SYDNEY J. FREEDBERG JR.

WASHINGTON — As Russian ground troops started massing along the border with Ukraine in 2021, Russian hackers began laying the foundation for their own unprecedented cyber onslaught not just against Kyiv, but the Western nations supporting the embattled Eastern European country. The digital campaign went into overdrive alongside the physical invasion — but in more recent months, Moscow seems unable to keep up the pace, at least for now.
According to a new report by Mandiant, a cybersecurity firm now part of Google Cloud, the spring and fall of 2021 saw dramatic spikes in phishing attempts. That’s a common preliminary stage of hacking, using deceptive emails, links, and websites to trick legitimate users into divulging their login information, which then opens the door for follow-on attacks.
During the next year, when Russia invaded Ukraine, Russian phishing attempts against Ukraine rose 250 percent, while Russian phishing against NATO countries increased over 300 percent, compared to a 2020 baseline. Within Ukraine, the campaign targeted more than 150 government entities, with those in the ministry of defense as the number one target.
And though the report says Moscow appears to have backed off its cyber operations lately, it isn’t over.
“We assess with high confidence that Russian government-backed attackers will continue to conduct attacks against Ukraine and NATO partners to further Russian strategic objectives,” the report says.
The campaign Mandiant analyzed includes a global phishing operation in September-October 2021 by a group Mandiant calls Frozenlake but others refer to as the notorious Fancybear. Backed by the Russian military intelligence agency, the GRU, this organization is most famous in the US for purportedly hacking the Democratic National Committee ahead of the 2016 elections. Overall, Mandiant credits Frozenlake/Fancybear with over 77 percent of “government-backed attack activity targeting users in NATO countries,” with an allied Belarusian group called Pushcha coming in a distant second with 15.5 percent.
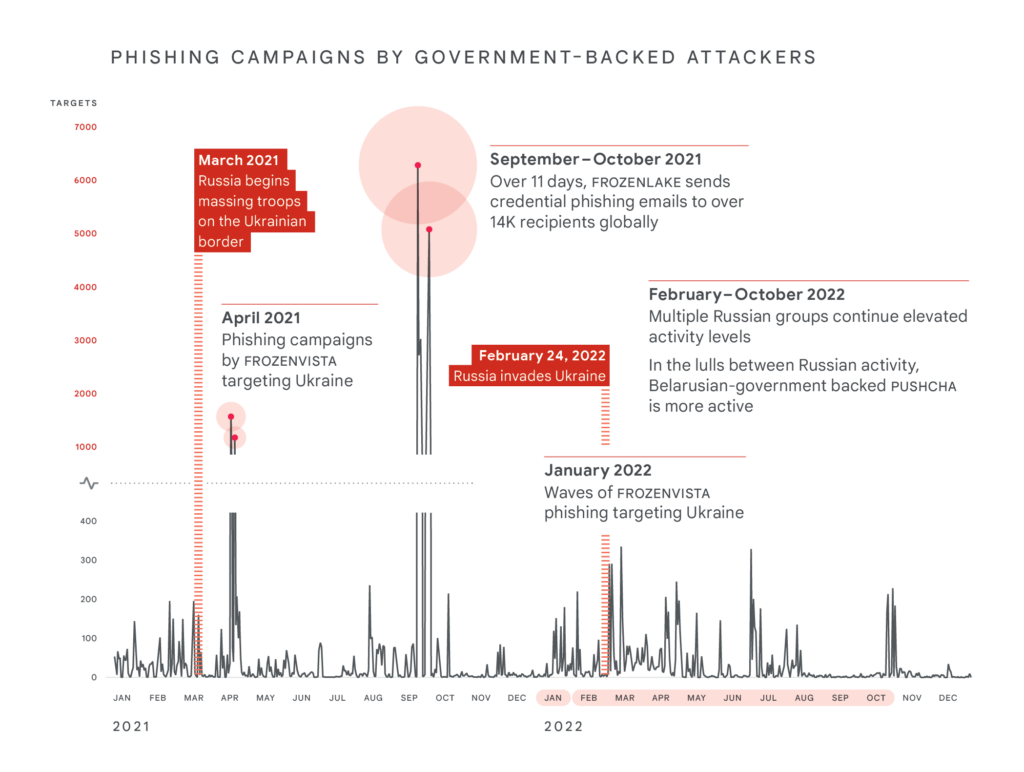
Russian phishing attempts against Ukraine, 2021-2022. (Mandiant graphic)
Since the invasion kicked off, some observers have been confounded by the apparent lack of success Russia’s once-feared cyber squads have had in taking Ukraine offline. More recently officials noted that the attacks were happening, but Ukraine, with a lot of Western help, had managed to mainly fend them off.
