 At least 500,000 aging routers, mostly located in Ukraine, have been infected with malware that experts believe could be used to turn them into a massive botnet capable of launching a major cyberattack aimed, in part, at disrupting power grids. On Wednesday, Cisco and Symantec both released details of malware called "VPN Filter," which they say has infected routers made by Linksys, Microtik, Netgear, QNAP and TP-Link in 54 countries, including the United States. The Daily Beast reports that the FBI on Tuesday obtained a court order instructing domain registrar Verisign to give the bureau control of a domain to which infected routers attempt to "phone home" for instructions.
At least 500,000 aging routers, mostly located in Ukraine, have been infected with malware that experts believe could be used to turn them into a massive botnet capable of launching a major cyberattack aimed, in part, at disrupting power grids. On Wednesday, Cisco and Symantec both released details of malware called "VPN Filter," which they say has infected routers made by Linksys, Microtik, Netgear, QNAP and TP-Link in 54 countries, including the United States. The Daily Beast reports that the FBI on Tuesday obtained a court order instructing domain registrar Verisign to give the bureau control of a domain to which infected routers attempt to "phone home" for instructions.
The FBI, which has reportedly been tracking the router malware since last August, on Wednesday seized control of the domain, enabling it to sinkhole the domain and at least partially block attackers' control of the infected routers, as well as to identify infected routers, The Daily Beast reports.
Security experts say the malicious components downloaded by the malware onto the router can be flushed by rebooting the router. But it remains to be seen how effective the FBI's sinkholing of the control domain will be at containing any malicious use of the router botnet. It's also unclear if the FBI and other law enforcement agencies might be able to convince users of infected routers to update or retire them.
Attacker: Fancy Bear
According to an affidavit obtained by The Daily Beast, the FBI says it's connected the mass router compromise to the hacking group known as "Fancy Bear," aka APT28, Pawn Storm, Sednit, Sofacy and Tsar Team.
The group, which many security experts believe is tied to the Kremlin, has also been tied to attacks against the Democratic National Committee and Hilary Clinton's 2016 presidential campaign as well as the U.S. Senate and this year's Olympic Winter Games, among many other targets (see Analysis: VPN Fail Reveals 'Guccifer 2.0' is 'Fancy Bear').
The FBI couldn't be immediately reached for comment.
Teardown: VPN Filter
All of the routers infected with VPN Filter appear to be aging models, which experts have long warned are at high risk of being compromised by attackers if they have not been updated with the latest security fixes - and had any default passwords changed - or if vendors have stopped shipping updates for the devices. The potential fallout from this type of scenario was demonstrated by the fast-moving Mirai malware outbreak that began in 2016 (see The Next IoT Botnet Has Improved on Mirai).
Cisco's Talos intelligence unit published technical information on VPN Filter on Wednesday, saying that even though it had yet to complete its investigation into the malware, the "scale and capability" of the campaign prompted it to release details so organizations could take immediate defensive steps.
"The malware has a destructive capability that can render an infected device unusable, which can be triggered on individual victim machines or en masse."
—Cisco
The VPN Filter malware is multifunction, capable of stealing login credentials, monitoring network traffic flows, including Modbus, a common serial communications protocol for industrial control systems, Cisco writes. VPN Filter can also intentionally brick routers.
"The malware has a destructive capability that can render an infected device unusable, which can be triggered on individual victim machines or en masse, and has the potential of cutting off internet access for hundreds of thousands of victims worldwide," Cisco says.
In its report, Cisco - as is common for security researchers - doesn't attempt to name the likely developer of the malware. But it does say that it believes that a state-sponsored or state-affiliated actor is behind the malicious code. Some of VPN Filter's code is also similar to BlackEnergy, a type of malware that was used in attacks against critical infrastructure in Ukraine. The malware has been tied to an APT group known as Sandworm, which many security experts believe is tied to Fancy Bear.
Ukraine: Malware Testing Ground
Ukraine has been on the knife's edge of some of the world's most aggressive cyberattacks. Experts have long suspected Russia has used Ukraine as a guinea pig for offensive cyber operations.
In 2015 and 2016, cyberattacks on Ukraine energy providers caused blackouts. In June 2017, attackers seeded malicious software inside a software update for accounting software developed in Ukraine called MeDoc (see Police in Ukraine Blame Russia for NotPetya).
The malware, called NotPetya, purported to be ransomware, but appeared more geared to simply locking up systems for good. The infections started in Ukraine, but rapidly spread around the world, causing hundreds of millions of dollars in damages to multiple companies, including shipping giant Maersk, FedEx's TNT Express unit and the German company Beiersdorf.
