recorded 33 per cent fewer deaths. The annual Global Terrorism Index (GTI) is produced by the Institute for Economics & Peace (IEP) and provides a comprehensive summary of the key global terrorism trends in analysing the direct and indirect impact of terrorism in 163 countries.
The fifth edition of the Global Terrorism Index highlights that for the second consecutive year, deaths from terrorism have decreased. There were 22 per cent fewer deaths when compared to the peak of terror activity in 2014, with significant declines in terrorism in the epicentres of Syria, Pakistan, Afghanistan and Nigeria. Collectively these four countries, which are among the five most impacted by terrorism, recorded 33 per cent fewer deaths. The annual Global Terrorism Index (GTI) is produced by the Institute for Economics & Peace (IEP) and provides a comprehensive summary of the key global terrorism trends in analysing the direct and indirect impact of terrorism in 163 countries.War, Nuclear War and the Law
By George Friedman
The U.S. Senate held hearings last week on the president’s authority to use nuclear weapons. The trigger for the hearings was the North Korea situation, and the fear among some that President Donald Trump might launch a reckless nuclear attack against the North Koreans. The question senators were asking was what the power of the president was to initiate nuclear war unilaterally.
This has long been a burning question, but one that has been intentionally ignored for decades. But this question involves not only the use of nuclear weapons, but the president’s authority to initiate all kinds of war without congressional approval. The Constitution states that the president is commander in chief of the armed forces. It also says that Congress has the power to declare war. On the surface, this seems a fairly clear system. The president is in command of the military; however, the authority to go to war rests with Congress.
The Kremlin’s Trojan Horses 2.0
BY ATLANTIC COUNCIL
“Russia’s interference in the US presidential election in 2016 sent a signal to the West: democratic societies are deeply vulnerable to foreign influence,” writes Dr. Alina Polyakova in The Kremlin’s Trojan Horses 2.0: Russian Influence in Greece, Italy, and Spain, a new report from the Atlantic Council’s Eurasia Center. Following a successful installment on Russian influence in France, Germany, and the United Kingdom, this report examines Russian political presence in Southern Europe.
Israel: The Making of a Cyber Power - Case Study
On September 14, 2017, CCHS convened a Symposium on Trends in Technology and Digital Security. Four panels addressed emerging threats and their implications for security policy, with a focus on digital infrastructure protection and anticipatory analysis. In a series of Issue Briefs, CCHS shares the findings and recommendations that emerged from the Symposium, primarily on a not-for-attribution basis. This fifth Brief in the series is a case study of the evolution of Israel as a cyber power.
The EU’s Revised Cybersecurity Strategy
In September 2017 the EU updated its 2013 Cyber Security Strategy. The new version is intended to improve the protection of Europe’s critical infrastructure and boost the EU’s digital self-assertiveness towards other regions of the world. But the reformed strategy leaves open a number of questions as to how its objective of an “open, safe and secure cyberspace” will be credibly defended, both internally and externally. The EU has neither properly defined resilience or deterrence nor made sufficiently clear how it intends to overcome institutional fragmentation and lack of legal authority in cybersecurity issues. Moreover, controversial topics – such as the harmonisation of criminal law or the use of encryption – have been entirely omitted. Member states should abandon their standalone efforts and speed up the legal regulation of cybersecurity at the EU level.
Subscribe to:
Posts (Atom)