By Brandon Valeriano and Benjamin Jensen
Great‐power competition in the 21st century increasingly involves the use of cyber operations between rival states. But do cyber operations achieve their stated objectives? What are the escalation risks? Under what conditions could increasingly frequent and sophisticated cyber operations result in inadvertent escalation and the use of military force? The answers to these questions should inform U.S. cybersecurity policy and strategy.
In the context of recent shifts in cybersecurity policy in the United States, this paper examines the character of cyber conflict through time. Data on cyber actions from 2000 to 2016 demonstrate evidence of a restrained domain with few aggressive attacks that seek a dramatic, decisive impact. Attacks do not beget attacks, nor do they deter them. But if few operations are effective in compelling the enemy and fewer still lead to responses in the domain, why would a policy of offensive operations to deter rival states be useful in cyberspace?
We demonstrate that, while cyber operations to date have not been escalatory or particularly effective in achieving decisive outcomes, recent policy changes and strategy pronouncements by the Trump administration increase the risk of escalation while doing nothing to make cyber operations more effective. These changes revolve around a dangerous myth: offense is an effective and easy way to stop rival states from hacking America. New policies for authorizing preemptive offensive cyber strategies risk crossing a threshold and changing the rules of the game.
Cyberspace to date has been a domain of political warfare and coercive diplomacy. An offensively postured cyber policy is dangerous, counterproductive, and undermines norms in cyberspace. Many have promoted the idea of a coming “Cyber Pearl Harbor,” but instead the domain is littered with covert operations meant to manage escalation and deter future attacks. Cyber strategy and policy must start from an accurate understanding of the domain, not imagined realities.
Senior leaders throughout the federal government should consider a more prudent and restrained approach to cyber operations. We argue for a defensive posture consisting of limited cyber operations aimed at restraining rivals and avoiding escalation. At the same time, the United States should focus on protective measures to make U.S. systems less vulnerable and on sharing intelligence with allies and partners. A policy of restraint that maintains control over the weapons of cyber war is strategically wise.
Introduction
In the summer of 2017, the Trump administration faced a series of stark choices for compelling North Korea to abandon its ballistic missile tests and its nuclear program. Under the previous administration, the United States used cyber operations in an effort to degrade North Korean weapons development through targeting “command, control, telemetry and guidance systems, before or during a North Korean missile test launch.”1 These cyber operations failed to halt North Korean weapons development, but they demonstrated U.S. capability while avoiding escalation.
This approach was consistent with the Department of Defense 2015 Cyber Strategy, which called for developing “viable cyber options [that] . . . control conflict escalation and shape the conflict environment at all stages.”2 In developing these options against China and other powers, Tom Bossert, Trump’s former homeland security adviser, reportedly argued for coordinating these covert signals with economic policy and “other elements of national power to prevent bad behavior online.”3 President Trump’s response, according to journalist Bob Woodward: “you and your cyber . . . are going to get me in a war—with all your cyber shit.”4
This episode illustrates the core questions regarding offensive cyber operations. In the 21st century, great powers wage a constant battle in the digital shadows by exploiting the connectivity of our world to undermine rivals. But do cyber operations actually achieve stated foreign policy objectives? Relatedly, what are the escalation risks? Under what conditions could increasingly frequent and sophisticated cyber operations result in inadvertent escalation? The answers to these questions should inform U.S. cybersecurity policy.
Cyber operations to date have not been escalatory or particularly effective in decisively achieving desired outcomes. Recent policy changes and strategy pronouncements by the Trump administration, however, could make escalation more likely while doing nothing to improve effectiveness. These changes are driven by a dangerous myth that offense is an effective and easy way to stop rival states from hacking America.
New policies for authorizing preemptive offensive cyber strategies risk crossing a threshold and changing the rules of the game. Cyberspace, to date, has been a domain of political warfare and coercive diplomacy, a world of spies developing long-term access and infrastructure for covert action, not soldiers planning limited-objective raids. Recent policy shifts appear to favor the soldier over the spy, thus creating a new risk of offensive cyber events triggering inadvertent escalation between great powers.
