Joe Tidy
When Russia initiated its full-scale invasion of Ukraine, a second, less visible battle in cyberspace got under way. The BBC's cyber correspondent Joe Tidy travelled to Ukraine to speak to those fighting the cyber war, and found the conflict has blurred the lines between those working for the military and the unofficial activist hackers.
When I went to visit Oleksandr in his one-bedroom flat in central Ukraine, I found a typically spartan set-up common to many hackers.
No furniture or home comforts - not even a TV - just a powerful computer in one corner of his bedroom and a powerful music system in the other.
From here, Oleksandr has helped temporarily disable hundreds of Russian websites, disrupted services at dozens of banks and defaced websites with pro-Ukraine messages.
He is one of the most prominent hackers in the vigilante group, the IT Army of Ukraine - a volunteer hacking network with a Telegram group nearly 200,000-strong.
For more than a year, he has devoted himself to causing as much chaos in Russia as possible.
Even during our visit he was running complex software attempting to take his latest target - a Russian banking website - offline.
Ironically though, he admits the idea for his favourite hack actually began with a tip from an anonymous Russian, who told them about an organisation called Chestny Znak - Russia's only product authentication system.
He was told all goods produced in Russia - including fresh food - have to be scanned for a unique number and a barcode supplied by the company from the moment of their creation at a factory, up till the moment of being sold.
Oleksandr smiles as he describes how he and his team found a way to take the service offline, using a hacking tool that floods a computer system with internet traffic - known as a targeted DDoS (Distributed Denial-of-Service) attack.
"The economic losses were pretty high, I think. It was mind-blowing," says Oleksandr.
 IMAGE SOURCE,AFPImage caption,
IMAGE SOURCE,AFPImage caption,Oleksandr says he is not scared of Russian reprisals and refuses to hide his identity
In reality, it's hard to gauge the disruption prompted by the hack, but for four days last April Chestny Znak posted regular updates about the DDoS attack on its official Telegram feed. Traders were offered advice and a helpline to call for assistance.
Eventually Russia's Ministry of Industry and Trade was forced to relax some rules on food labelling to allow perishables to be traded.
More recently, around the first anniversary of the invasion, Oleksandr joined a team of hackers, called One Fist, to hijack Russian radio stations and broadcast the sound of fake air raid sirens and an alert message telling citizens to take shelter.
"We feel ourselves like military," says Oleksandr. "When my country calls me to pick up a rifle I am ready, but hacking Russia now, I feel that I am helpful."
Many experts predicted that people like Oleksandr - hacktivists - might play a part in the Ukraine conflict, but the scale of the activity has come as a shock - with hacker armies emerging on both sides.
Officially Ukraine is defending itself from cyber attacks, aided by Western cyber military teams and private cyber-security companies - funded by millions of dollars in donations.
But unofficial links are also beginning to emerge between vigilante groups going on the offensive and carrying out criminal attacks and military officials.
On both sides, lines between targeted, state-sanctioned cyber-attacks and ad-hoc vigilante hacking have been blurred. The consequences could be far-reaching.
On a visit to Ukraine's cyber defence HQ in Kyiv, officials claim they have evidence that the Russian hacktivist gang, Killnet, which has a Telegram group of nearly 100,000, is working directly with the cyber section of the Russian military.
"These groups, like Killnet or the Cyber Army of Russia, started off carrying out DDoS attacks - but have since recruited more talented and skilled people," says Viktor Zhora, deputy chairman of the State Service of Special Communications.
He alleges the groups have consultants from the Russian military and are now capable of launching sophisticated cyber attacks.
Russian commanders are uniting all of the hacktivist groups and activities into a single source of aggression in cyber-space against Ukraine and its allies, he claims.
The link would be problematic for Russia if proven.
Since the invasion, Russia has been relatively targeted in its cyber attacks - sticking to Ukrainian targets that are loosely linked to the war effort.
But Killnet has called for and carried out disruptive - albeit temporary - attacks on hospital websites in both Ukraine and allied countries.
