
Evil flower in South Asia, lure of beauty, ghost war elephants roaming the Himalayas … To many people, these fantastic code names could only be heard in thrilling hacker movies.
It turns out that they are real groups from India with possible intelligence background and state support. Investigations conducted by several of China's leading cybersecurity companies have revealed a sophisticated network: they have constantly attacked defense and military units as well as state-owned enterprises in China, Nepal and Pakistan over the past few years, and such attacks are on the rise under new disguises of international trendy topics.
These groups are normally known as Advanced Persistent Threat (APT) organizations made up of hackers with government support which focuses on persistent network attacks against specific targets. APT organizations are spread in the world, with many having been active in attacks against key infrastructure and government departments for years.
Chinese cybersecurity analysts and diplomatic relations observers often mention that the next world war will be fought not on the ground, or in the air or under water, but virtually in the cyberspace.
China has been victims of cyberattacks for many years and the rising attacks from India once again revealed the severity of the situation and the urgency to speed up building of a cybersecurity safeguard system.
Cyberattacks from South Asian regions, mainly India, target China's key industries. Graphic: Feng Qingyin/GT
Accurate attacks with varying tactics
India is a country that might be overlooked as a threat by the world intelligence community. Even other countries in South Asia may not be fully aware of its advanced cyber capabilities.
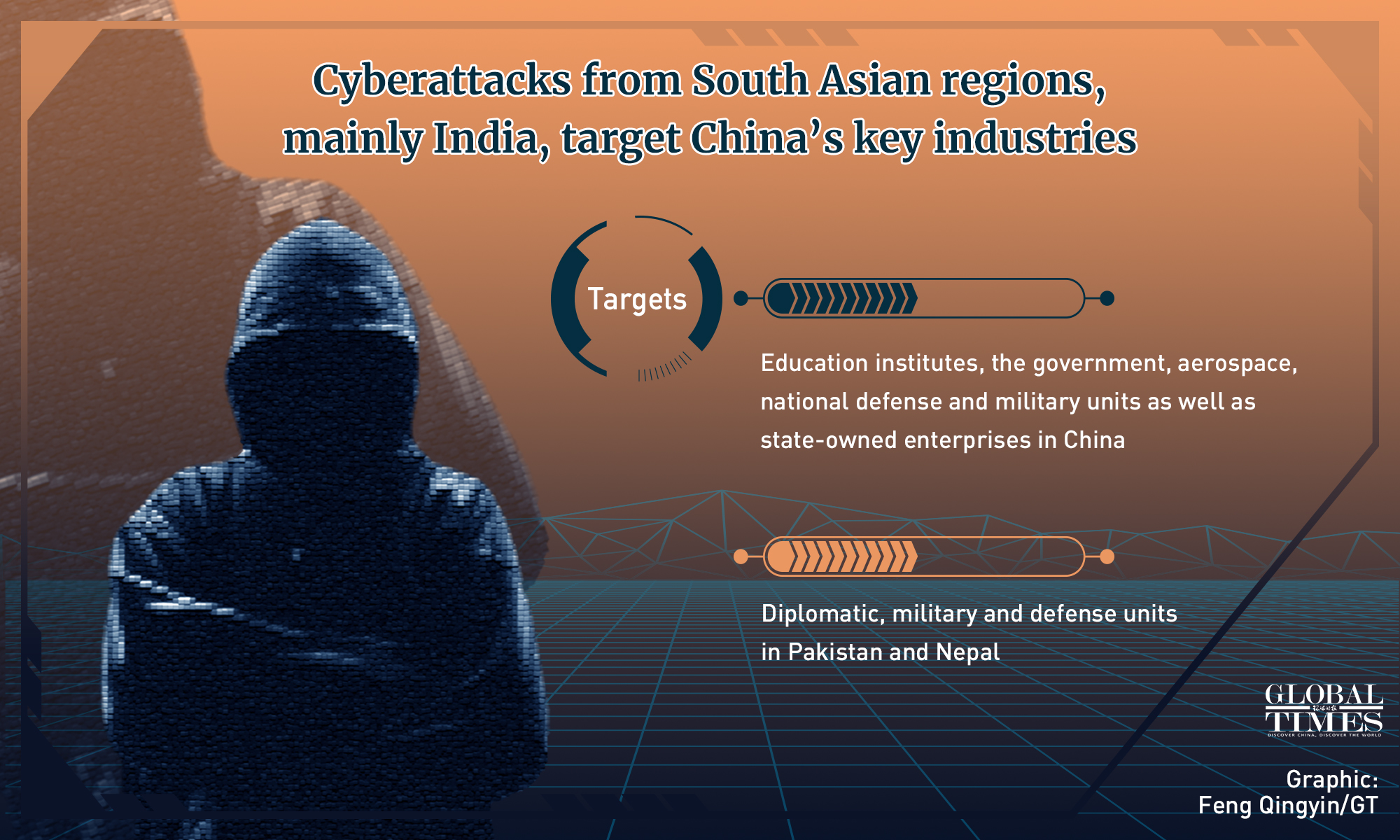
"Since March, we have detected several phishing activities targeting government, defense and military units, as well as state-owned enterprises in China, Pakistan, and Nepal," Antiy Labs, one of China's renowned cybersecurity companies, said in a statement sent to the Global Times.