Senior leaders throughout the federal government should consider a more prudent and restrained approach to cyber operations. Building on Sir Julian Corbett’s Principles of Maritime Strategy, one of the preeminent works in 20th century military theory, we argue for a defensive posture consisting of limited cyber operations aimed at restraining rivals and avoiding escalation.5 This approach counsels stepping back from preemption and focusing on sharing intelligence and hardening targets (that is, updating systems to repair existing vulnerabilities). The United States should exercise restraint and avoid preemptive strikes against great powers in cyberspace.

Cyber Command’s New, More Aggressive Policy
In April 2018, United States Cyber Command released a new vision statement calling for “persistent action”6 to maintain cyber superiority.7 The document echoed other major studies portraying the United States as ceding the digital high ground to adversaries. For example, a 2018 Defense Science Board study claimed the “the United States has fallen behind its competitors in the cyber domain, both conceptually and operationally.”8 Similarly, the Cyber Command vision statement portrays other great powers as increasingly capable of deploying sophisticated cyber actions against the United States. Major competitors, according to the statement, are using cyber operations to alter the long-term balance of power, short of military force.9 In using cyber operations to undermine American power, it claims these actors—especially strategic competitors such as Russia and China—are threatening not just the U.S. military but the entire global infrastructure and open exchange of information. In fact, according to General Paul M. Nakasone, commanding general of Cyber Command, “the environment we operate in today is truly one of great-power competition, and in these competitions, the locus of the struggle for power has shifted towards cyberspace.”10
In response to these threats, Cyber Command contends that the United States needs a more aggressive strategy. Cyber Command envisions a new era of persistent action that retains cyber superiority for the United States. Drawing on military doctrine, the document defines cyberspace superiority as “the degree of dominance in cyberspace by one force that permits the secure, reliable conduct of operations by that force, and its related land, air, maritime, and space forces at a given time and place without prohibitive interference by an adversary.” In this view, the United States must command the digital commons to ensure other nonmilitary actors can access and use the new domain. Doing so requires persistence, defined as “the continuous ability to anticipate the adversary’s vulnerabilities, and formulate and execute cyberspace operations to contest adversary courses of action under determined conditions.”11
This approach increasingly sees preemption as the only viable path to security. U.S. cyber operations will “influence the calculation of our adversaries, deter aggression, and clarify the distinction between acceptable and unacceptable behavior in cyberspace,” and, as a result, “improve the security and stability of cyberspace.”12 Achieving this new stability through persistent action depends on “scaling to the magnitude of the threat, removing constraints on [U.S.] speed and agility, and maneuvering to counter adversaries and enhance national security.”13 In other words, the United States must go on the offense and preempt threats in the cyber domain as a means of ensuring stability.
Cyber Command emphasizes a constant state of competition beneath the threshold of armed conflict and underscores the need for faster responses to adversary attacks. This parallels broader policy developments in the Trump administration. First, persistent action is linked to the concept of “contact” in the 2018 National Defense Strategy.14 The new defense strategy, along with the 2018 National Security Strategy, envisions constant competition between great powers as the norm in the 21st century.15 Renewed great-power competition requires a global operating model comprised of four layers (contact, blunt, surge, and homeland) designed to help the United States “compete more effectively below the level of armed conflict; delay, degrade, or deny adversary aggression; surge war-winning forces and manage conflict escalation; and defend the U.S. homeland.”16 In this model, cyberspace becomes another domain in which the United States must achieve command of the commons to guarantee the larger international order.
Securing command of the commons in the face of increasing cyber operations by China and Russia requires a policy framework that accelerates cyber offense. Offensive cyber operations entail missions “intended to project power in and through foreign cyberspace.”17 In August 2018, Trump granted the military the initiative to launch offensive cyber operations with what appears to be little interagency consultation or coordination.18 Cyberspace became a domain for soldiers, not just networks of spies. The move represented a dramatic shift from the restraints on cyber operations imposed by the Obama administration.
Obama’s Presidential Policy Directive 20 originally specified the conduct and content of cyberspace operations. Secretly issued in October 2012 after Congress failed to provide guidance for cyber operations, the directive authorized offensive cyber operations under certain conditions and only after careful interagency vetting.19 All operations had to be consistent with American values and had to balance the effectiveness of operations with the risk to all targets, as determined by the president and the national security adviser.20
This policy framework required decisionmakers to ask whether more conventional operations would be better suited for the target as well as the extent to which the operation might compromise other espionage and cyber operations. It also sought to ensure cyber effects were nonlethal and limited in magnitude: a clear attempt to avoid escalation. Similarly, the guidelines portrayed cyberspace as dynamic and boundless, increasing the risk that operations spill over to affect partner countries or impact American citizens.
