Michael Martelle
The central questions of this thesis are whether Russian cyber capabilities reflect an investment in offensive or defensive cyber weapons and whether Russia's cyber technology, doctrine, and policy indicate an offensive or defensive cyber posture. The discussion of Russian cyber capability includes several case studies of Russian cyber activity.
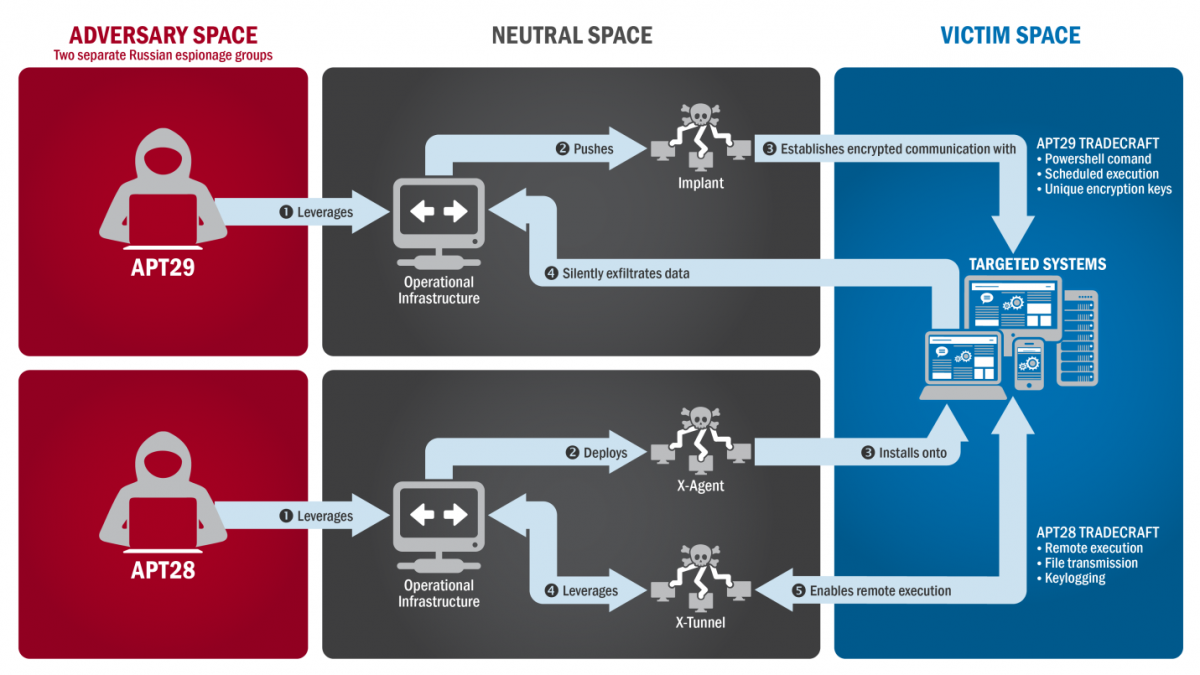
This report presents the information that the U.S. government is willing to make public concerning the "the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints associated with the U.S. election, as well as a range of U.S. Government, political, and private sectors entities."
In their joint statement, the DNI, Under Secretary Defense for Intelligence, and the Director of NSA/Commander, U.S. Cyber Command, discuss a variety of consequences of cyber threats - physical, commercial, psychological consequences - on cyber policy, diplomacy, and warfare. In addition, the statement discusses a number of cyber threat actors - nation states (Russia, China, North Korea, Iran), terrorists, and criminals - and responses to cyber threats.
This report is a greatly expanded version of the GRIZZLY STEPPE analysis released in late December 2016, and focuses on the use of the Cyber Kill Chain model (whose components are reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on the objective) to analyze malicious cyber activity.
This paper examines both the theoretical and practical underpinnings of the Russian approach to cyber warfare. It contains chapters on cyber as a subcomponent of information warfare, organizations and agencies, hacktivists and criminals, three case studies of Russian cyber operations (Estonia in 2007, Georgia in 2008, and the Ukraine from 2013 to the present), and chapters on bots, leaks, and trolls.
In his testimony before the Senate Select Committee on Intelligence, Sarts presents case-study research conducted at the NATO Strategic Communications Centre of Excellence on the tools used by Russia in conducting influence operations and Western responses before making a series of policy recommendations.
One section of this study addresses Russian cyber activities, including cyber-enabled psychological operations (including the use of hacktivists, trolls, and bots) and information defense.
This document indicts 12 Russian intelligence officers for operations against Democratic Congressional Campaign Committee computer networks to interfere in the 2016 election.
No comments:
Post a Comment