The organization behind the attacks is from India and its activities can be traced back to as early as April 2019. So far, more than 100 phishing counterfeit websites created by the organization have been detected by Antiy Labs.
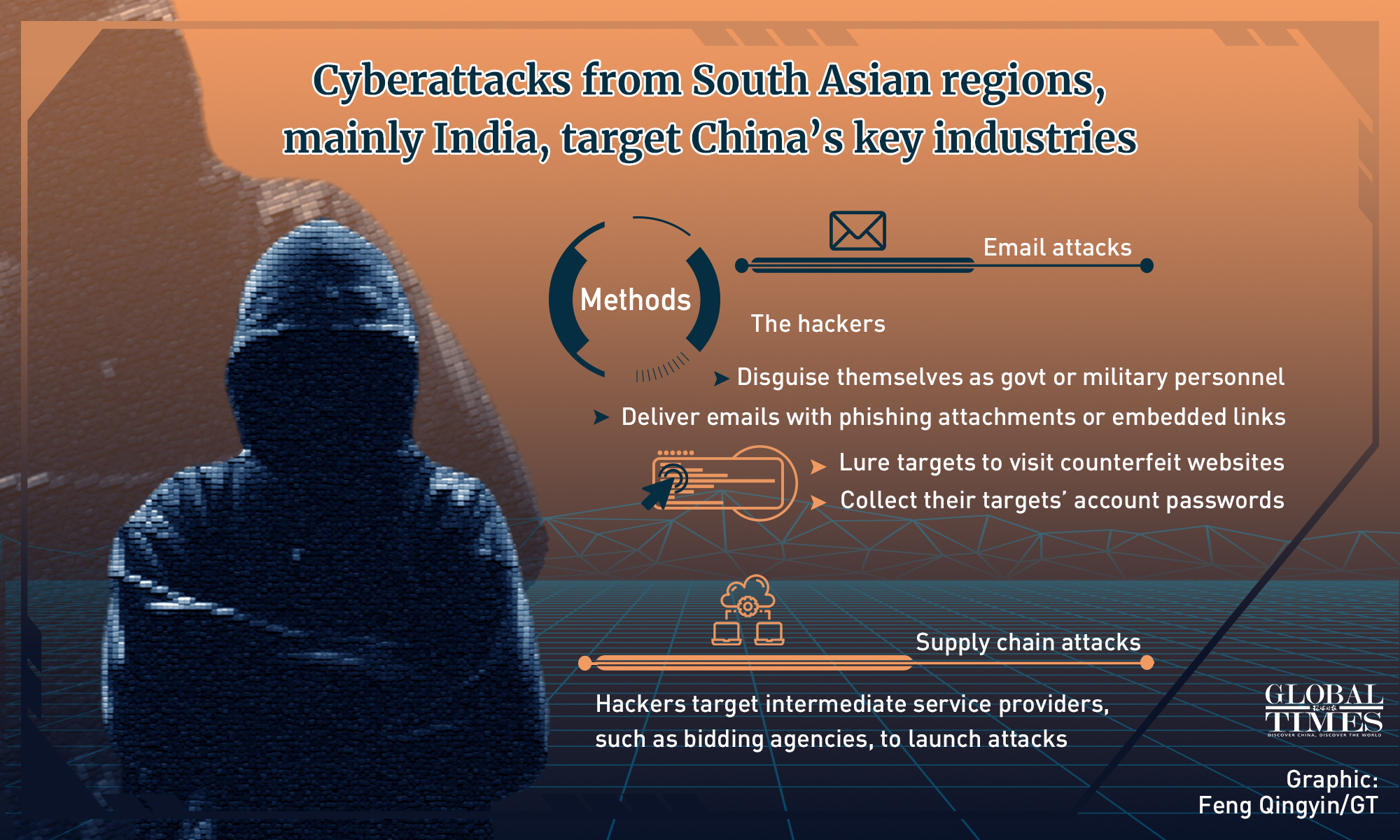
The company's vice chief engineer, Li Bosong, told the Global Times that the organization has been known to target Chinese government departments through spear-phishing, that is when the hackers disguise themselves as government or military personnel and deliver emails with phishing attachments or embedded links to targets, luring them to visit the websites created by them and collecting the account password for intelligence gathering.