In moving to the new framework, the Trump administration appears to be changing the rules of the game in cyberspace. North Korea, Iran, Russia, and China have long been exploiting the digital connectivity of our world for covert operations to gain a position of advantage. They have exhibited less restraint or concern for the consequences of militarizing cyberspace than the United States. Yet, what the cyber hegemon (the United States) does defines the character of cyber operations much more than these secondary actors.21 Despite increasingly sophisticated operations, between 2000 and 2016 cyberspace was a domain defined by political warfare and covert signaling to control escalation more than it was an arena of decisive action.22 Taking a more offensive posture and preempting threats at their source, an action implied by the Cyber Command Vision Statement, has the potential to change the character of cyber operations, and through it, 21st century great-power competition.23
The Character of Cyber Operations, 2000–2016
Evaluating the policy debate about offensive cyber operations requires empirically describing prevailing patterns and trends associated with how rival states employ their capabilities. Just as it is perilous to describe all wars based on observations of crucial cases such as the First World War, it is similarly dangerous to assume that high-profile cases such as the Stuxnet operation, which degraded Iranian nuclear capabilities, accurately represent all cyber strategy. Rather, developing cyber policy options and supporting strategies should start with a clear understanding of how states use the digital domain to achieve a position of advantage in long-term competition.
Between 2000 and 2016, there have been 272 documented cyber operations between rival states.24 These exchanges are best thought of as major operations involving a foreign policy impact. Each operation therefore might involve thousands, if not millions, of individual incidents as adversaries hijack computer networks to launch distributed denial of service attacks (DDoS) or use sustained spear-phishing campaigns to gain access to key systems. Like other forms of covert action, for every cyber operation we learn about, there are surely countless others we do not know about, as well as failed access attempts.
Using the Dyadic Cyber Incident Dataset, we can categorize these operations based on three major tactics: disruption, espionage, and degradation.25 Cyber disruptions are low-cost, low-pain initiatives, such as DDoS attacks and website defacements, that harass a target to signal resolve and gain a temporary position of advantage.26 Cyber espionage reflects efforts to alter the balance of information in a way that enables coercion.27 Cyber degradations are higher-cost, higher-pain-inducing efforts that seek to degrade or destroy some aspect of the target’s cyberspace networks, operations, or functions.28 As strategies for achieving a position of advantage, degradation attacks typically involve coercion or efforts to compel or deter an adversary.29
To date, cyber operations do not appear to produce concessions by themselves. Offense, whether disruption, espionage, or degradation, does not produce lasting results sufficient to change the behavior of a target state.30 Only 11 operations (4 percent) appear to have produced even a temporary political concession, with the majority associated with sustained, multiyear counterespionage operations by U.S. operatives usually targeting China or Russia.31 Furthermore, each of these operations involved not just cyber actions, but other instruments of national power, such as diplomatic negotiations, economic sanctions, and military threats.32
Under the Obama administration, these operations were calibrated to limit escalation risks and took place alongside a larger series of diplomatic maneuvers designed to manage great-power relationships. For example, the United States used an interagency response to Chinese hacking that included covert retaliation but also involved pursuing a 2015 agreement to limit cyber-enabled economic warfare.33 In response to Russian actions, the United States pursed a mix of sanctions, diplomatic maneuvers, and cyber actions.
This strategy of combining active defense and coercive diplomacy, the use of positive and negative instruments of power to alter adversary behavior, was also on display in Buckshot Yankee, the code name given to the U.S. retaliation against a massive intrusion of Defense Department networks by Russia in 2008.34 Notably, many in the cybersecurity community view such activities as defensive counterstrikes designed to raise the costs of future adversary incursions into U.S. networks, rather than viewing them as preemptive offensive actions.35 Cyber operations rarely work in isolation, and when they do, they tend to involve very sophisticated capabilities that impose costs and risks on the attacker.36 Because such attacks can degrade or even destroy the target’s networks and operations in the short term, they can also undermine espionage operations that rely on gathering information over the long term. Degradation attacks therefore make up the minority (14.76 percent) of documented operations between rival states. The majority of cyber operations were limited disruptions and espionage.