Ukraine's security services, the SBU, warned on Wednesday of a possible "large-scale cyberattack" just ahead of the Champions League soccer final scheduled for this Sunday in Kiev. The SBU says it believes Russia may be to blame for the infections as part of a campaign to disrupt the sporting event.
In mid-April, the U.S. and U.K issued an unprecedented warning that Russia has undertaken a methodical campaign to undermine infrastructure across the internet, including compromising routers, switches, firewalls and network intrusion devices (see US, UK: Russian Hackers Deeply Embedded in Routers, Switches).
No Zero Days
Cisco says it's not sure how the routers initially become infected. But the company suspects that attacks are not using so-called zero-day vulnerabilities, which refers to unknown flaws for which there are no software fixes.
The routers affected include those made by Linksys, Netgear, Mikrotik, TP-Link and Q-Nap devices. All of the routers models have well-known vulnerabilities, Cisco says.
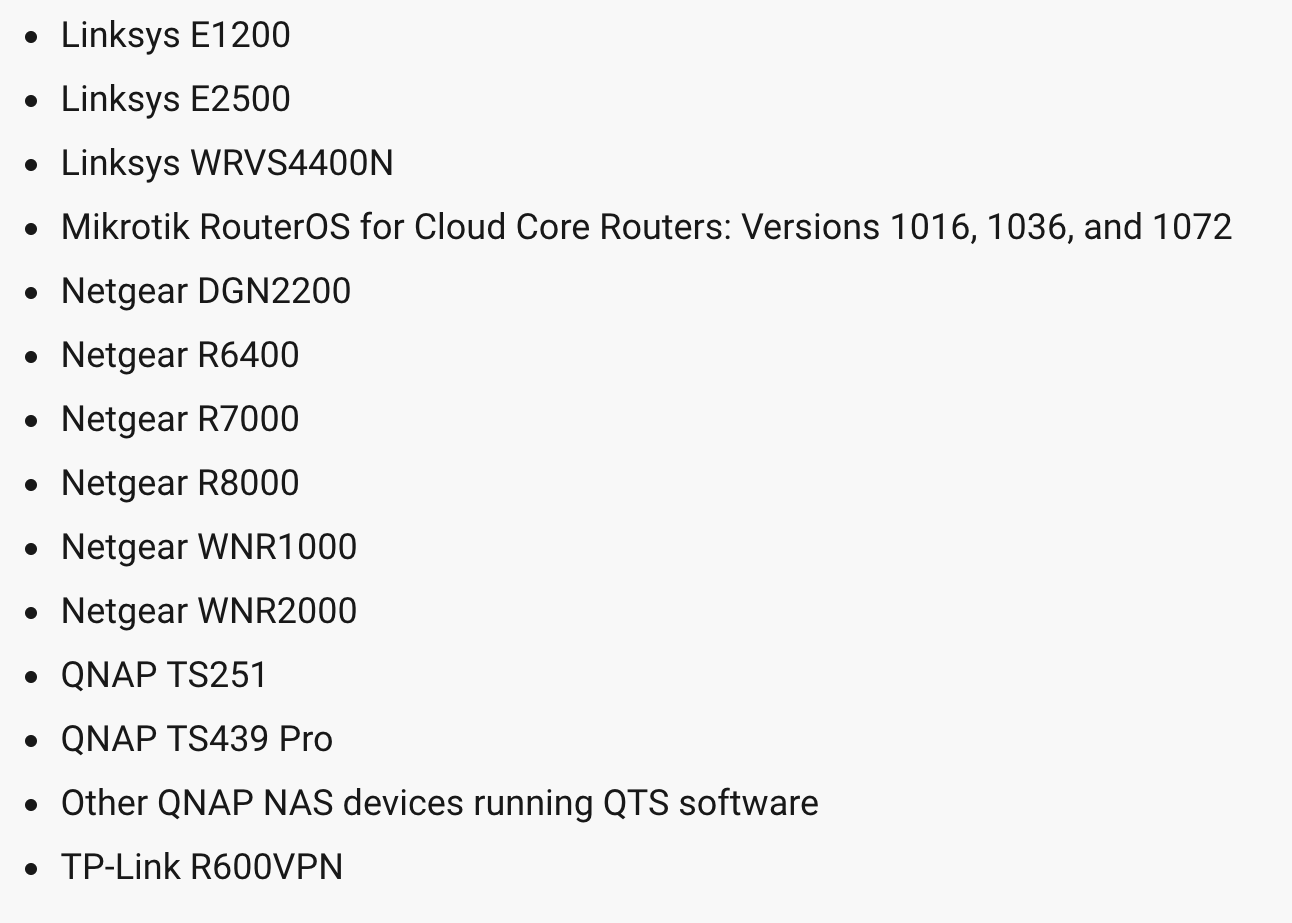 Routers vulnerable to VPNFilter. (Source: Symantec)
Routers vulnerable to VPNFilter. (Source: Symantec)
Defending against the attacks is "extremely difficult," Cisco says. The routers are directly connected to the internet, which is how attackers have been able to locate them.
