Red faces in Red Square, again. Last July, I reported on the hacking of SyTech, an FSB (Federal Security Service) contractor working on internet surveillance tech. Now, reports have emerged from Russia of another shocking security breach within the FSB ecosystem. This one has exposed “a new weapon ordered by the security service,” one that can execute cyber attacks on the Internet of Things (IoT)—the millions of connected devices now in our homes and offices.
The goal of the so-called “Fronton Program” is to exploit IoT security vulnerabilities en masse—remember, these technologies are fundamentally less secure than other connected devices in homes and offices. In fact, one of the breached technical documents reported by BBC Russia even explains that “the Internet of Things is less secure than mobile devices and servers.” The security contractors highlight retained default “factory” passwords as the obvious weakness, one that is easy to exploit.
“Why is our own government spying on us through the IoT?” the hackers ask on Twitter. “In fact, spies on the whole world. How do they do it?” In an earlier tweet, they say “we can prove Kremlin henchmen crack our computers and spy on us.”
The intent of the program is not to access the owners of those devices, but rather to herd them together into a botnet that can be used to attack much larger targets—think major U.S. and European internet platforms, or the infrastructure within entire countries, such as those bordering Russia.
In the documents secured by the hacking group, the contractors say that “a powerful attack of several hundred thousand machines can make social networking sites, file hosting services inaccessible for several hours. An attack on national DNS servers can make the internet inaccessible for several hours in a small country.”
The contractors also cite Mirai—an IoT botnet that infected 600,000 devices. At its peak in October, 2016, “Mirai targeted the popular DNS provider DYN. This event prevented Internet users from accessing many popular websites, including AirBnB, Amazon, Github, HBO, Netflix, Paypal, Reddit, and Twitter.”
The breadcrumbs back to FSB are not hard to follow—the work order for one of the prototype weapons “was allegedly prepared by InformInvestGroup CJSC by order of military unit No. 64829, better known as the FSB Information Security Center.”
Targeted devices for the new exploits include cameras and NVRs, “if they transmit video,” the contractors explain, “they have a sufficiently large communication channel to effectively perform DDoS.” Clearly, the comprise of such devices in foreign countries by a nation-state agency carries other surveillance risks as well.
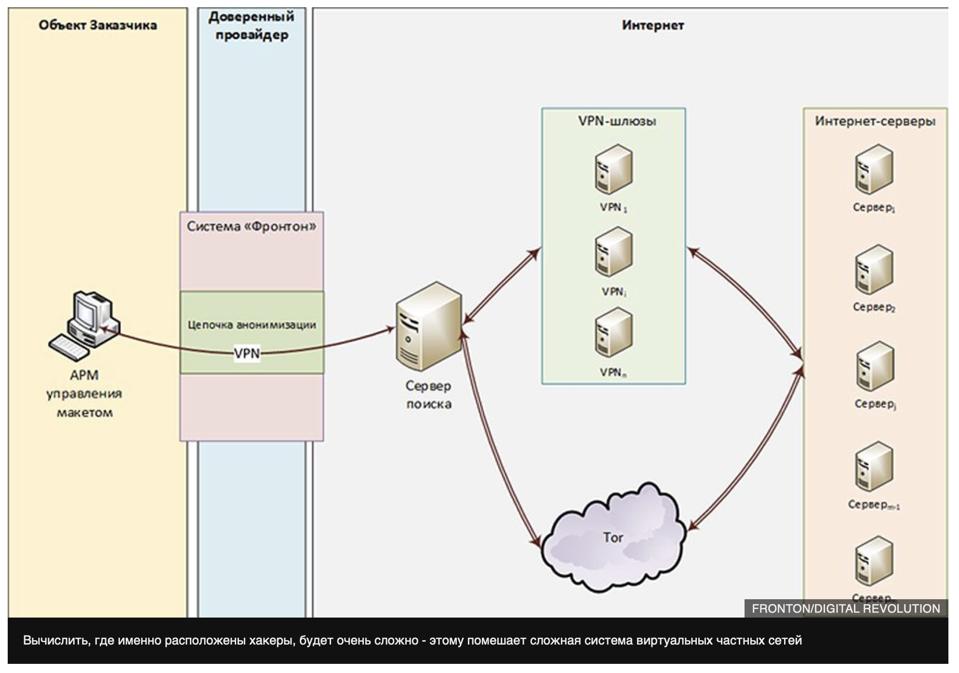
DIGITAL REVOLUTION / BBC RUSSIA
Digital Revolution published the 12 technical documents on March 18, documents which date back to 2017/18. The group has been the most persistent hacking threat to FSB. Last July, the smaller 0v1ru$ group breached contractor SyTech's servers and secured details of targeted collection tools—these were passed on to Digital revolution and shared. Prior to that, in late-2018, Digital Revolution breached the servers belonging to the Quantum Research Institute, an FSB supplier.
Stepping back from the specifics, there are countless warnings about the insecurity of IoT devices. These need to have regular firmwares updates and factory-set credentials reset before setup. There are also calls for network separation, gapping such devices from sensitive data at home—albeit that’s not the risk in this attack.
While many such attacks are out down to more generalist hackers and cyber criminals, it has been pointed out repeatedly that IoT devices now represent the easiest route into many enterprises. Hacking a printer, VoIP phone, network switch, smart appliance or insecure mobile device is much easier than attacking the network itself. IT departments worldwide are now scrabbling to assess the risk.
FSB’s remit stretches beyond domestic intelligence to cover overseas electronic collection, with intel oversight more broadly. It is the successor to the KGB and reports directly to Russia’s President Vladimir Putin. The fact that these kind of tools are being contracted out for development given the current geopolitical climate should give us all serious pause for thought.
FSB and Digital Revolution were approached for comments on this story.

No comments:
Post a Comment