It is thus not surprising that given the limited objectives of most cyber operations, to date rival states have tended to respond proportionally or not at all. Returning to the data, between 2000 and 2016, only 89 operations (32.72 percent) saw a retaliatory cyber response within one year. Of those, 54 (60.7 percent) were at a low-level response severity (e.g., website defacements, limited denial of service attacks, etc.). Table 1 in the appendix compares the severity scores for cyber operations between rival states between 2000 and 2016.37 When rival states do retaliate, the responses tend to be proportional: that is, they tend to match the severity of the initial attack.38
Low-level responses beget low-level counterresponses as states constantly engage in a limited manner consistent with the ebbs and flows of what famed Cold War nuclear theorist Herman Kahn called “subcrisis maneuvering.”39 Rarely does a response include an increase in severity. Instead, we witness counterresponses of a similar or lower level than the original intrusion or a response outside the cyber domain (for example, economic sanctions or legal indictment of specific individuals). The engagement is persistent but managed, and often occurs beneath an escalatory threshold.40 As seen in Table 2 in the appendix, this behavior appears to apply equally to each possible cyber strategy: disruption, espionage, and degradation. Espionage saw little retaliatory escalation, while disruption and degradation both exhibited more low-level responses.
Of the remaining 35 operations that prompted retaliation, 25 (71.4 percent) were related to U.S. active defense responses to repeated Russian and Chinese cyber operations. That is, the United States preferred to wait on adversary networks, develop intelligence, and retaliate with precise strikes designed to undermine specific threats. This strategy was not preemptive. Consistent with the idea of active defense, the strategy is best thought of as a counterattack that exploits rival network intrusions.
Cyber operations also offer a means of signaling future escalation risk as well as a cross-domain release valve for crises. Rival states use cyber operations as a substitute for riskier military operations. Consider the standoff between Russia and Turkey in 2016. After a Turkish F-16 shot down a Russian Su-24 Fencer, a wave of DDoS attacks hit Turkish state-owned banks and government websites.41 Similarly, China is responding to U.S. tariffs and increased freedom of navigation operations—provocatively sailing U.S. warships in waters that China claims—with increased cyber activity targeting military networks.42 Russia is using a broad-front cyber campaign in response to Western sanctions, infiltrating targets ranging from the anti-doping agencies and sports federations to Westinghouse, which builds nuclear power plants, and the Hague-based Organization for the Prohibition of Chemical Weapons.43 Rather than escalate with conventional military operations, cyber operations offer rivals a way to respond to provocations without significantly increasing tensions in a crisis. Better to have a Russian DDoS attack temporarily shut down Turkish networks than for Russian long-range missiles to target Turkish military bases.
The Myth of the Offense
Contrary to observed patterns of limited disruption and espionage, Cyber Command sees cyberspace as a domain fraught with increasing risk, where great powers such as China and Russia will undermine American power. The only solution, from this perspective, is to go on the offense. Yet, the benefits of an offensive posture, especially in cyberspace, are mostly illusory to date. Instead, the cyber domain tends to be optimized for defense and deception, not decisive offensive blows. Not only is offense likely the weaker form of competition in cyberspace, it also risks inadvertent escalation. The fear, suspicion, and misperception that characterize interstate rivalries exacerbate the risk of offensive action in cyberspace.
Cyber Command’s 2018 persistent-action strategy aims to “expose adversaries’ weaknesses, learn their intentions and capabilities, and counter attacks close to their origins.”44 Put in simple terms, the best defense is a good offense: get on adversary networks and stop cyber operations targeting the United States before they occur. Under this strategy, offensive cyber operations will also be preemptive in that they are designed to “contest dangerous adversary activity before it impairs [U.S.] national power.”45 To use another sports metaphor, come out swinging. Go on the offense first and establish escalation dominance (that is, demonstrating such superior capabilities over the target state that it can’t afford to escalate in response).46
According to Cyber Command, preemptive strikes will “impose . . . strategic costs on our adversaries, compelling them to shift resources to defense and reduce attacks.”47 Whether through punishment, risk, or denial strategies, offensive actions theoretically alter the target’s behavior by increasing the expected costs of targeting U.S. interests.48 Offensive action, according to this thinking, deters future aggression by signaling resolve and establishing escalation dominance. Yet, there are well-established reasons to doubt that offensive options produce the intended results in cyberspace.