 Image caption,
Image caption,A masked Killmilk - Killnet's leader - sent a video, responding to the BBC's questions
The Geneva Convention, rules aimed to limit the savagery of physical wars, prohibit such attacks on civilians. But there's no Geneva Convention for cyber warfare. The International Committee of the Red Cross argues that existing codes should apply - so targeting hospitals, for example, would constitute a breach.
The fact that hacker attacks are being carried out on Nato countries could also trigger a collective response if they caused serious harm.
The Russian government did not respond to requests for comment from the BBC - so instead, we went directly to Killnet's leader, who goes by the moniker Killmilk.
Killmilk refused to take part in a face-to-face interview, but after weeks of messages on Telegram he sent video responses to our questions - before breaking off communication.
In his recordings, Killmilk boasts that the hackers devote 12 hours a day to Killnet. "I see no equal in the world to Russian hackers. Useless and stupid Ukrainian hackers cannot succeed in confronting us," he says.
Killmilk insisted his group is completely independent of Russian special services, asserting that he has a regular job as a factory loader and is "a simple person".
Before the war and Killnet, he says he started a criminal DDoS-for-hire business - but, when the invasion began, he was determined to dedicate his hacking efforts to disrupting Ukraine and its allies.
"Wherever I am, my laptop and everything I need is always with me. In this, I am mobile and efficient and devote almost all my time to our movement."
 Image caption,
Image caption,Killmilk posts dramatic videos to his group's Telegram account in order to rally support
Whilst some hactivist vigilante groups, like the infamous Anonymous collective, have slowed down activities against Russia and moved on in the past three months, Killnet has increased its activity and is also focussing on the West - urged on by bombastic videos from Killmilk which show him urinating on flags representing Nato and the US.
Over the Easter weekend, Killnet's Telegram channel was used to create a pop-up team called KillNATO Psychos. Within hours, it was hundreds of members-strong and proceeded to carry out a wave of attacks which temporarily disrupted Nato member websites. The group also published a list of Nato staff email addresses and encouraged people to harass them.
The allegation that Russian cyber military is working with criminal hacktivists will not come as a shock for many in the cyber-security world, which for years has accused Russia of harbouring some of the most prolific and profitable cyber-crime groups.
However our visit to Ukraine confirmed that lines are blurring there too.
A year ago, as the capital Kyiv braced for attack, Roman was helping carry out criminal hacks and building software for the war effort - as part of a volunteer group he co-founded called IT Stand for Ukraine.
But now, he has officially been recruited by his country's cyber military.
 Image caption,
Image caption,Vigilante-turned-soldier Roman thinks cyber plays a huge part in the war effort
We met in a park near his training headquarters in the city of Zhytomyr, two hours west of Kyiv.
As a vigilante-turned-military man, Roman has a unique perspective.
He chose not to go into details about his current role, but says part of his job is finding ways to comb through piles of data and leaked information from the cyber war.
Even before he was recruited, Roman confirms his hacking team worked directly with Ukrainian authorities.
"We started to communicate with state forces doing the same as us and we began kind of synchronising our operations. They basically started to give us some targets and say what to do, when to do," he says.
Roman says one of the most impactful attacks was when his team disabled ticket machines for a southern Russian railway network.
When challenged about the disruption this would have caused everyday people in Russia, Roman shrugs.
It's the kind of attack that Ukraine's cyber military could never publicly carry out themselves.
Since the start of the full-scale invasion, Ukraine has been at pains to present itself as the defender, not the attacker.
Could Ukrainian cyber commanders be using vigilantes to stretch the front line of the conflict into the Russian state?
 IMAGE SOURCE,MIKHAILO FEDOROVImage caption,
IMAGE SOURCE,MIKHAILO FEDOROVImage caption,Mykhailo Fedorov says cyber-attacks by vigilantes are justified
Mykhailo Fedorov, Ukraine's deputy prime minister and minister for digital transformation, is responsible for the department which controversially set up the Telegram group for Oleksandr's IT Army of Ukraine.