But the report says that, building on the access gained by phishing attempts and other cyber reconnaissance, Russia conducted “more destructive cyber attacks” — using “wipers” trying to erase Ukrainian data — in the first four months of 2022 than in the previous eight years.
“The beginning of the invasion was really rough, in that the wipers were very aggressive and there were a lot of them,” said Luke McNamara, principal analyst for Mandiant, in an email to Breaking Defense. “With the initial invasion not being successful, we saw a short pause in wipers, but there was still plenty of on-going espionage and probing cyber activity occurring.”
“We still see wipers from time to time,” he noted, “but not like in the beginning of the physical invasion.”
Both such destructive attacks and the preparatory phishing have fallen off since early 2022, albeit with occasional surges. Overall, Mandiant reports, “the pace of attacks slowed and appeared less coordinated than the initial wave in February 2022.”
Mandiant’s analysis suggests Russia may have expended a lot of stockpiled cyber ammunition early in the war. Hackers can lurk undetected in a network for months or years, quietly stealing data, but once they unleash destructive malware, visibly disrupting operations, it becomes obvious that someone has unauthorized access to the system, and cybersecurity specialists can often lock them out.
“To conduct the initial waves of destructive activity, Russian actors often employed accesses gained months before, which were often lost as the attack was remediated,” Mandiant reports. In the following months, the report goes on, “destructive attacks often occurred more quickly after the attacker gained or regained access.” In other words, before the invasion, the Russians had time to infiltrate a network and lurk a while before trying to take it down; after, they would often gain access and attack almost immediately, in effect burning their bridges as fast as they built them.
This “willingness to prioritize destructive attacks at the cost of persistent access” for intelligence-gathering, Mandiant concludes, indicates the importance Russia places on disrupting Ukrainian networks — or, they add, simply bad planning.
Yet Russia has also showed a certain restraint in its recent cyber attacks, Mandiant suggests. In 2017, for example, the Russian Notpetya attack spread far beyond Ukraine, most likely by mistake, paralyzing global shipping company Maersk and doing billions of damage worldwide. In February 2022, Russian hackers disrupted the Viasat broadband network, crippling communications not only in Ukraine — that is, until Elon Musk’s Starlink stepped in — but also across Europe. Since then, however, Mandiant reports, “we’ve seen little evidence of a spillover effect outside Ukraine.”
It seems Russia hasn’t even used malware to attack the Ukrainian power grid, as it did in 2017 with the Industroyer/Crashoverride virus that briefly blacked out part of Kyiv. This isn’t because Russia lacks the expertise, McNamara said. “Russia definitely has the capability and intent to create [physically] destructive attacks — as evidenced with INDUSTROYER.v2 — should they choose to, but they have not done so.”
Instead, Russia resorted to real-world attacks, expending much of its missile arsenal against Ukrainian infrastructure, seeking to destroy it permanently rather than disrupt it temporarily with a hack. That shows, in McNamara’s estimation, some limits of cyber warfare.
“Cyber tools are often best used for espionage because in the kinetic war, conventional means are going to have most of the destructive impacts,” he said.
No comments:
Post a Comment