Defense and Deception
The rationale behind persistent action—that the best defense is a good offense—is deeply flawed. In fact, most military and strategic theory holds that the defense is the superior posture.49 For example, Sun Tzu describes controlling an adversary to make their actions more predictable, and hence easy to undermine, by baiting them to attack strong points.50 The stronger form of war is a deception-driven defense: confusing an attacker so that they waste resources attacking strong points that appear weak. This parallels cybersecurity scholars Erik Gartzke and Jon Lindsay’s claim that cyberspace is not offense dominant, but deception dominant.51 Rather than persistent action and preemptive strikes on adversary networks, the United States needs persistent deception and defensive counterstrikes optimized to undermine adversary planning and capabilities.
Fear and the Security Dilemma
New policy options proposed by Cyber Command and the Trump administration risk exacerbating fear in other countries and creating a self-reinforcing spiral of tit-for-tat escalations that risk war even though each actor feels he is acting defensively—or, as it is called in the scholarly literature, a security dilemma.52 As shown above, most cyber operations to date have not resulted in escalation. The cyber domain has been a world of spies collecting valuable information and engaging in limited disruptions that substitute for, as well as complement, more conventional options. Shifting to a policy of preemptive offensive cyber warfare risks provoking fear and overreaction in other states and possibly producing conflict spirals. Even limited-objective cyber offensive action defined as “defending forward” can be misinterpreted and lead to inadvertent escalation.53 As the historian Cathal Nolan puts it, “intrusions into a state’s strategically important networks pose serious risks and are therefore inherently threatening.”54
More worryingly, with a more offensive posture, it will be increasingly difficult for states to differentiate between cyber espionage and more damaging degradation operations.55 What the United States calls defending forward, China and Russia will call preemptive strikes. Worse still, this posture will likely lead great powers to assume all network intrusions, including espionage, are preparing the environment for follow-on offensive strikes. According to cybersecurity scholar Ben Buchanan, “in the [aggressor] state’s own view, such moves are clearly defensive, merely ensuring that its military will have the strength and flexibility to meet whatever comes its way. Yet potential adversaries are unlikely to share this perspective.”56 The new strategy risks producing a “forever cyber war” prone to inadvertent escalation because it implies all cyber operations should be interpreted as escalatory by adversaries.57
The Myth of Decisive Cyber Victory
There is a tendency in the military profession, at least in the United States and Europe, to uphold the concept of decisive battle as central to the Western way of war.58 Often, disruptive technologies—from strategic bombers in the mid-20th century to cyber operations in the 21st century—are seen as providing decisive offensive advantages in crises. In the interwar period between the world wars, airpower enthusiasts argued that bombers would reliably reach their targets, forcing political leaders to end hostilities or face the prospect of destroyed cities and economic collapse.59
Yet the search for decisive battle is often an elusive, if not dangerous, temptation for military planners and policymakers. In a comparative historical treatment of major 19th- and 20th-century battles, Nolan argues that “often, war results in something clouded, neither triumph nor defeat. It is an arena of grey outcomes, partial and ambiguous resolution of disputes and causes that led to the choice of force as an instrument of policy in the first place.”60 Decisive victories in any one battle are rare. Adversaries can refuse to fight.61 They can even signal resolve through demonstrating their ability to endure pain.
Planning and Assessment Pathologies
The new policy framework for offensive cyber operations risks compounding common pathologies associated with strategic assessments and planning. 62 Removing interagency checks increases the risks that an operation will backfire on the attacker or compromise ongoing operations.
Misperception is pervasive in insulated decisionmaking processes for several reasons.63 First, small groups unchecked by bureaucracy tend to produce narrow plans prone to escalation during crises.64 Second, leaders often give guidance to planners during crises that reflects their political bias or personality traits rather than a rational assessment of threats and options.65 Third, offensive bias in planning may have little to do with the actual threat and more to do with a cult of the offensive and the desire of officers to ensure their autonomy and resources.66 Removing interagency checks therefore risks compounding fundamental attribution errors and other implicit biases. Cyber operations are too important to be left to the generals at Cyber Command alone.