Since then, the government claims to have had no involvement in the hacktivist network.
Mr Fedorov denies accusations he is encouraging offensive attacks against Russian civilian targets.
But he said he is confident that Ukraine has the "moral right to do everything it can to protect the lives of our citizens".
"I think that in a year of the full-scale war, Ukrainian hackers have shown that, despite such an invasion, they operate ethically enough - and do not cause excessive damage to any subjects besides the ones of the Russian Federation that are involved in the war," he says.
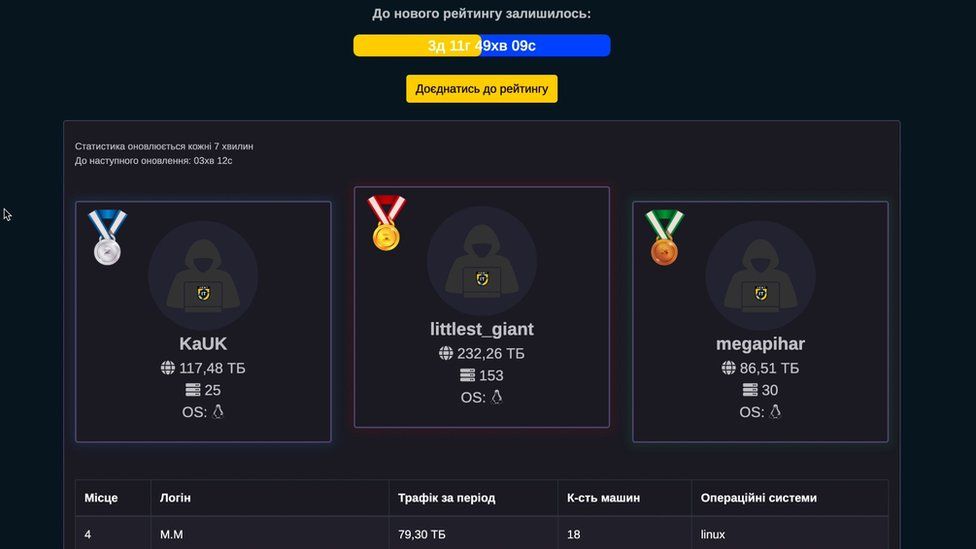 IMAGE SOURCE,AFPImage caption,
IMAGE SOURCE,AFPImage caption,The IT Army of Ukraine has a hacker leader board, suggesting the gamification of illegal hacking
But Ukrainian hacktivists are not just hacking the Russian war machine.
Despite the Ukrainian army not condoning the targetting of institutions like healthcare, hacks are being organised to cause as much disruption as possible to the Russian people.
One of the co-ordinators of the IT Army of Ukraine, Ted, proudly showed us his collection of angry comments from ordinary Russian customers who have experienced disruption as a result of their activities.
His website includes a hacker leaderboard - I ask whether his group could be "gamifying" criminal hacking - and whether this created a danger of escalation.
"Talking from the standpoint of Western laws, I think, yes, there is a danger of gamification of illegal hacking. But what we need to realise is that when war is coming to your country, there are no good ways or bad ways to fight."
Some predict the severity of attacks will increase from Russia as it struggles on the physical battlefield.
Ukrainian officials say the worst attacks are not coming from hacktivists, but from the Russian military, which is co-ordinating cyber attacks with physical attacks on targets such as energy grids.
Back at Ukraine's cyber defence HQ, Mr Zhora says Russia has so far failed to deliver the kind of cyber attacks that experts feared - but that's not due to lack of effort - and their attacks would be more disruptive if Ukraine was weaker.
Some sources have also told me that Ukraine has been worse affected by Russian hackers than its commanders are admitting.
As with all aspects of war, the fog of war is hard to penetrate and that's especially true in cyber-space.
Additional reporting by producer Peter Ball
No comments:
Post a Comment