Although there are patches for some of the well-known flaws, as with many IoT devices, applying the patches isn't convenient. Also, none of the devices have built-in anti-malware capabilities.
Ukraine's SBU also says it has been able to "neutralize" some of hidden infrastructure used by attackers, "but we emphasize that without the elimination of end-user vulnerabilities, it is impossible to prevent new waves of similar cyber attacks."
The first stage of VPN Filter's infection establishes a foothold on the device, infecting firmware based on BusyBox and Linux, Cisco says. Unfortunately, simply rebooting the router won't eliminate the first stage.
VPN Filter "is capable of modifying non-volatile configuration memory (NVRAM) values and adds itself to crontab, the Linux job scheduler, to achieve persistence," Cisco says. "This is a departure from previous IoT malware, like Mirai, which is ephemeral and disappears with a simple device reboot."
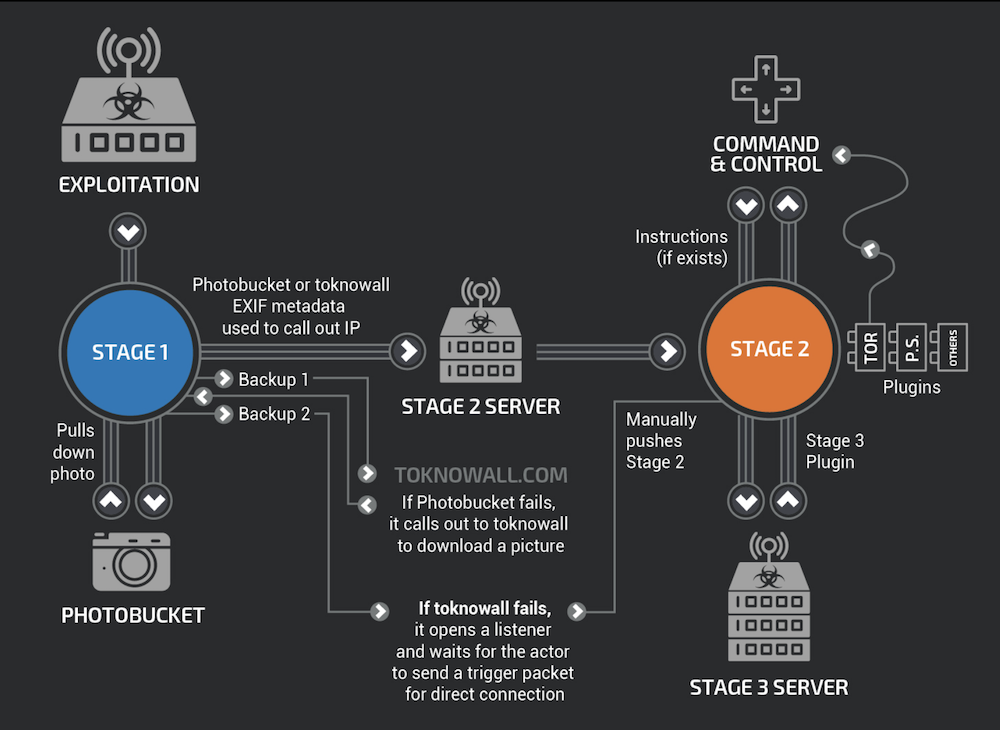
A diagram by Cisco of VPN Filter's network activity. (Source: Cisco)
Once the foothold is established, VPN Filter tries to download other modules in two other stages, including a packet sniffer, a Tor plugin, an attack against an industrial control system protocol, and other management capabilities. The second and third stage will, however, disappear on reboot, Cisco says.
But the problem is then that the first stage can reinstall the second and third stages again, according to an advisory from Symantec.
The malware is programmed to load images on the photo-sharing site Photobucket.com that have instructions hidden in their metadata, and if that fails, to visit ToKnowAll.com as a backup, researchers say. But with the Photobucket images having been removed and the bureau having seized control of the latter domain, rebooted routers will no longer be able to receive attack payloads. Of course, that still leaves routers that have yet to be rebooted, which may still be vulnerable to being used by attackers.
Vulnerable Routers: What To Do
At least four router manufacturers have issued guidance on how to deal with VPN Filter.