An Alternative Approach: Cyber Defense-in-Being
Rather than going on the offensive, the United States should develop a cyber posture that signals restraint and builds an active defense network. This network should adopt key tenets of Julian Corbett’s concept of a “fleet-in-being.” For Corbett, writing in 1911, the operative strategic problem for the British Empire was securing global interests. Regional adversaries could overwhelm local defenses and achieve fait accompli victories, and the British could not be everywhere at once. They had to adopt a fleet-in-being, a distributed network of cruisers (mobility) and fortified ports (strong points) that increased the costs of adversary aggression, buying time for diplomacy and, should it fail, for mobilizing sufficient forces for a counterattack. This dispersed network signaled resolve and generated options by disputing who could command the seas. A fleet-in-being “endeavor[ed] by active defensive operations to prevent the enemy either securing or exercising control for the objects he has in view.” This strategy thus advocated “avoiding decisive action by strategical or tactical activity, so as to keep our fleet-in-being till the situation develops in our favor.”67
In cyber operations, the United States requires a global network organized around active defenses rather than offensive actions designed to preempt other great powers. This network requires intelligence sharing and target hardening with partners, including industry, to reduce adversaries’ expected benefits of cyber operations. Just as new technologies enabled new theories of victory for Corbett, digital connectivity puts a premium on deception and active defense in cyberspace.
Active Defense
In military theory, active defense is “the employment of limited offensive action and counterattacks to deny a contested area or position to the enemy.”68 The term comes from Chinese strategic theory and calls for a defensive posture that “strik[es] only after the opponent has struck first.”69 In the cyber context, active defense utilizes deception to expose the attacker’s espionage and offensive operations in order prepare counterattacks.70 With respect to persistent engagement, defending forward risks undermining the ability to isolate adversary capabilities and, if need be, degrade them through targeted counterattacks designed to limit escalation risks.
Deception and defense produce a position of advantage.71 A connected society is inherently vulnerable. New hardware and endless software updates produce new vulnerabilities at a continual, even if variable, rate. The only true security comes from making adversaries doubt the wisdom of attack.
One technique that can be used to this effect is to lure would-be attackers into network traps, undermining their confidence in their own intelligence and capabilities. For example, a honeypot is false data that adversaries find so alluring that they attempt to access it. This allows defenders to either identify adversary cyber espionage capabilities or deliver their own payloads to rival networks. Thus, through deception, active defense can change the expected benefits of offensive cyber operations and effectively deter adversaries. The opposition must worry that all of their cyber espionage operations might be revealed, or worse, used as vectors for a counterattack.
Hardening Targets
Target hardening is a concept that emerged in the early Cold War. Based on a 1954 study on the vulnerability of U.S. forces,72 Albert Wohlstetter and Fred Hoffman advocated, among other things, that U.S. forces use passive measures (geographic dispersion, constantly airborne platforms, etc.) and active measures (hardened silos) to reduce vulnerability and ensure a “delicate balance of terror.”73
In cyberspace, target hardening also involves active and passive measures.74 In addition to active defense, active measures include investments in human capital and new technology that make it more difficult to access a network. These can range from employing “white hat” hackers, ethical computer hackers who penetrate systems in order to identify vulnerabilities, to updating cyber defensive systems regularly. Passive measures can range from education (e.g., the importance of updating software and avoiding suspicious messages and websites) to ensuring accounts have two-factor authentication—measures that minimize the number of easy attack vectors.
If the goal of the recently released National Cyber Strategy is cost-imposition—increasing the costs of enemy activity—the question is how best to alter a rival’s cost-benefit calculation in cyberspace. The current strategy relies on offense: operating forward to thwart attacks preemptively. In theory, a rival is deterred by the expectation of punishment for accessing U.S. networks. Yet, an alternative approach would be to adopt a defensive form of cost imposition by targeting hardening and increasing the marginal cost of gaining access to the system. That is, if rivals want to gain access to a network they have to invest more resources and take advantage of more complex—and rare—vulnerabilities.
Cost imposition in defense starts with target hardening, and worryingly, the United States has neglected this important measure. As a recent Government Accountability Office report makes clear, the Department of Defense has not prioritized security in weapons systems and there are weaknesses throughout the entire infrastructure.75 According to the study, “from 2012–2017, DOD testers routinely found mission-critical cyber vulnerabilities in nearly all weapon systems that were under development. Using relatively simple tools and techniques, tests were able to take control of these systems and largely operate undetected.”76 The Pentagon should address these deficiencies and increase the expected costs of gaining access to U.S.—and allied—networks.