When a phishing website is used, it will first show a message like "restricted" or "updating e-mail system." Then, the website will pop up a window asking to log in to the email account again. When this is done, the user will be switched to the fake email login site that the hackers have created, Li explained.
Chinese tech giant 360 Security Technology also told the Global Times that hackers from India have been caught actively launching cyberattacks targeting multiple organizations and individuals in China in the past two years. In 2020, the company monitored and captured more than 100 of initial payloads mostly from India and they induced users to execute malicious payloads through harpoon emails in various fields.
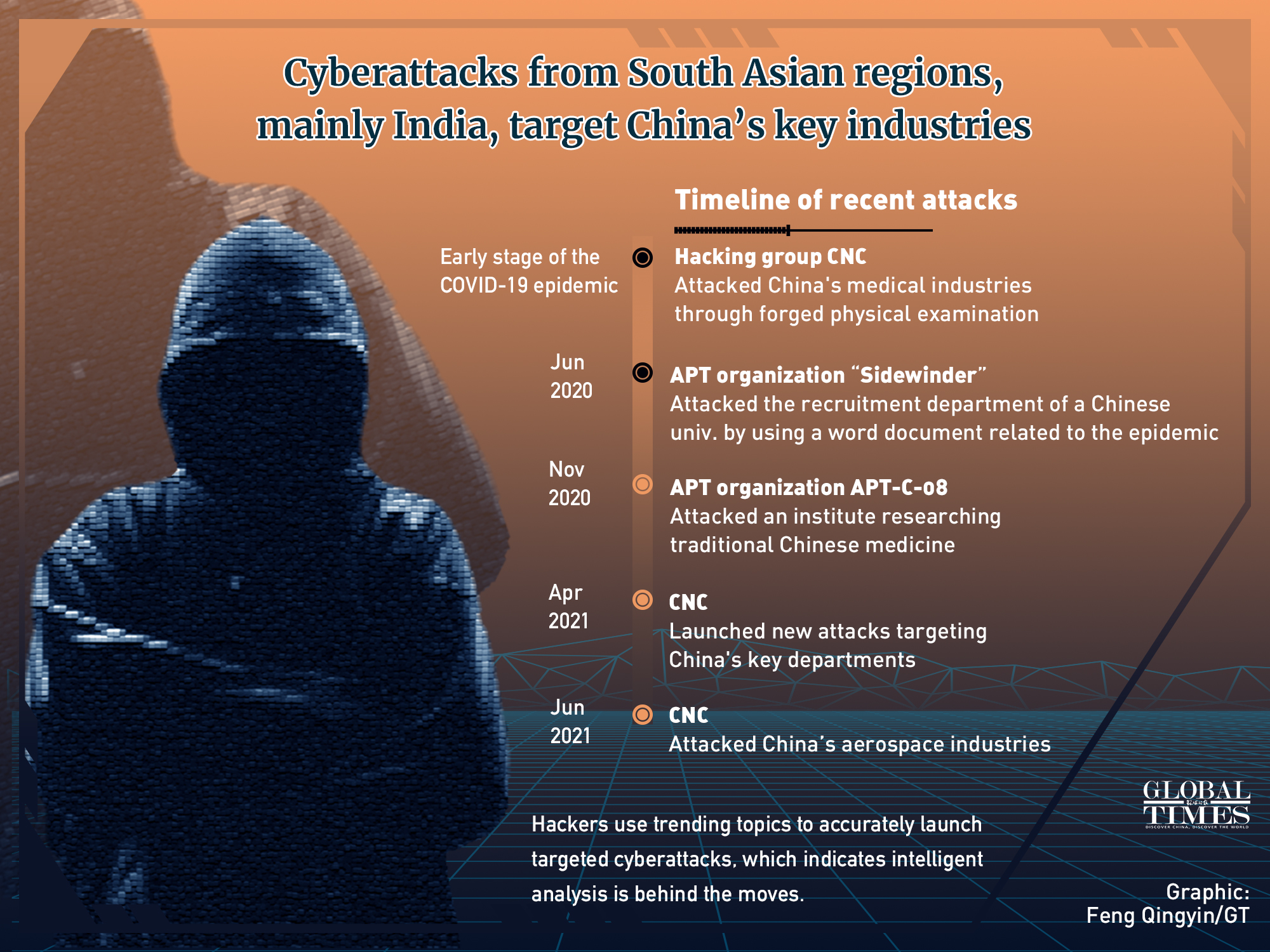
Their attacks were largely on the rise in the first half of 2021, targeting education, government, aerospace and defense industries in many fields. Those attacks were especially aimed at organizations or individuals mentioned in online trending topics on politics and economy, the pandemic situation and industrial activities, the company said.