Netgear says the remote management feature should be disabled and the default administrator password changed.
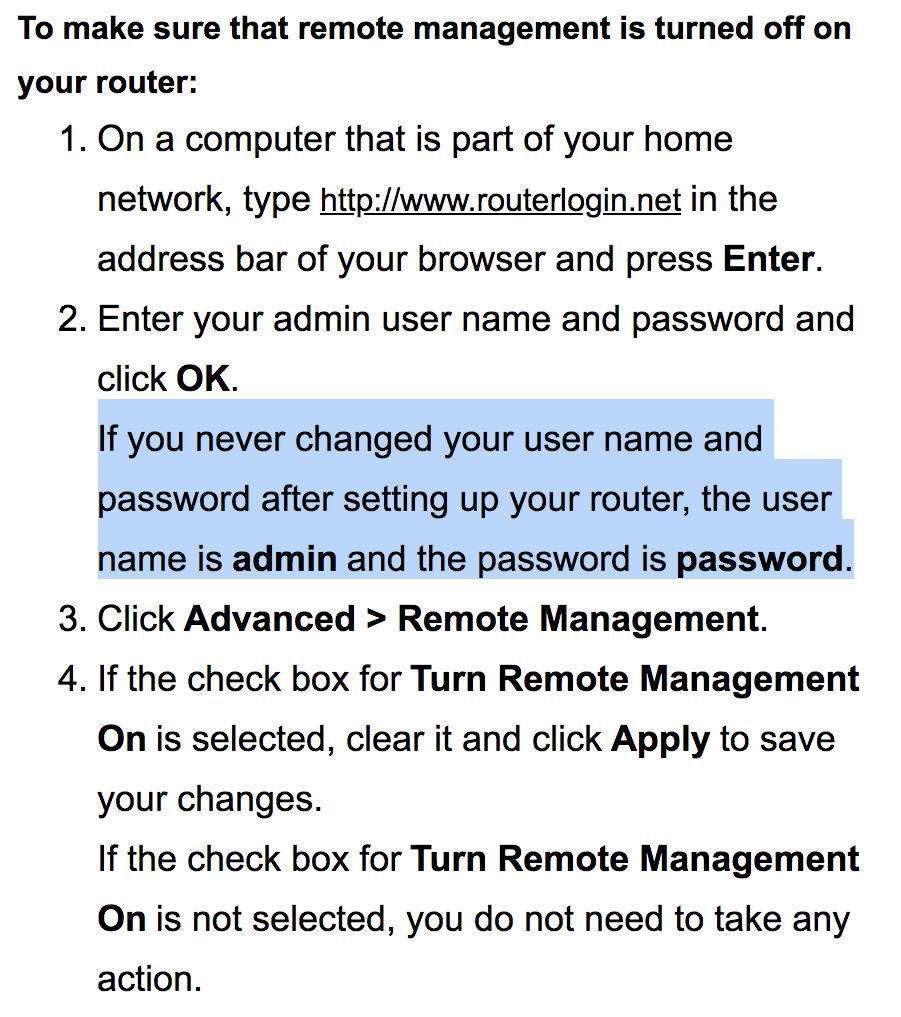 Netgear's advice on countering VPN Filter. (Source: Netgear)
Netgear's advice on countering VPN Filter. (Source: Netgear)
Failing to change a router's default credentials is a widespread concern. Networking manufacturers often now ship routers that have a preset, complicated password or force users to reset the credentials. That can make it more difficult for an attacker to gain remote access to the device and compromise it.
Unfortunately, not all router manufacturers appear to have tightened their default settings. In particular, Netgear routers affected by VPN Filter have default credentials for accessing the router's internal settings: "admin" and "password."
TP-Link devices appear to have the same problem. "TP-Link strongly encourages users of its products to keep their devices updated with the latest firmware to protect against threats and ensure their product is up to date," the company says. "In addition to updating product firmware, users should also make sure that they change the default admin password for their devices."
Linksys says in a statement that its newer routers, such as its mesh and EA/WRT lines, include automatic software downloads and force default password changes, so they are not affected by VPN Filter. But older models will need to have their firmware updated to safeguard them against the malware. Any router already infected by the malware will also need a factory reset, Linksys says.
Mikrotik, which is based in Latvia, says it is "highly certain" that the malware exploits a vulnerability in its RouterOS software that was patched in March 2017. "Simply upgrading RouterOS software deletes the malware, any other third-party files and closes the vulnerability," the company says.
Officials at QNAP couldn't be immediately reached for comment.
Executive Editor Mathew Schwartz also contributed to this report.
No comments:
Post a Comment