In cyber operations, the more money adversaries must spend on accessing and exploiting a key network, such as the critical infrastructure of the financial system, the less money they have to spend on conducting other attacks. Coupled with active defense and the use of deception to undermine adversary confidence in their offensive and espionage efforts, target hardening changes the projected benefits of cyber operations. Defensive options, such as hardening targets and increasing societal resiliency, ensure the target is difficult to coerce. As Buchanan notes, “no cybersecurity approach is credible unless it begins with a discussion of the vital role of baseline defenses.”77 These defenses, consistent with the Department of Homeland Security strategy, start with “identifying the most critical systems and prioritizing protection around those systems.”78 Cyber strategy should prioritize hardening key targets while seeding the network with digital traps—active defenses—that undermine adversary offensive and espionage options.
Intelligence Sharing and Coordination
There are also benefits to sharing threat intelligence with industry and allies. The United States operates a global security network that connects not just treaty allies but businesses and civil society actors.79 Any cyber strategy must embrace this fact as a source of strength, not a point of vulnerability. A greater number of actors identifying adversary cyber operations provides early warning indicators and reveals adversary capabilities.
To date, intelligence sharing associated with cyber operations has been prone to interagency debate and coordination challenges. There are organizational seams, such as the divide between the FBI and CIA before the September 11th terrorist attacks, that often limit intelligence sharing and create barriers to effective response within the federal government.80 This dilemma is compounded with respect to alliance partners and industry. States and many other organizations tend to stovepipe information and undermine effective coordination based on security risks. Yet, closing off information in a network limits responsiveness.
Rather than limit information sharing, the United States should reengage processes such as the Obama administration’s Vulnerabilities Equities Policy, which sought disclosures of newly discovered and unknown malware that might pose a global threat.81 Sharing threat intelligence is central to not just interagency coordination, but working with partner states, businesses, and civil society. In order to strengthen the defense of the network through depth, the United States will need to assume risk in sharing information, and hence lose some offensive options. This includes working with nontraditional actors, such as the white hat hacker community, which conducts probes in order to help strengthen networks from adversary attacks.82 It also implies sacrificing some espionage and offensive cyber options to ensure partners can patch their networks and update their defenses.
Conclusion
Cyber policy and strategy should favor restraint over offense in protecting the digital commons. In MIT political scientist Barry Posen’s proposed grand strategy, restraint calls for fewer forward-deployed forces and less coordination with partners.83 In a cybersecurity context, restraint implies preserving the digital commons for commercial and social interests, thus limiting military action to the greatest extent possible.
Restraint can also help shape norms in cyberspace and make escalation taboo.84 To date, restraint has largely been the prevailing norm in this domain. Restraint has prevailed not so much as a prescribed foreign policy strategy, but because more aggressive tactics are ineffective, and states therefore use them sparingly.85 Data on cyber actions from 2000 to 2016 suggest a restrained domain with few aggressive attacks that seek a dramatic impact. Attacks do not beget attacks, nor do they deter them. The policy discourse is inconsistent with these observations. If few operations are effective in manipulating the enemy and fewer still lead to responses in the domain, why would a policy of offensive operations be useful in cyberspace?
For a variety of reasons, including the ineffectiveness of cyber operations and the fear of weapons proliferation, a normative system of restraint has gradually emerged in cyberspace. A policy of restraint that maintains control over the weapons of cyber war is therefore appropriate and strategically wise. Loosening the rules of engagement in pursuit of a more offensive posture, as the Trump administration advocates, violates norms and can lead to disastrous consequences for the entire system.
Given the ambiguous nature of signals in cyberspace, it is difficult to be sure that an offensive operation will be correctly interpreted as a warning shot designed to get adversaries to back down. Platitudes like “the best defense is a good offense” are best left for sports, not international politics. The evidence suggests that in cyberspace, the best defense is actually a good defense.