Photo: CFP
Cybersecurity analysts from the company believe that an intelligence organization is likely behind such accurate hacks.
For example, in the early stage of the COVID-19 pandemic, 360 Security Technology busted the hacking group CNC (APT-C-48) which launched attacks on China's medical institutes through forged physical examination forms taking advantage of the COVID-19 outbreaks in China. In April this year, the CNC launched fresh attacks targeting aerospace industries in the midst of China's space events in June.
Other heated topics like cross-Straits tensions, China's cruise missile capabilities and the Doklam standoff were also used as baits for their attacks against Chinese military agencies, think tanks, universities and research institutions.
Apart from spear-phishing attack, APT organizations are also good at "watering hole" attacks, which target users by infecting websites that they commonly visit. Sometimes, a simple attack delivering a known malware can be enough to get hackers what they want.
In November 2020, an APT organization known as Evil Flower in South Asia launched an attack against a research institute on traditional Chinese medicine, a cybersecurity insider told the Global Times. "The organization has been active since early November 2013, but remained undetected until 2016, when it was first revealed by a foreign cybersecurity vendor."
Evil Flower has a strong political background, mainly targeting Pakistan and China. In 2018, its activities against Saudi Arabia were revealed, targeting government departments, power generation and military industries with the intention of stealing sensitive data. In 2019, it also strengthened the attacks on China's import and export enterprises, the insider said.
Cyberattacks from South Asian regions, mainly India, target China's key industries. Graphic: Feng Qingyin/GT
Cyberattacks from South Asian regions, mainly India, target China's key industries. Graphic: Feng Qingyin/GT
Cybersecurity is national security
Attacks from India highlighted how cybersecurity risks have mushroomed along with the rapid development of China's internet sector. Over the years, China has been a major victim of cyberattacks and the web has become a new weapon from the US and its allies against China and Russia in the information war.
According to the annual report from the National Computer Network Emergency Response Technical Team/Coordination Center of China (CNCERT/CC), in 2020 about 5.31 million hosts on the Chinese mainland were controlled by a total of about 52,000 overseas malicious program command and control servers, and the top three origins of overseas servers in terms of the number of compromised Chinese hosts are all from NATO member states.
"Previously, we had a misunderstanding that China was a developing country with less valuable internet information which was not worthy to be stolen. However, China is now the world's second largest economy, so the world's superpowers and even China's neighboring countries would see China now as a strong opponent and thus launch national cyberattacks. Such attacks will be persistent and will evolve along with the changes of international geopolitics," Shen Yi, deputy director of the Fudan University Cyberspace Research Center, told the Global Times on Thursday.
Just as Chinese President Xi Jinping said at a meeting early in 2014 that "internet security and informatization is a major strategic issue concerning a country's security and development as well as people's life and work," the cyberattacks from India have taught us the lesson that cybersecurity is the lifeline of national security, Shen said.
Xi's speech in 2014 served as a milestone in creating a national strategy for China's cybersecurity and informatization.
Although China has dedicated efforts to maintaining good relations with India, the South Asian country inherited Western geopolitical ideas and principles from its suzerain when it was a British colony. India conducted numerous cooperation with the US in cybersecurity and it is reasonable to speculate that behind the hacker groups there is intelligence sharing between India and the US, Shen said.
It is urgent for China to enhance its defense and deterrence capabilities in cybersecurity with a system that should be iterative, with data flowing across borders, while achieving effective dynamic defense based on threat hunting, Shen said.
China should set routine examinations and drills system in organizations to find and solve problems, rather than roughly penalizing them, Shen explained.
Moreover, a notification mechanism is also required to report attacks at government departments and enterprises, Shen noted, adding that "the US is good at issuing reports describing explicitly the whole process of the attacks to blame China. Similar reports should be published by research institutions and companies in China as an effective countermeasure."
Qin An, head of the Beijing-based Institute of China Cyberspace Strategy, believes India's constant harassment and challenges in cyberspace are in line with the US Indo-Pacific Strategy.
"Whether the attacks are floods or sewage and wherever the water came from India or the US, China should improve its defense system by cultivating more experts and professional teams," Qin said.
New challenges, ranging from rogue programs to security loopholes, have also pushed the government to roll out a slew of legal measures to build a cybersecurity governance system.
Since 2017, China has been building, almost from scratch, legal mechanisms to safeguard cybersecurity.
In June, China passed its Data Security Law, which is seen as a crucial move to develop a broad strategy that will provide support to the country's enterprises to increase their spending on data security.
In July, China's Ministry of Industry and Information Technology released a draft of a three-year cybersecurity plan, the most detailed strategy for the development of China's cybersecurity industry, which would mandate that key industries such as telecommunications devote 10 percent of their budget to cybersecurity by 2023.
No comments:
Post a Comment