Appendix
Table 1
Retaliation dynamics
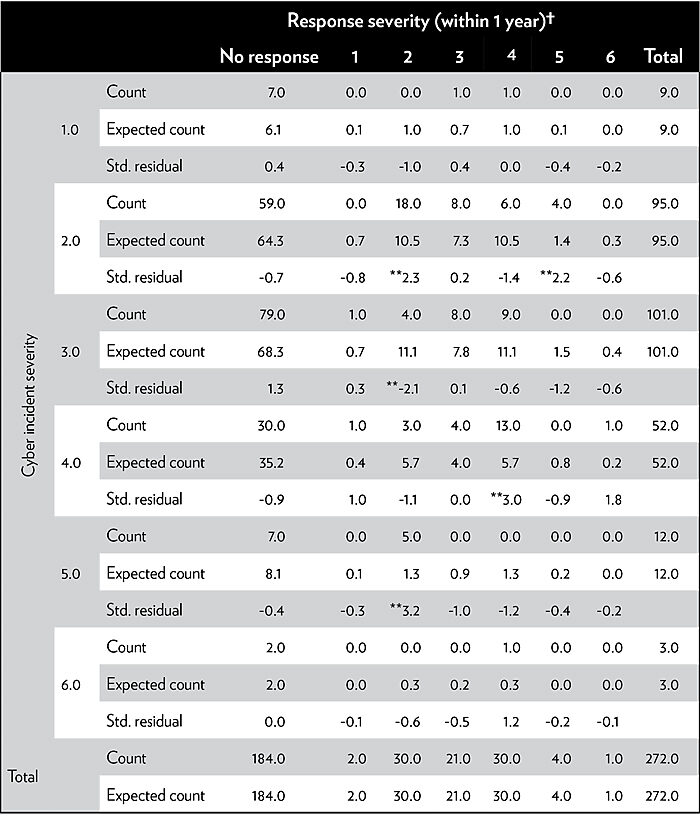
Sources: Dyadic Cyber Incidents Dataset version 1.5, maintained by the authors. See Ryan C. Maness, Brandon Valeriano, and Benjamin Jensen, “The Dyadic Cyber Incident and Dispute Dataset, Version 1.1,” 2017.
Notes: †There were no documented responses greater than 6. Scores of 7–10 imply national-level sustained damage and death. **Denotes column results that are statistically significant (p > .05).
Table 2
Cyber objectives and retaliation severity
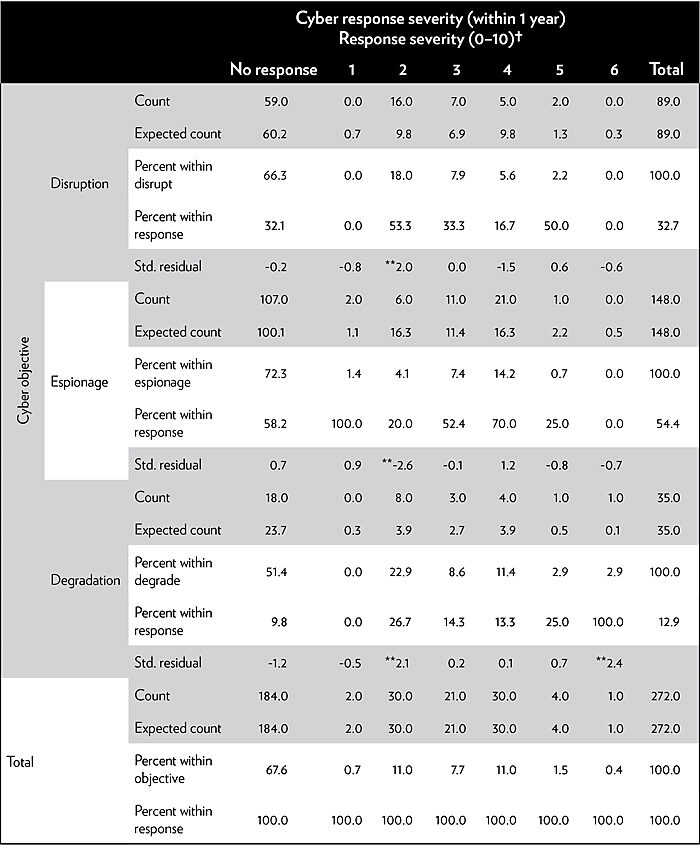
Sources: Dyadic Cyber Incidents Dataset version 1.5, maintained by the authors. See Ryan C. Maness, Brandon Valeriano, and Benjamin Jensen, “The Dyadic Cyber Incident and Dispute Dataset, Version 1.1,” 2017.
Notes: †There were no documented responses greater than 6. Scores of 7–10 imply national-level sustained damage and death. **Denotes column results that are statistically significant (p > .05).
No comments:
Post a Comment